Vulnerability detection method and device
A vulnerability detection and vulnerability technology, applied in the computer field, can solve problems such as low vulnerability detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
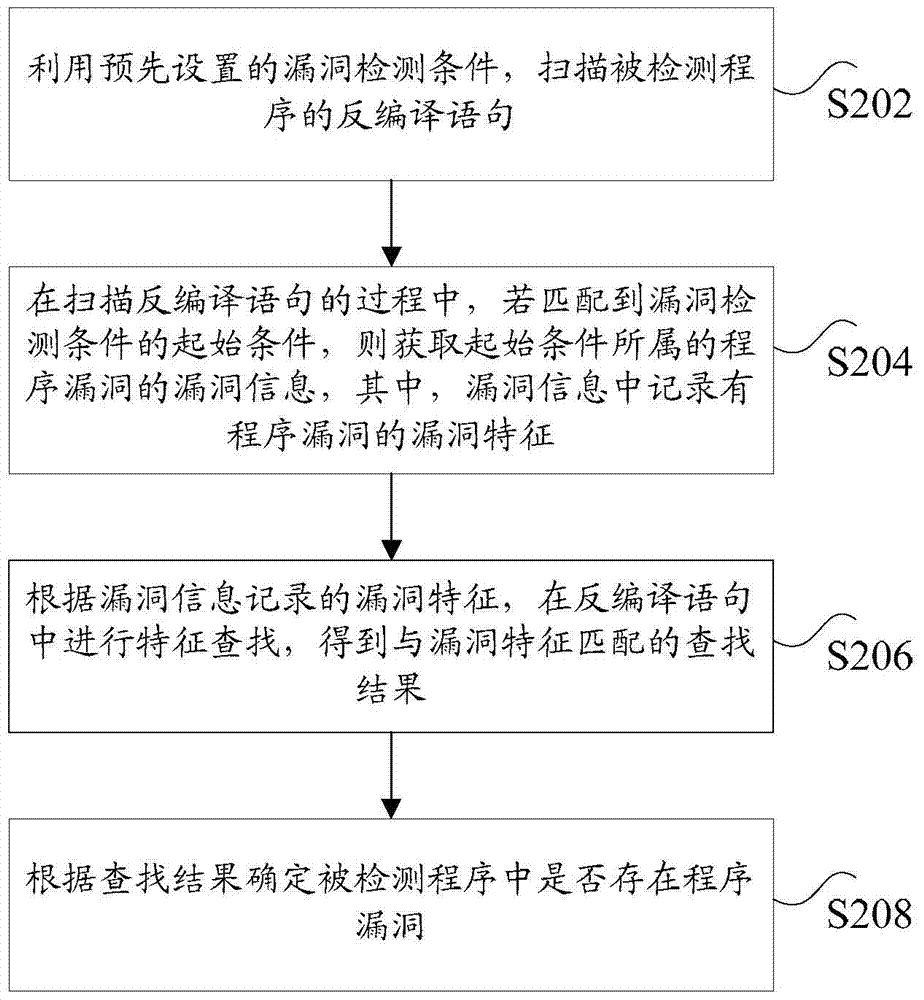
[0032] According to the embodiment of the present application, an embodiment of a vulnerability detection method is provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, although A logical order is shown in the flowcharts, but in some cases the steps shown or described may be performed in an order different from that shown or described herein.
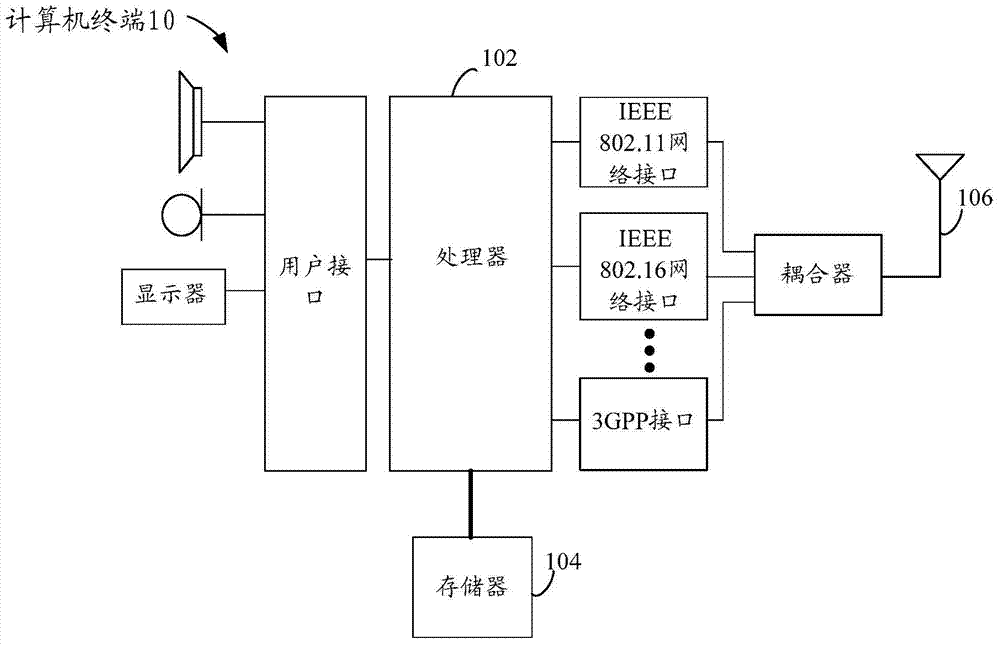
[0033] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, figure 1 It is a block diagram of the hardware structure of a computer terminal of a vulnerability detection method in the embodiment of the present application. Such as figure 1 As shown, the computer terminal 10 may include one or more (only one is shown in the figure) processors ...
Embodiment 2
[0104] According to an embodiment of the present application, a vulnerability detection device for implementing the above vulnerability detection method is also provided, such as Figure 7 As shown, the apparatus may include: a scanning unit 701 , a first acquiring unit 703 , a searching unit 705 and a determining unit 707 .
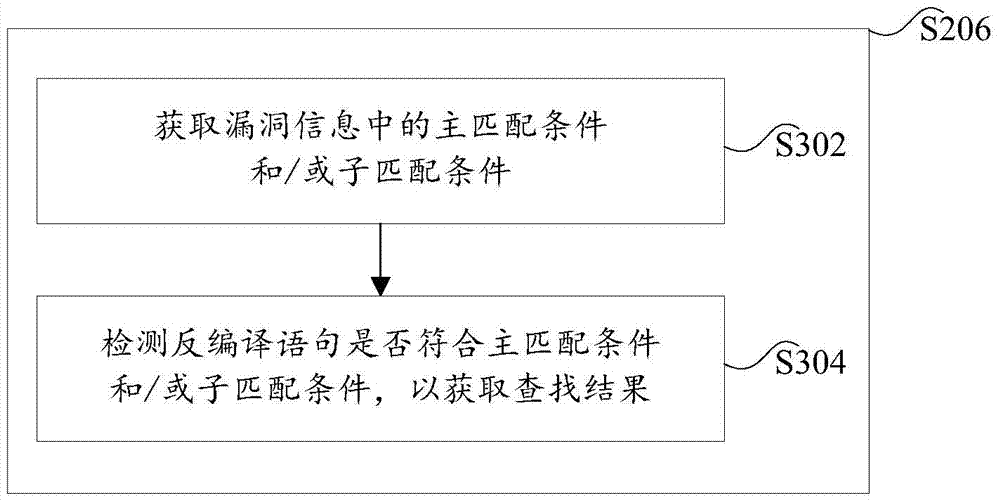
[0105] Among them, the scanning unit 701 is used to scan the decompiled statement of the detected program by using the pre-set vulnerability detection condition; initial condition, then obtain the vulnerability information of the program vulnerability to which the initial condition belongs, wherein, the vulnerability characteristics of the program vulnerability are recorded in the vulnerability information; the search unit 705 is used to perform feature extraction in the decompiled statement according to the vulnerability characteristics recorded in the vulnerability information Searching to obtain a search result that matches the vulnerability feature; ...
Embodiment 3
[0125] Embodiments of the present application may provide a computer terminal, and the computer terminal may be any computer terminal device in a group of computer terminals. Optionally, in this embodiment, the foregoing computer terminal may also be replaced with a terminal device such as a mobile terminal.
[0126] Optionally, in this embodiment, the foregoing computer terminal may be located in at least one network device among multiple network devices of the computer network.
[0127] In this embodiment, the above-mentioned computer terminal can execute the program code of the following steps in the vulnerability detection method of the application program: use the pre-set vulnerability detection conditions to scan the decompiled statement of the detected program; in the process of scanning the decompiled statement, If the initial condition of the vulnerability detection condition is matched, the vulnerability information of the program vulnerability to which the initial c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com