Method, system and storage medium for http traffic analysis and processing oriented to dpi applications
A traffic analysis, HTTP protocol technology, applied in the field of network security, can solve problems such as code instability, achieve the effect of improving overall performance, saving system overhead, and stabilizing the protocol analysis process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] In order to make the technical solutions of the present invention more obvious and easy to understand, specific embodiments are given and described in detail below with reference to the accompanying drawings.
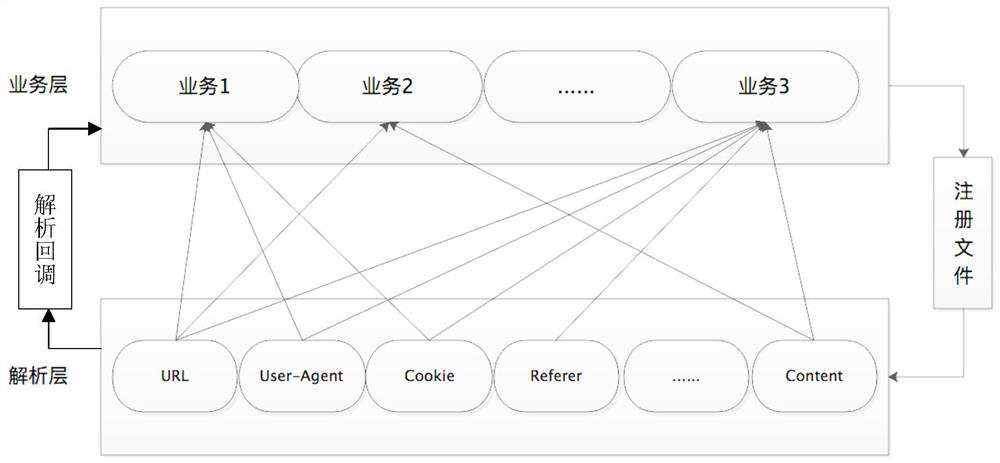
[0025] The flow chart of the method of the present invention is as follows figure 1 As shown, it mainly includes two basic steps of service registration HTTP field and HTTP field parsing and callback, and the details are as follows.
[0026] (1) Business registration HTTP field steps
[0027] Different services have different requirements for HTTP protocol fields. The HTTP field required by a certain service is called the service's interest domain for the HTTP parsing result. The business layer writes its own interest domain in the configuration file, and the parsing layer obtains the interest domain of different services through the configuration file. This process is the registration process of the business interest domain.
[0028] In addition, during the re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com