Secure calling convention system and methods
A technology of API calling and application programming interface, which is applied in transmission systems, digital transmission systems, secure communication devices, etc., and can solve problems such as infeasibility, API not being hidden, and inability to protect licensed functions, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
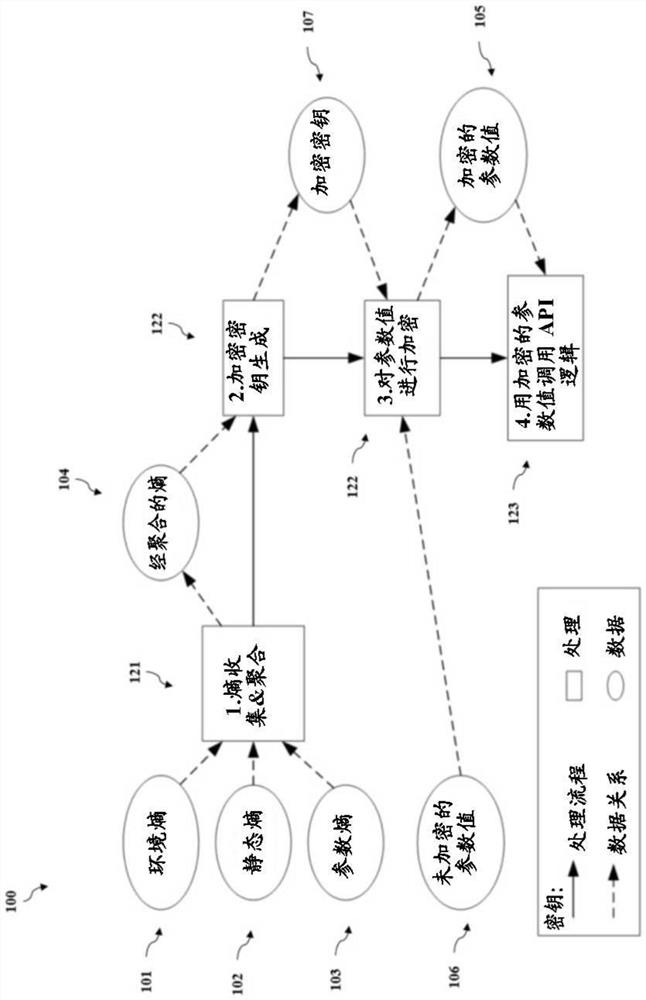
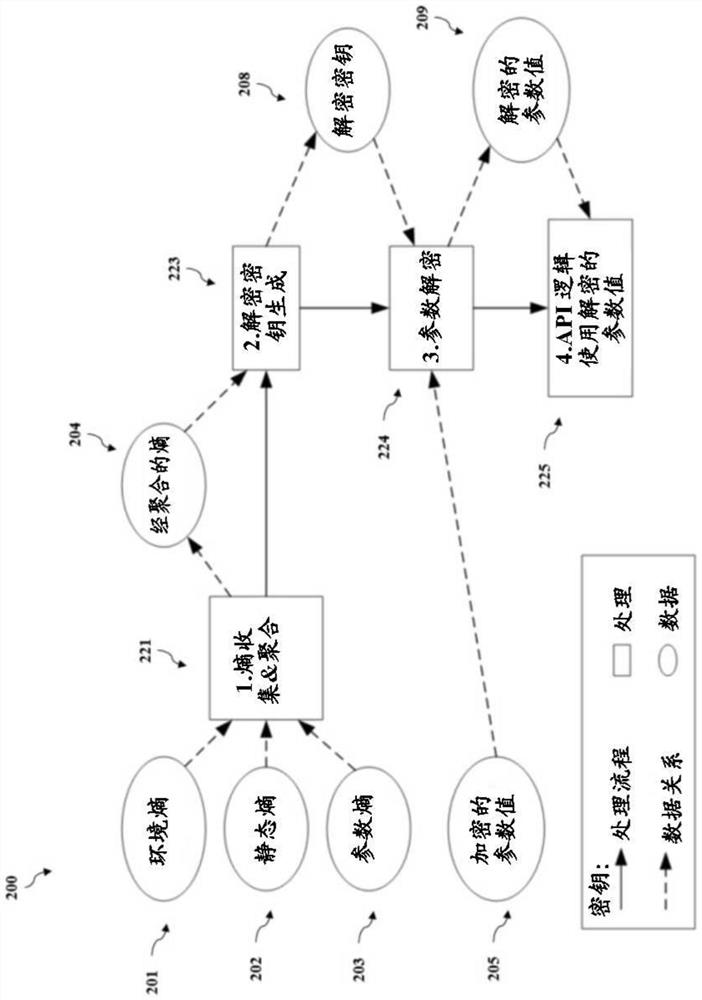
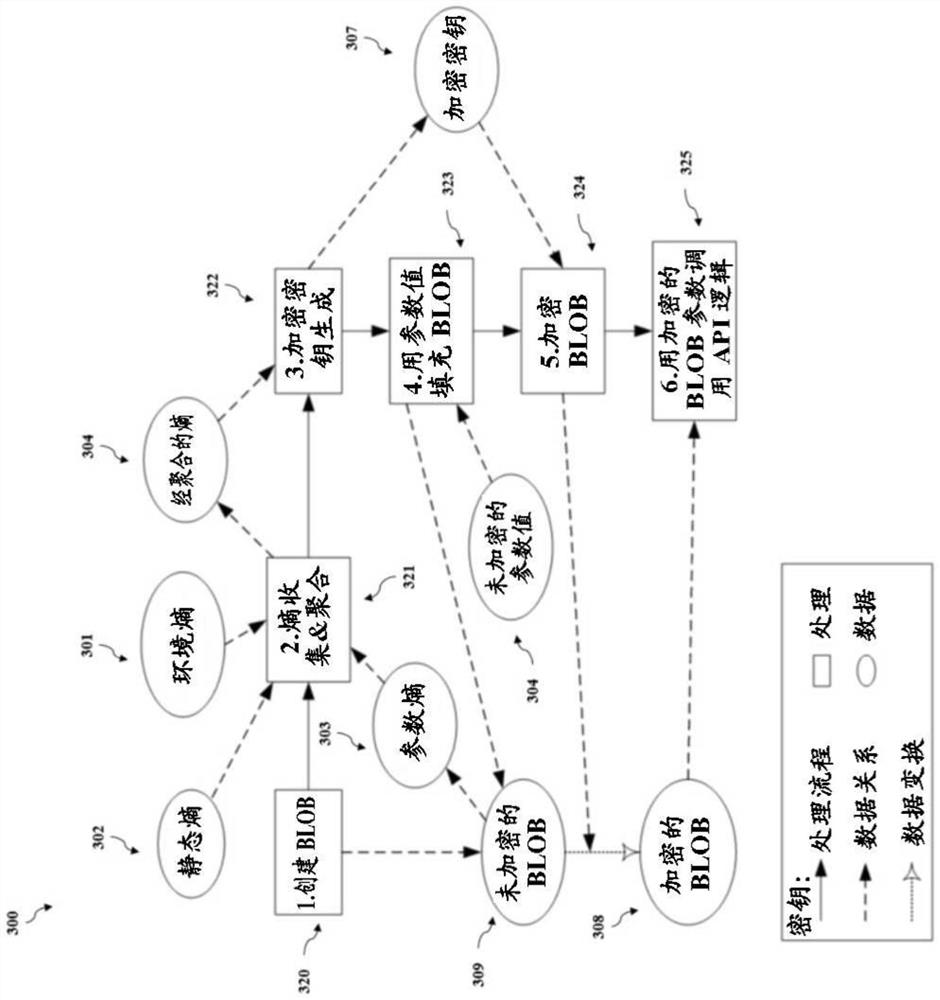
[0055] Embodiments of the present disclosure relate to systems and methods for using SCCs to protect information passed between a caller of an API and logic contained within the API.
[0056] To this end, in various embodiments, protecting information includes information that has undergone cryptographic operations. According to some embodiments, a "cryptographic operation" includes, but is not limited to, a set of instructions stored on a transitory and / or non-transitory computer-readable medium that, when executed, results in encryption of information or one or more portions thereof. Encrypt or decrypt.
[0057] As used herein, according to some embodiments, "encryption" is the process of transforming information from its original form into a form in which the original form can no longer be observed. In some embodiments, encryption requires the use of encryption keys used to manage transformations. As used herein, in various embodiments, an "encryption key" is a value used...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com