Serial threat access management and control system and method
A control system and evaluation system technology, which is applied in the transmission system, digital transmission system, data exchange network, etc., can solve the problem of high false negative rate and false negative rate in attack recognition, unfavorable test and evaluation technology promotion, and large amount of attack tool data, etc. problems, to achieve the effect of strong data packets and processing power
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
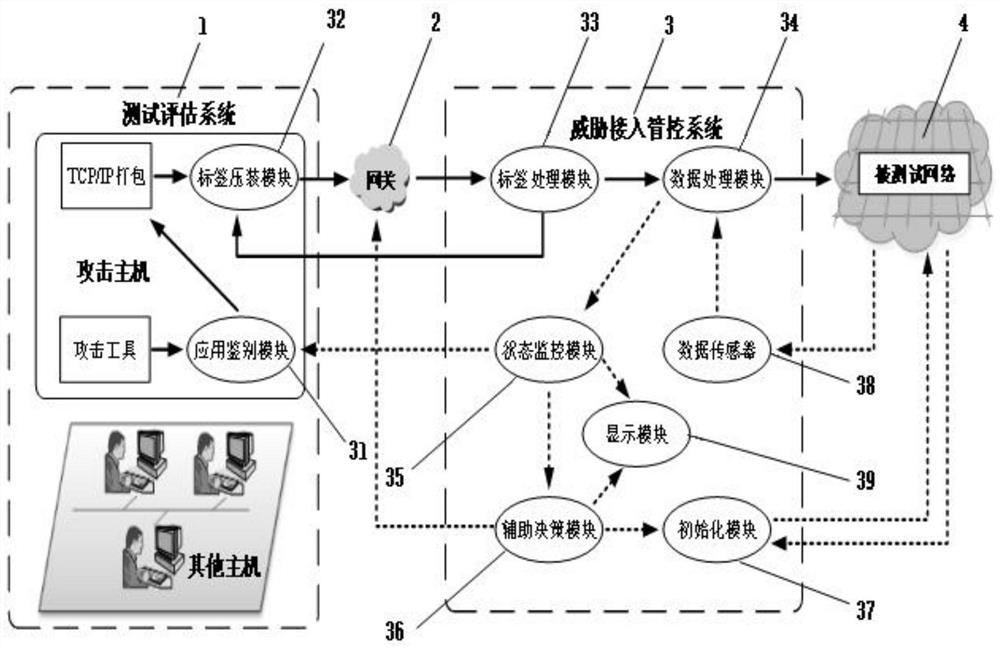
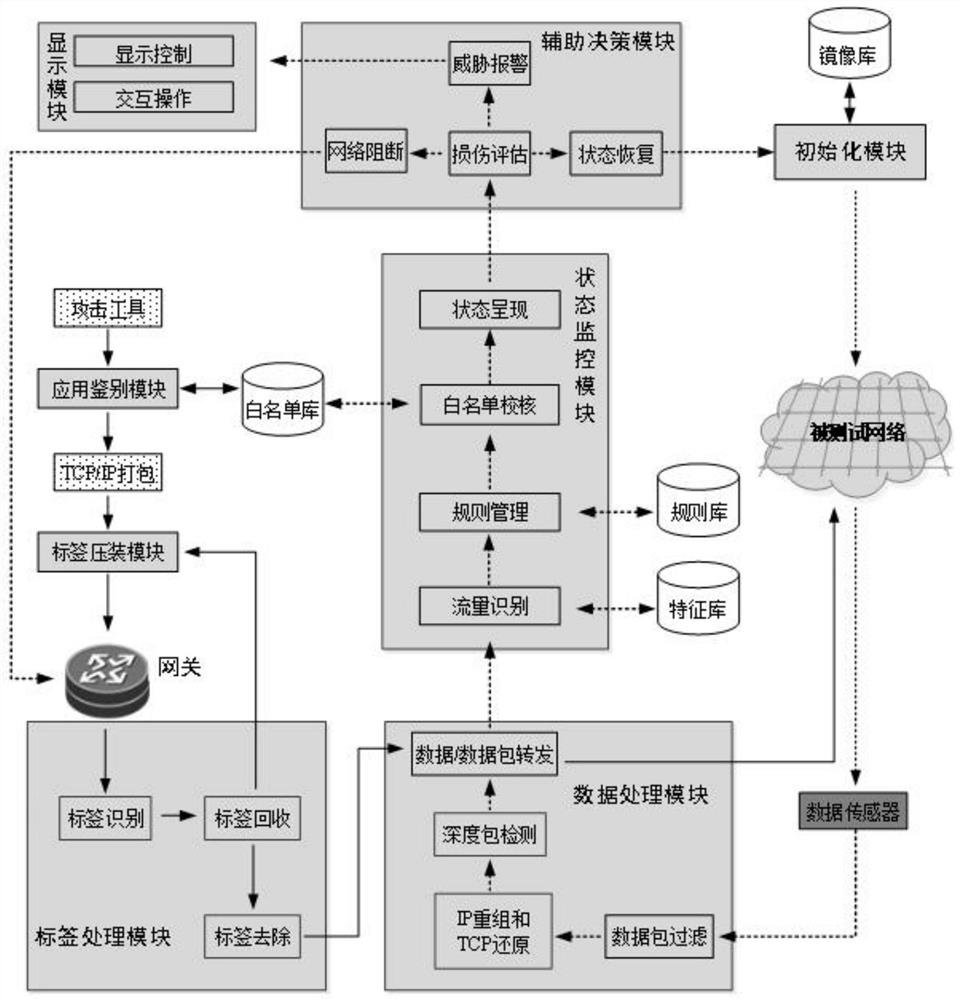
[0027] like figure 1 As shown, it is a schematic structural diagram of the threat access management and control system of the present invention, including an application identification module 31, a label pressing module 32, a label processing module 33, a data processing module 34, a status monitoring module 35, an auxiliary decision module 36, and an initialization module 37 , a data sensor 38 and a display module 39 are serially inserted into the link between the test evaluation system 1 and the network under test 4 . The specific function process of the threat access management and control system is as follows: the attack host in the test and evaluation system 1 uses attack tools to generate attack data, and according to the pre-set white list of attack tools, after being identified by the application identification module 31, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com