Massive IoT device authentication method, storage medium, and information data processing terminal
A technology of IoT devices and authentication methods, which is applied in the field of storage media, massive IoT device authentication methods, and information data processing terminals. It can solve problems such as incomplete application of certification schemes, attacks on insecure communication channels for remote identity verification, and reliance on certificates, etc. , to achieve the effect of reducing network pressure and communication overhead, ensuring security and efficiency, and enhancing authentication security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
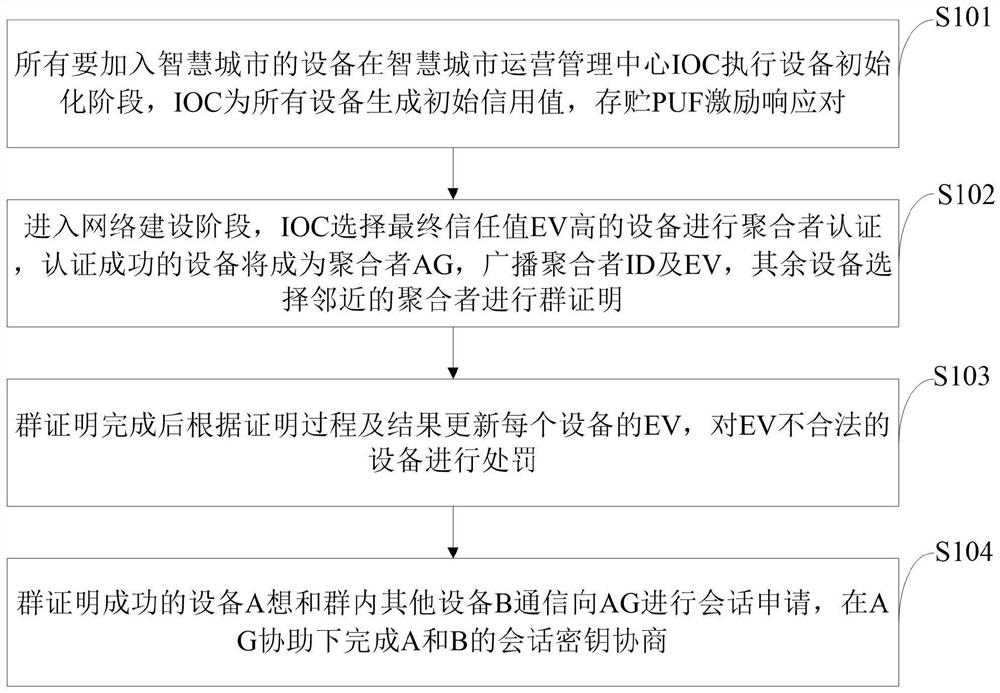
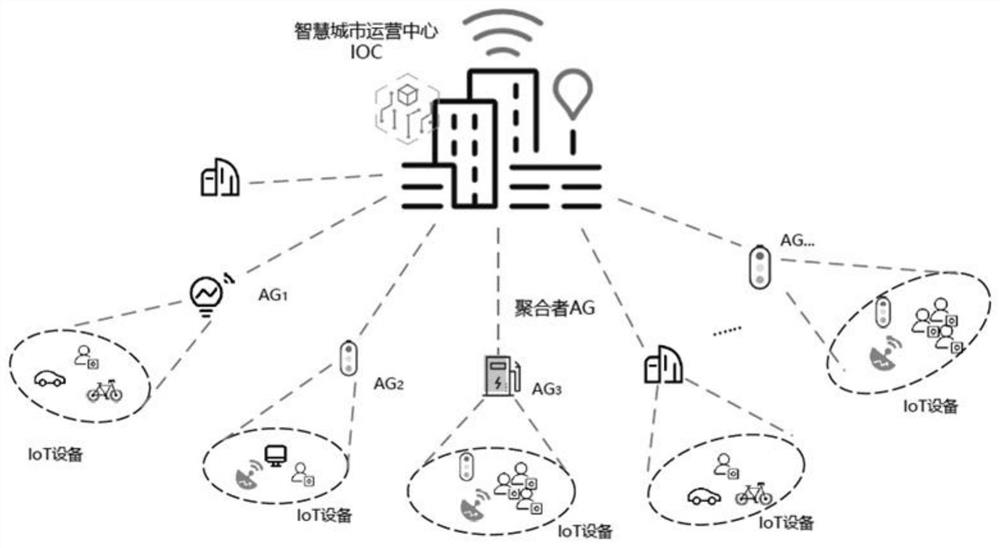
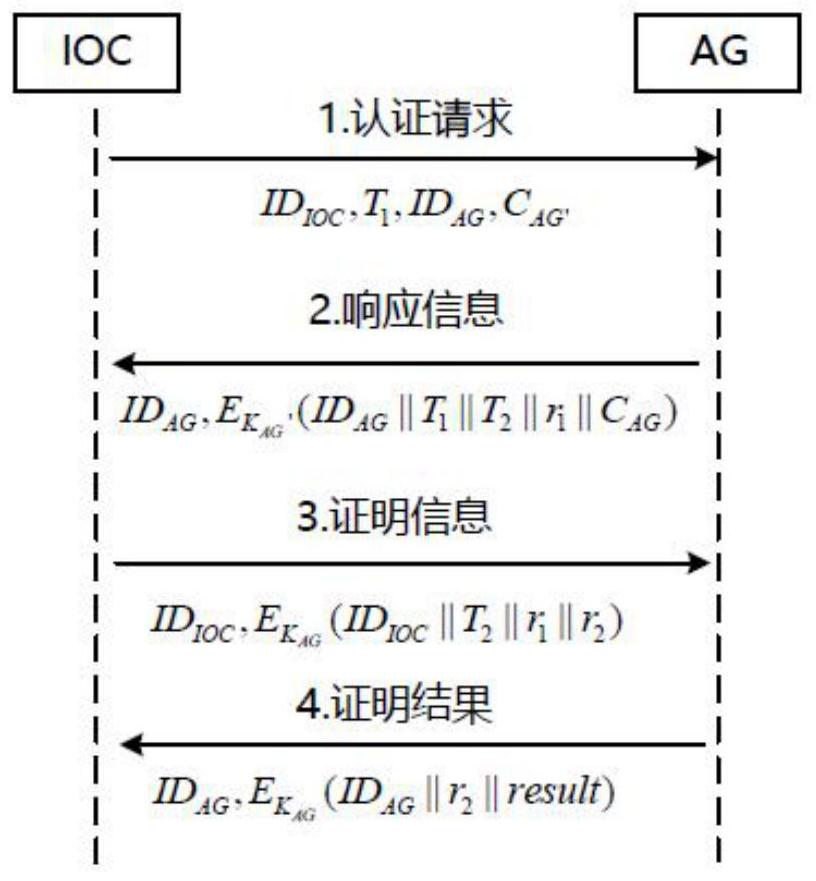
[0055] Aiming at the problems existing in the prior art, the present invention provides a massive Internet of Things device authentication method, a storage medium, and an information data processing terminal. The present invention is applicable to the scene of unified authentication of massive IOT devices in smart cities. By selecting IOT devices with high credit value and successful authentication to become AG, it assists IOC in authenticating massive IOT devices, reduces the network pressure of IOC, and uses reputation mechanism to The behavior of each IOT device is monitored, which can effectively defend against DOS att...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com