Mail user identity authentication and key distribution method, system, equipment and medium
A technology of user identity authentication and key distribution, which is applied to key distribution, can solve problems such as message integrity protection attacks, high error rate, and key leakage, so as to rectify email insecurity and chaos, protect security, and save development costs Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
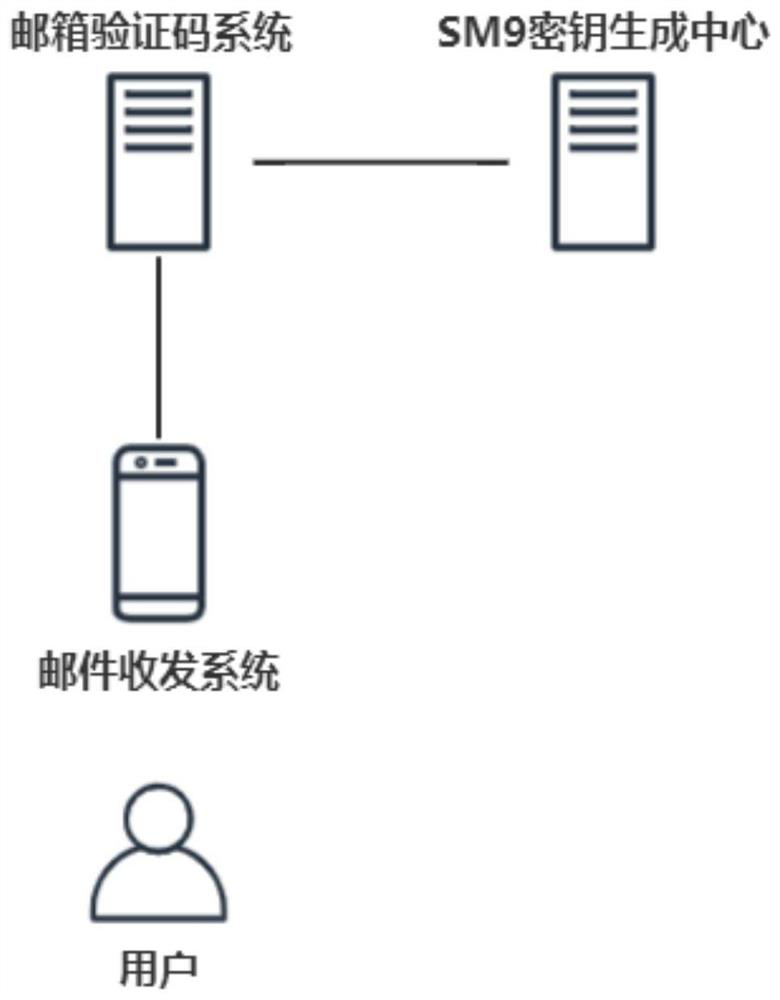
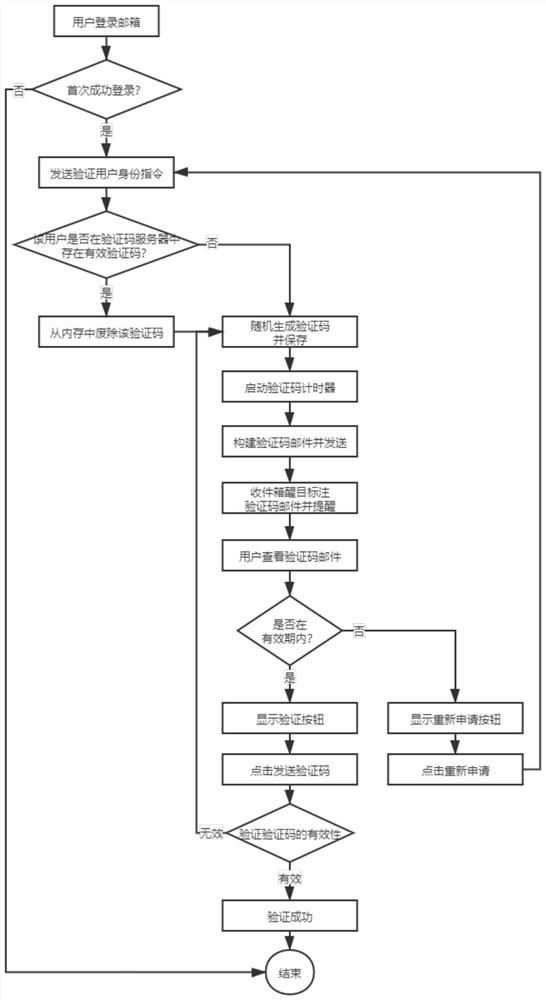
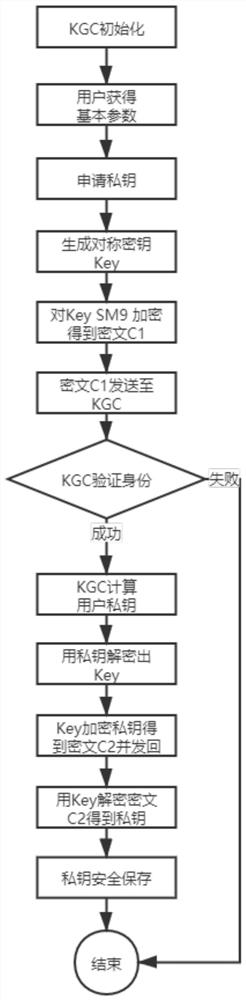
[0088] as attached Figure 1-3 As shown, the present embodiment provides a mail user identity authentication and key distribution method, involving a mail verification code unit, a key generation unit KGC, and a mail sending and receiving system; Operations such as writing emails can also realize the encryption and decryption of emails; however, the prerequisite for email encryption and decryption is to have the user's own public and private keys, and only the user knows it; otherwise, the security of emails cannot be guaranteed; this embodiment passes email verification The code unit is used to send the verification code email and verify the verification code, and then realize the user identity authentication, and finally the key generation unit KGC securely issues the private key belonging to the user identity.
[0089] Specifically include the following steps:
[0090] Step 1. Authentication
[0091] Step 11, the user logs into the mailbox; wherein, the login mailbox is t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com