Vulnerability priority analysis method, system and device for industrial control system and storage medium
An analysis method and technology of industrial control system, applied in the field of network security, can solve problems such as inability to reflect, lack of vulnerability exploitability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
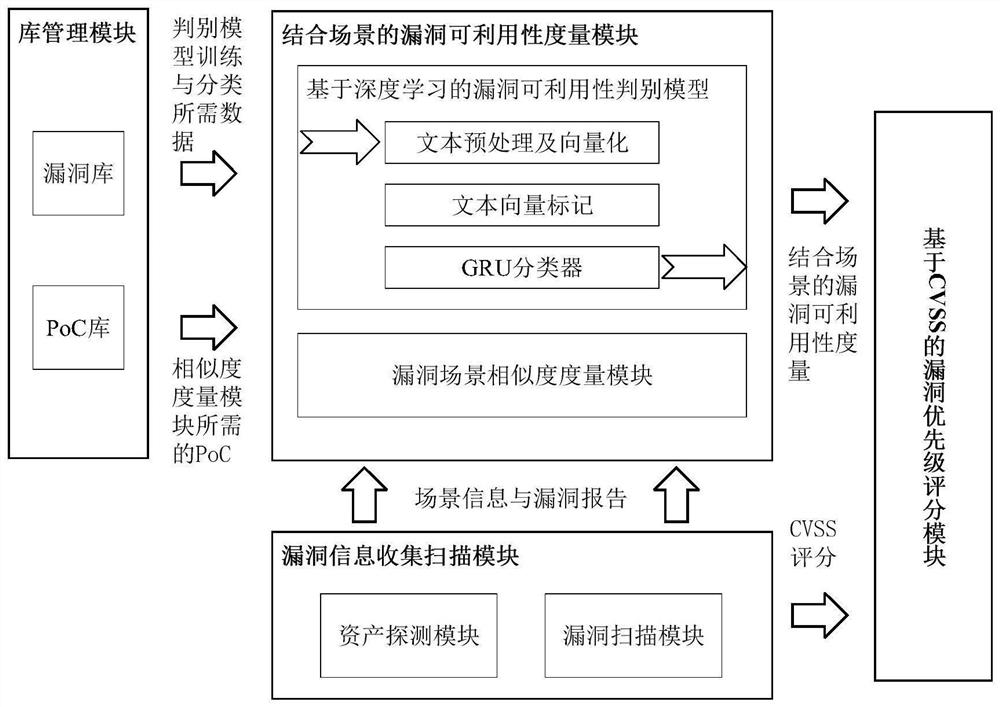
[0062] A vulnerability priority analysis method for industrial control systems, which refers to: the scenario and vulnerability information obtained through detection and scanning, combined with the PoC to give the vulnerability exploitability measurement combined with the scenario, and then based on the CVSS framework, the measurement value is combined with the vulnerability report. The CVSS score, which gives the priority score of the vulnerability.
Embodiment 2
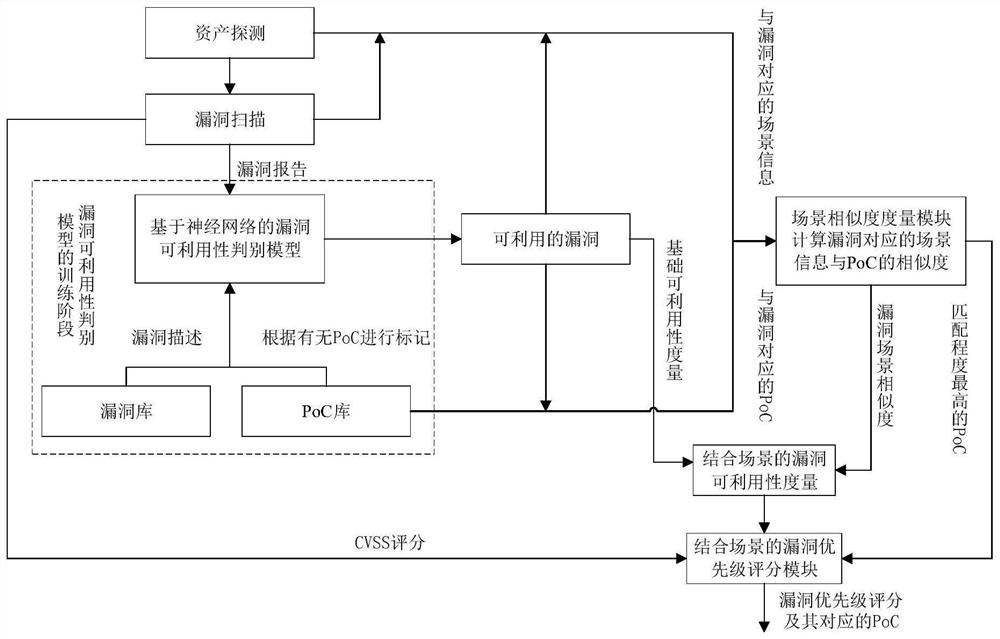
[0064] According to a kind of vulnerability priority analysis method for industrial control system described in embodiment 1, such as figure 2 , Figure 5 As shown, the difference is that the steps involved are as follows:
[0065] (1) Asset detection and vulnerability scanning: This is the basic step that vulnerability analysis must go through. After asset detection and vulnerability scanning, basic information is obtained. Basic information includes vulnerability reports, scene information corresponding to vulnerabilities, and CVSS scores; vulnerability reports Contains a brief description of the vulnerability, for example, in a certain system or service, on some version of them, a certain operation can cause a certain problem under certain network conditions, and also includes the release time, modification time, and Vulnerability type and other information. The scene information corresponding to the vulnerability includes information such as the host system, the service...
Embodiment 3
[0071] According to a kind of vulnerability priority analysis method for industrial control system described in embodiment 2, its difference is:
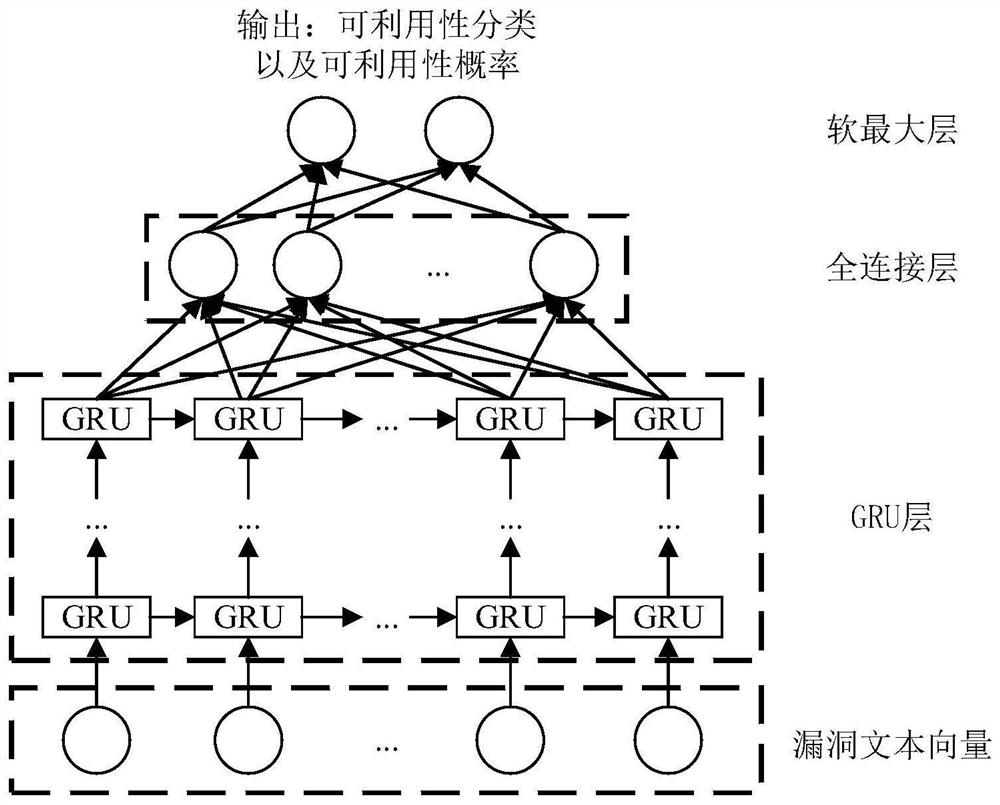
[0072] Such as Figure 4 As shown, the generation process of the vulnerability exploitability discriminant model based on deep learning is as follows:
[0073] In industrial control systems, actual verification of vulnerabilities requires relatively high costs. It is also of great significance in the actual production process if some vulnerabilities with low exploitability can be screened out from the set of vulnerabilities to be verified in advance. In the present invention, it is proposed to judge the exploitability of the vulnerability according to whether there is a corresponding PoC for the vulnerability. For new vulnerabilities, due to the short time of emergence, people do not know enough about the vulnerability, so there is no exploit method for this vulnerability, or the exploit method is not mature enough. This situation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com