Application program vulnerability detection method and device
An application program and vulnerability detection technology, applied in computer security devices, instruments, computing, etc., can solve problems such as low efficiency of vulnerability detection schemes and incomplete detection results, and achieve the effect of solving incomplete and comprehensive detection results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0024] According to an embodiment of the present invention, a method embodiment of a vulnerability detection method for an application program is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be implemented in a computer system such as a set of computer-executable instructions and, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
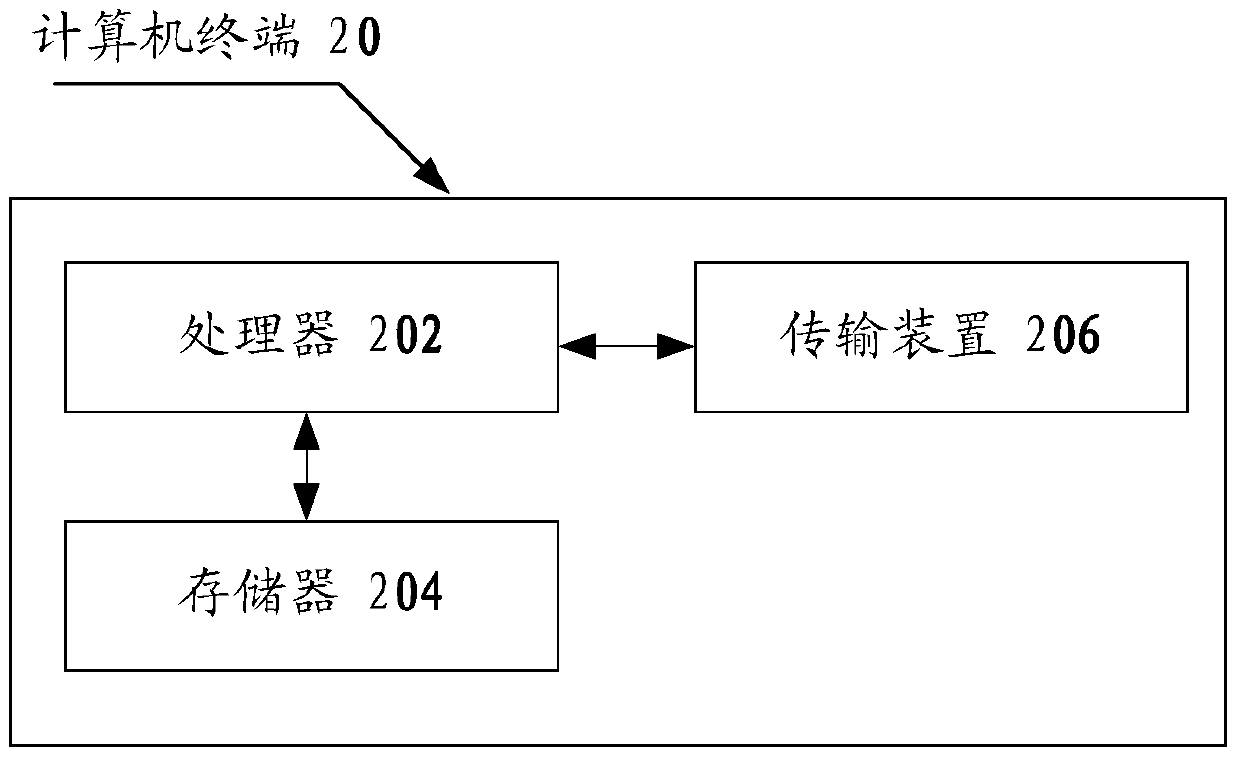
[0025] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, figure 2 It is a block diagram of the hardware structure of a computer terminal used to implement the application program vulnerability detection method according to the embodiment of the present invention. Such as figure 2 As shown, the computer t...
Embodiment 2
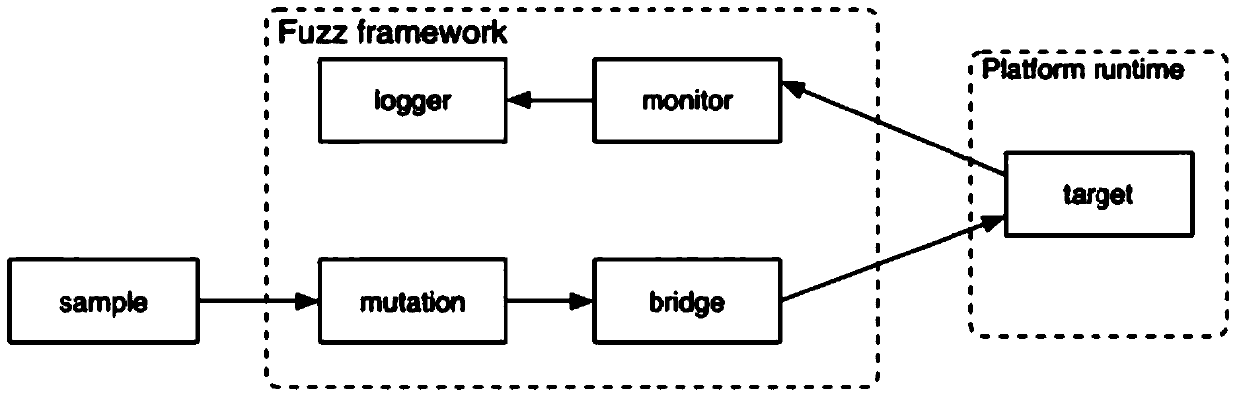
[0075] This embodiment is described by taking the detection of DOS vulnerabilities of applications based on the Android operating system as an example. However, it should be noted that the solution in this embodiment is not limited to application detection of the Android operating system, nor is it limited to DOS vulnerabilities. The main design idea of this embodiment is to filter out specific APIs through official documents (that is, open source documents), and use this as the basis for detecting DOS vulnerabilities, that is, for open source operating systems, according to the behavior of the system API described in open source documents To find specific APIs of interest, based on these APIs combined with some other methods to achieve specific functions (such as DOS vulnerability detection in this embodiment). It mainly includes the following processes: 1. Generate CFG (Controll Flow Graph) based on static code; 2. Prune through static analysis to filter out API branches th...
Embodiment 3
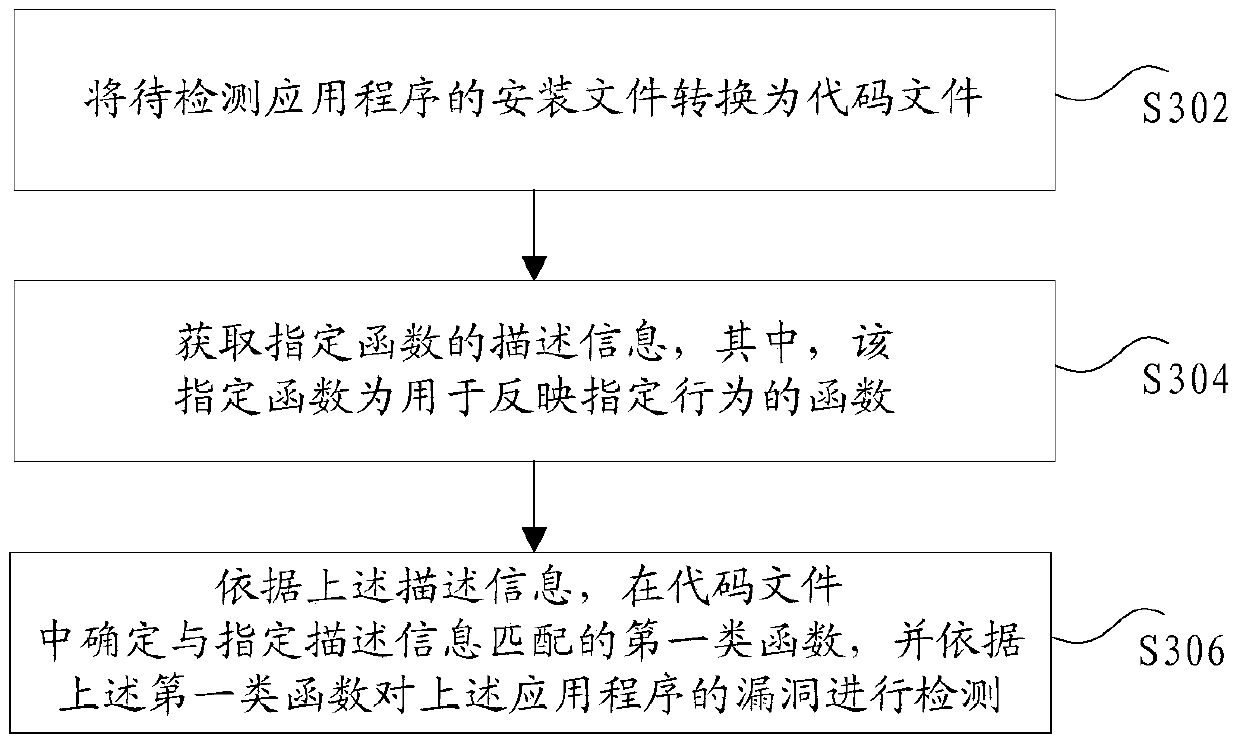
[0087] According to an embodiment of the present invention, there is also provided a vulnerability detection device for an application program implementing the above method, which can run in the mobile terminal, computer terminal or similar computing device described in Embodiment 1, but does not It is limited to the function or structure of the above-mentioned computing device in Embodiment 1. Such as Figure 7 As shown, the device includes:
[0088] The conversion module 70 is configured to convert the installation file of the application program to be detected into a code file. The functions realized by this module can be realized through solutions in related technologies. For example, for the installation package file of an Android application, the installation package (Android Package, APK for short) file of the application can be converted into smali code by APKTool , but not limited to this implementation.
[0089] The obtaining module 72 is connected to the conversi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com