Resource sharing device and system based on Internet security lock
A resource sharing and security lock technology, applied in the field of Internet resource sharing, can solve the problems of increasing user expenditure, poor contact, and failure to return in time, and achieve the effect of improving practicability, avoiding expenditure, and improving experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
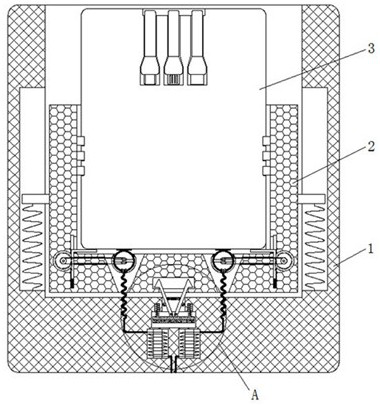
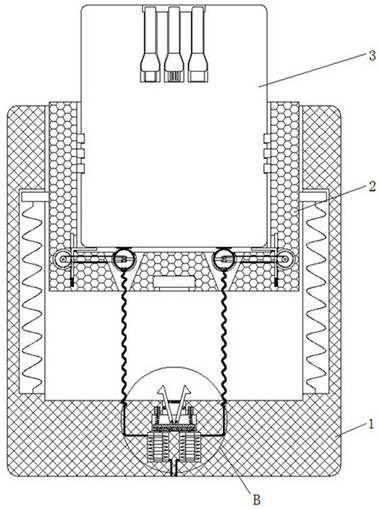
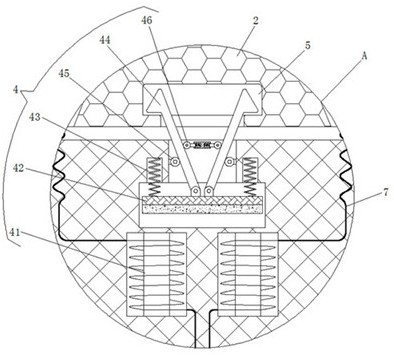
[0037] see Figure 1-4 , 7, a resource sharing device based on Internet security locks, including a housing 1, a limiting mechanism 4 is installed inside the housing 1, the limiting mechanism 4 includes a energized coil 41, and the energized coil 41 is adjacent to the magnetic plate 42 after being energized The magnetic pole on the surface has the same name as the magnetic pole, so that the energized coil 41 can generate repulsion to the magnetic plate 42 after being energized, and the top of the energized coil 41 inside the housing 1 is slidably connected to the magnetic plate 42, and the tops of the left and right sides of the magnetic plate 42 are fixedly connected with Spring 43, the top of magnetic plate 42 middle part is mutually rotatable and is connected with buckle 44, and the quantity of buckle 44 has two, expands to both sides at the top of magnetic plate 42, and symmetrical distribution, buckle 44 is all positioned at fixed pulley 45 and Between the telescopic pull...
Embodiment 2
[0045] see figure 1 , 2, 5, 6, a resource sharing device based on Internet security locks, including a housing 1, a connecting frame 2 is slidably connected to the top of the housing 1, a power bank 3 is slidably connected to the top of the connecting frame 2, and the limit mechanism 4 is located at The bottom of the casing 1 is close to the side of the connection frame 2, and the bottom of the connection frame 2 is provided with a groove 5, and the bottom of the connection frame 2 is equipped with a cleaning mechanism 6, which includes a receiving plate 61, and the left and right sides of the bottom of the connection frame 2 The side is elastically connected with a receiving plate 61, and the side of the receiving plate 61 away from the center of the bottom of the connecting frame 2 is meshed with a gear 62, and the left and right sides of the bottom of the connecting frame 2 are rotationally connected with an electric shock ring 63, and the transmission connection between th...
Embodiment 3
[0047] see Figure 1-8 , a resource sharing device based on Internet security locks, including a housing 1, a limit mechanism 4 is installed inside the housing 1, and the limit mechanism 4 includes a energized coil 41, and the adjacent surface of the energized coil 41 is adjacent to the magnetic plate 42 after energization The magnetic pole has the same name as the magnetic pole, so that the energized coil 41 can generate repulsion to the magnetic plate 42 after being energized. The upper part of the energized coil 41 inside the housing 1 is slidably connected to the magnetic plate 42, and the tops of the left and right sides of the magnetic plate 42 are fixedly connected to the spring 43. , the top of the middle part of the magnetic plate 42 is rotatably connected with buckles 44, and there are two buckles 44, which are spread out to both sides at the top of the magnetic plate 42 and distributed symmetrically. The buckles 44 are all located on the fixed pulley 45 and the teles...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com