Safety and compliance treatment method suitable for open source component
A component and security technology, applied in computer security devices, electrical digital data processing, instruments, etc., can solve compliance and compatibility risks, intellectual property risks, etc., to improve development efficiency, reduce development costs, and ensure safety sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
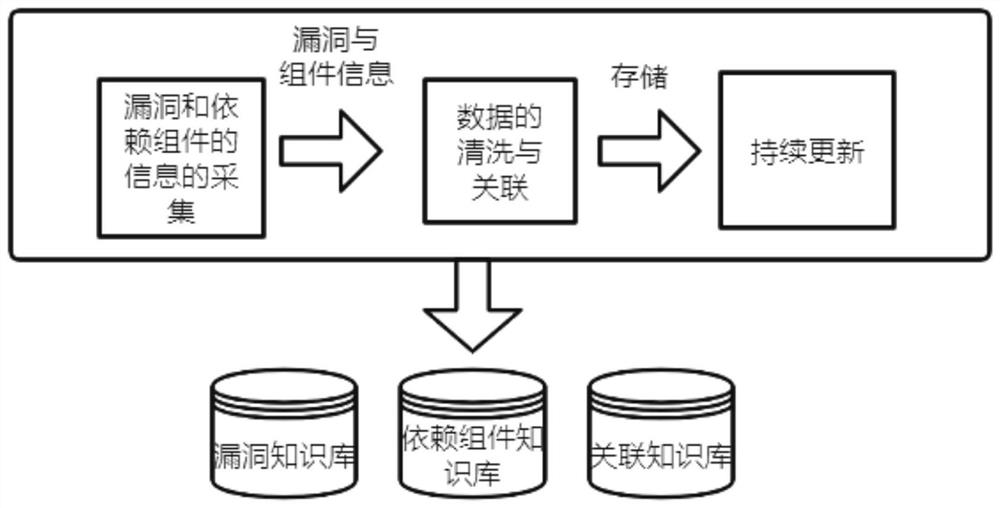
[0048] Such as Figures 1 to 6 ’s approach to security and compliance governance for open source components differs in that it includes the following steps:
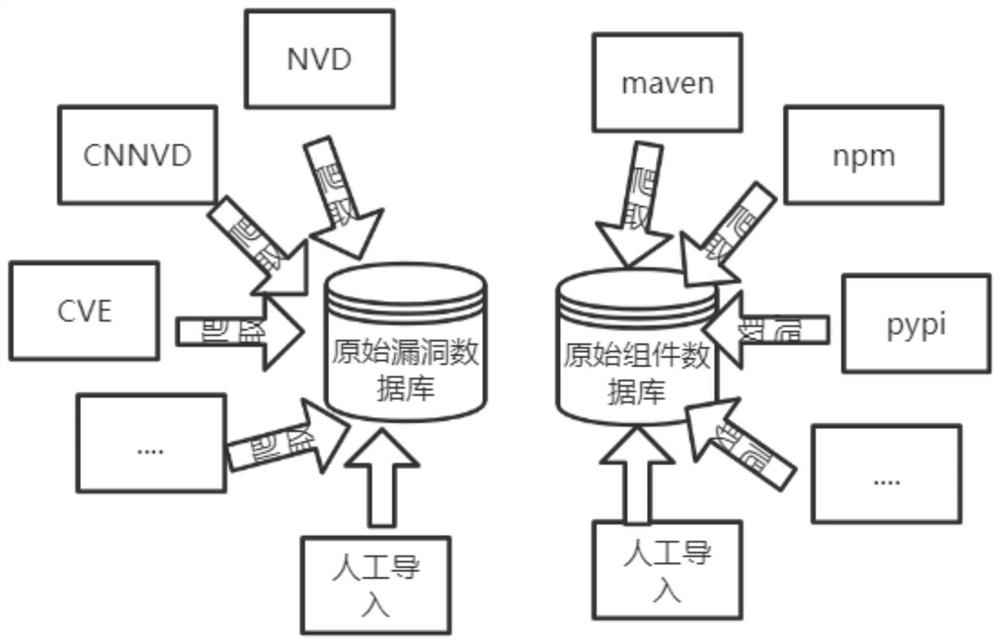
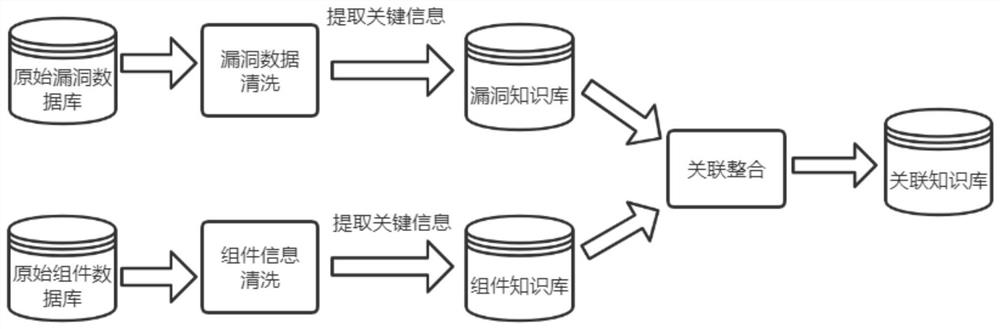
[0049] Step 1, construct the knowledge base. During this period, through the acquisition module (from multiple channels) through distributed crawlers, anti-crawler bypass and update strategies to collect vulnerability characteristics, vulnerability characteristics include CVE number, title, type, solution, component name, version, One or more of the license information. The manual import module can be used for the import of specific component information and basic vulnerability information data, satisfying the dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com