Secure authentication communication system, method, and IoT device in fog computing environment
An Internet of Things device and security authentication technology, which is applied in the field of Internet of Things devices and security authentication communication systems, can solve problems such as increasing authentication delays, failing to guarantee authentication security, and inability to authenticate IoT devices, and achieve the effect of reducing communication delays
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0089] 1. A security authentication communication system structure in a fog computing environment:
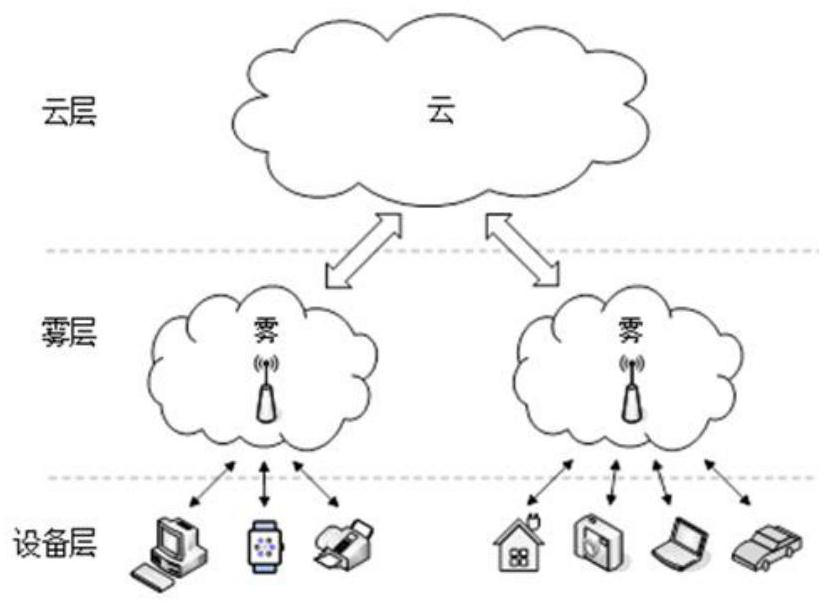
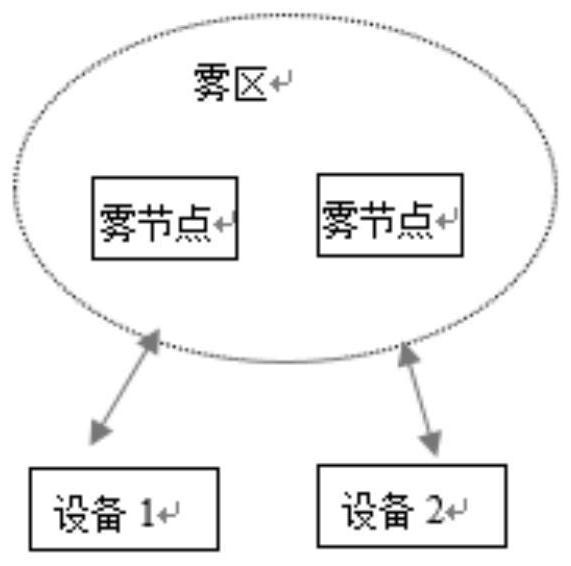
[0090] Fog computing consists of cloud layer, fog layer and device layer. The fog layer consists of many fog areas, and each fog area contains multiple fog nodes. The IoT device belongs to a fog area, and the IoT device transmits data by wireless communication with a fog node in the fog area. In addition, there is a trusted registration center in the system for the secure registration of newly added fog nodes and IoT devices. The purpose of the present invention is to realize secure communication at the fog layer and the device layer.
[0091] 2, the present invention realizes through the following technical scheme in order to achieve this purpose:
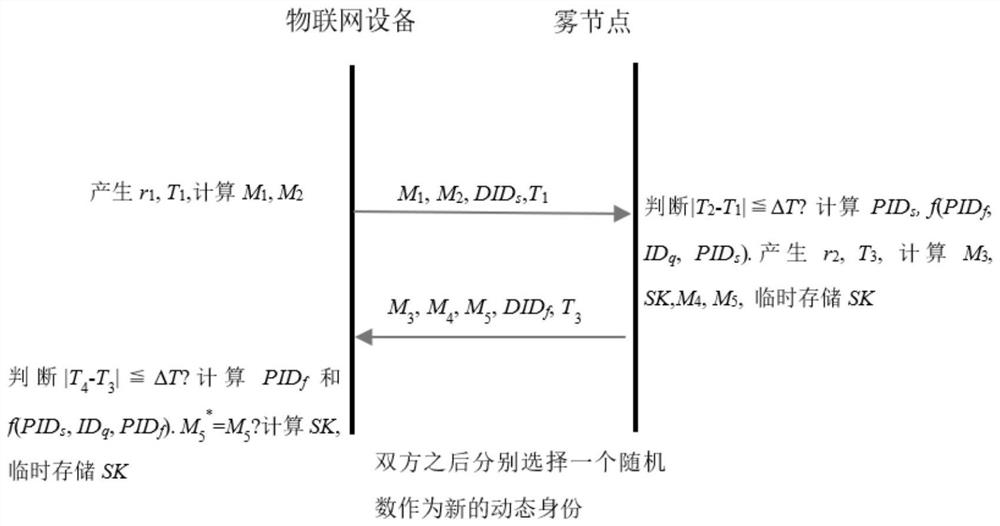
[0092] In order to achieve this purpose, the technical solution of the present invention includes three parts: first, a trusted registration center selects public parameters; second, a registration method for IoT devices and fog ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com