Power dispatching operation instruction security verification method and system
A technology of operating instructions and power scheduling, applied in the field of power systems, can solve problems such as tampering of scheduling instructions, power accidents, and potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
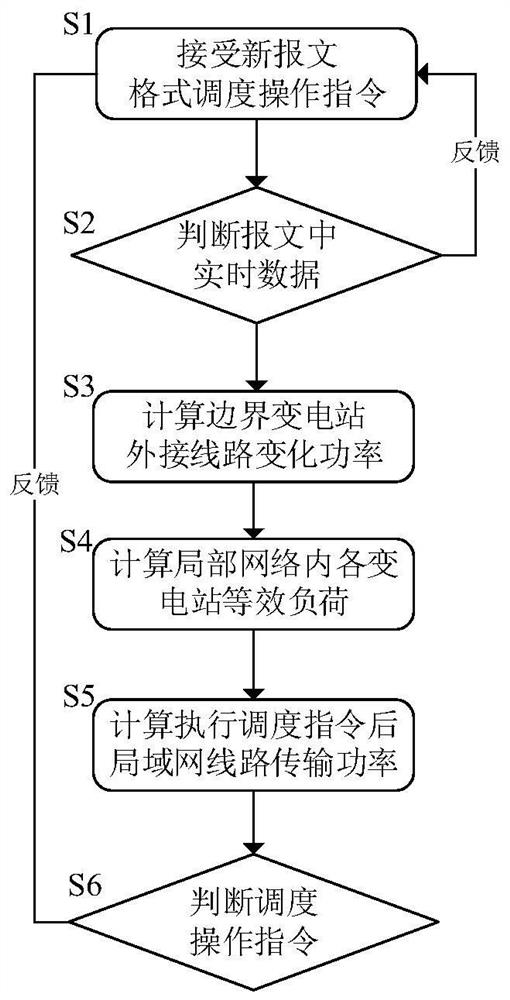
[0059] Further as a preferred embodiment, step S2 includes:
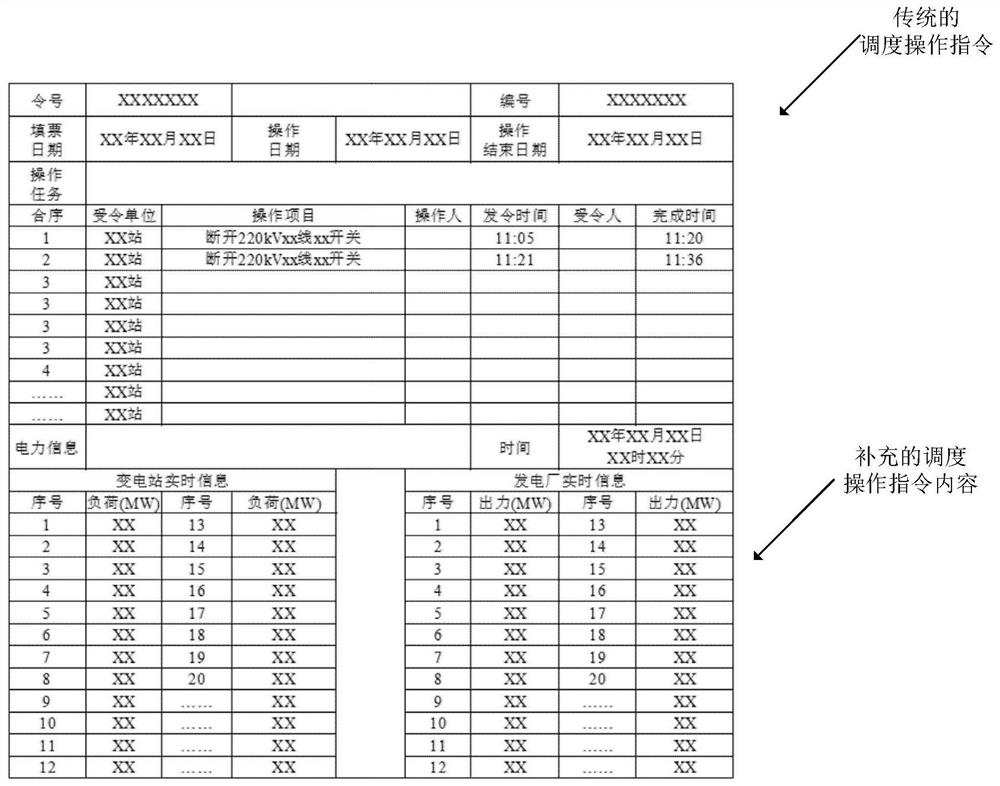
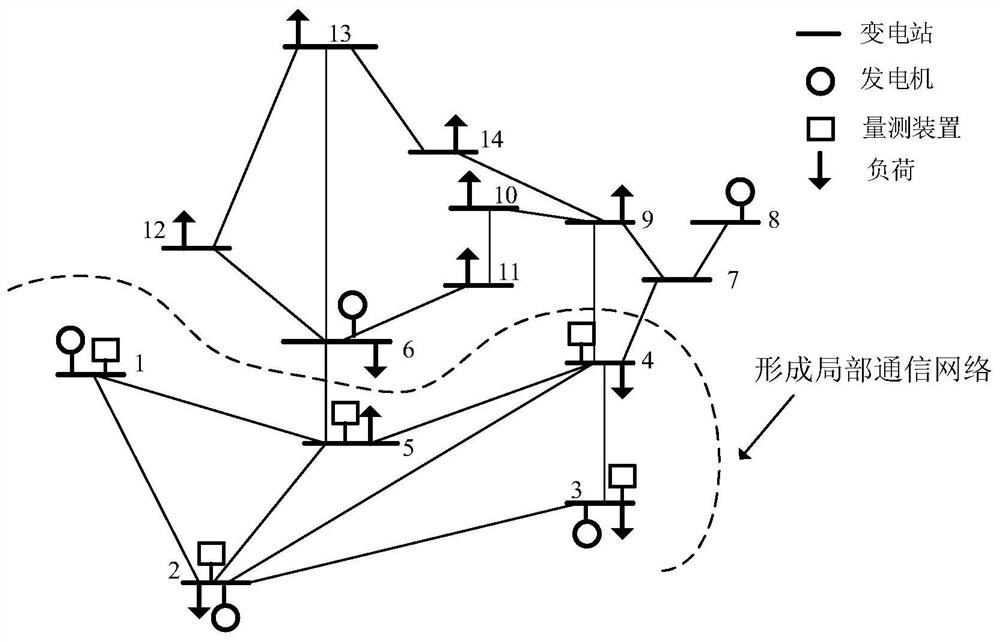
[0060] Step S21: According to the topological structure of the power network, establish a local communication network between substations, that is, a communication circle of substations. Choose substation n as the root node, and determine the child node substation j according to the connection line n-j of substation n. Substation n and all child nodes j establish a local communication network through a dedicated optical fiber network, which constitutes the communication circle of substation n, and realizes the actual data D between substation n and substation j. n 、D j , G n , G j of sharing. If there is a connecting line between substation j and substations outside the communication circle, substation j is a boundary substation.
[0061] In one embodiment, the schematic diagram of the communication network of substation 2 is as follows image 3 shown. Choose substation 2 as the root node, and determine subst...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com