Dynamic secret key protection method and system
A technology of dynamic secret key and protection system, which is applied in transmission system, digital transmission system and key distribution, which can solve problems such as doubts about the security of transmission secret key, and achieve the effect of strengthening protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
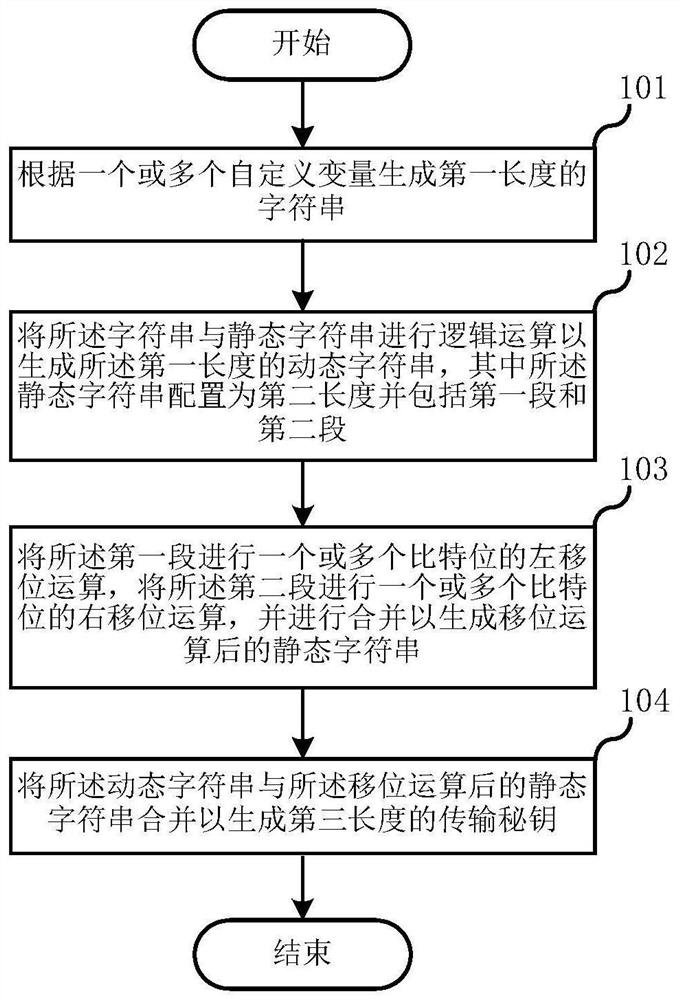
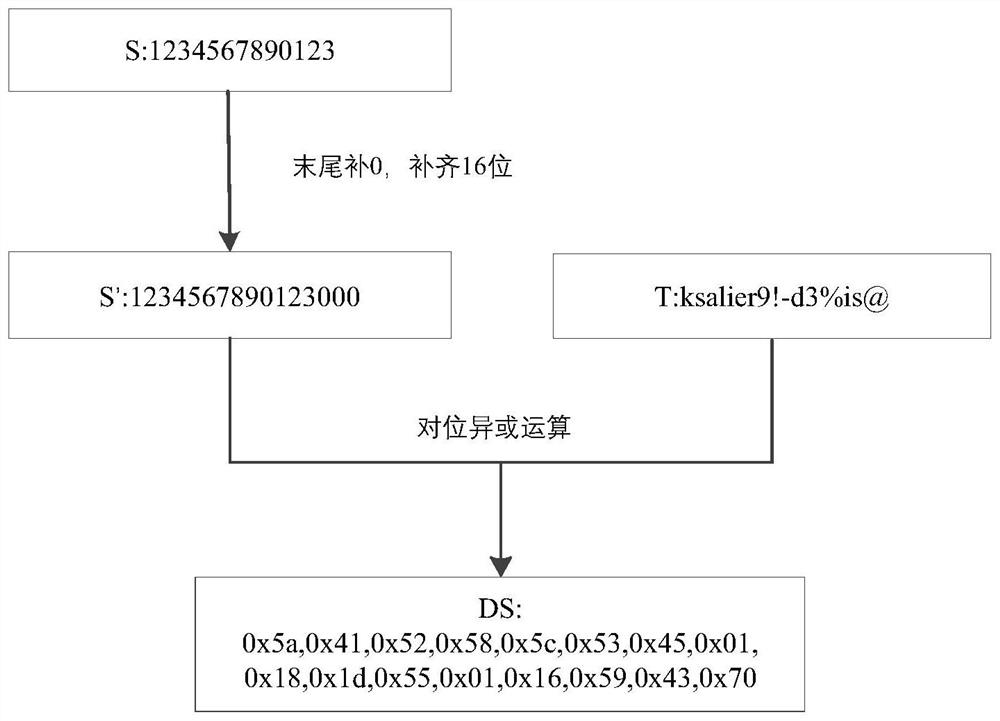
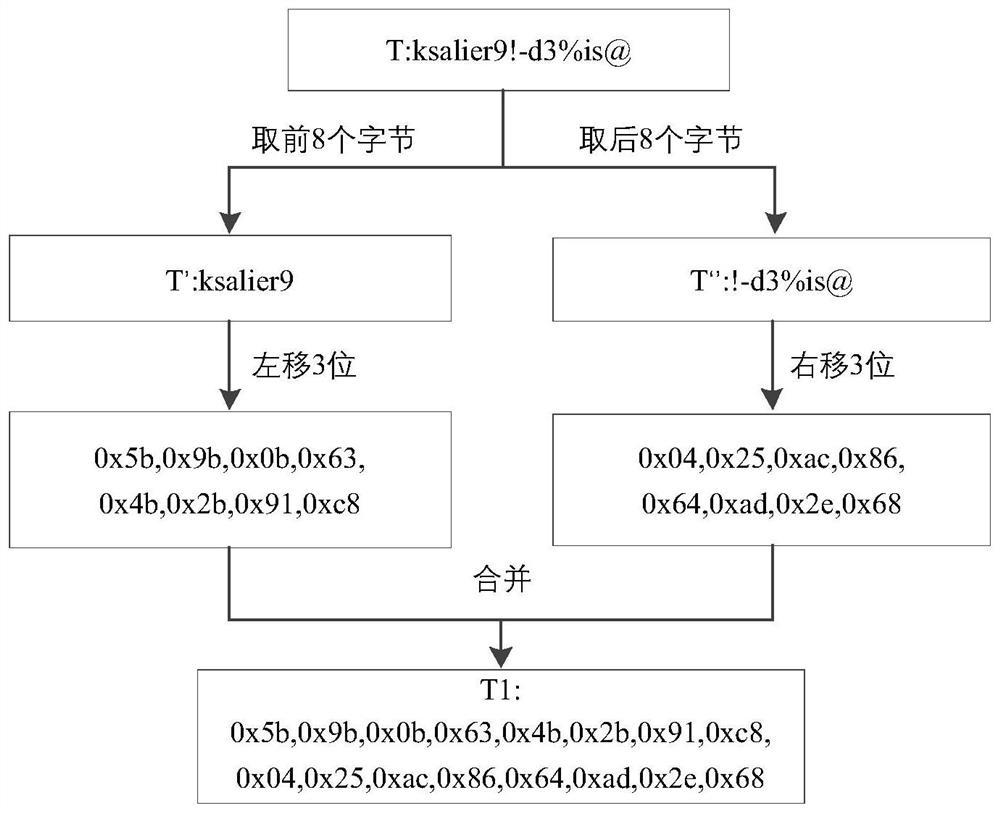
[0037] Various aspects and examples of the application will now be described. The following description provides specific details for a thorough understanding and enabling description of these examples. However, it will be understood by those skilled in the art that this application may be practiced without many of these details.
[0038] Also, some well-known structures or functions may not be shown or described in detail for the sake of brevity and to avoid unnecessarily obscuring the related description.
[0039] The terms used in the description given below, even if used in conjunction with the detailed description of some specific examples of this application, should be interpreted in their broadest reasonable manner. Even certain terms may be emphasized below, however, any terms that are intended to be interpreted in any limited manner will be explicitly and specifically defined in this Detailed Description section.
[0040] Without loss of generality, reference will b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com