Invisible office printing text encryption and decryption method
An encryption method and text technology, applied in image data processing, instruments, image data processing, etc., can solve problems such as large amount of calculation, inability to encrypt data, single spectrum, etc. The effect of less resource consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The present invention will be described in detail below with reference to the accompanying drawings and examples.
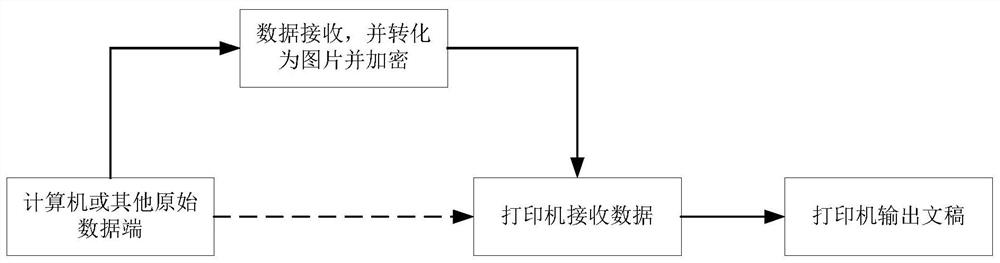
[0032] Under normal circumstances, the basic process of printing is:
[0033] 1) The computer or other raw data end transmits the information to be printed to the printer;
[0034] 2) The printer receives and processes the print data;
[0035] 3) The printer outputs the final document through the processes of developing, transferring and fixing.
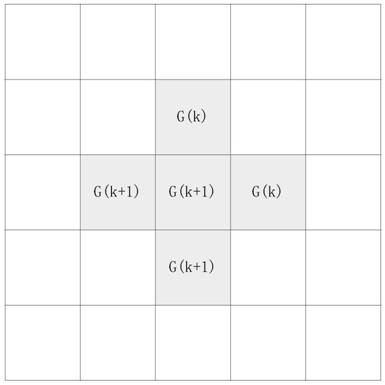
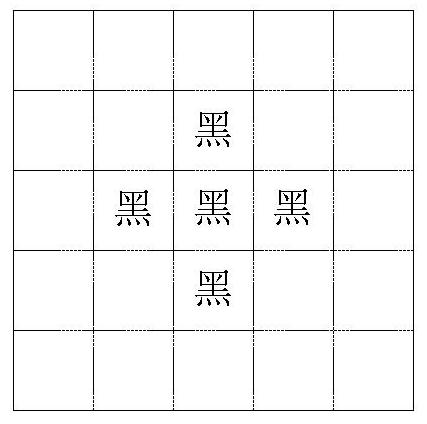
[0036] However, in the present invention, before the original data is sent to the printer, the original data is acquired and converted into a picture, and then the picture is encrypted. After the encryption is completed, the image information is passed to the printer, and the final encrypted document is output. Such as figure 1 As shown, specifically, the present invention encodes information based on the density or grayscale information of fonts or pictures, and after transmission, decrypts the encoded data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com