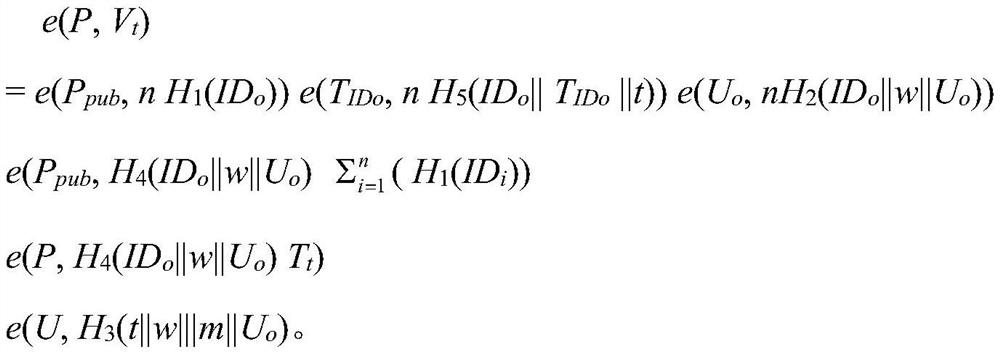An identity-based multi-proxy signature method and device for protecting private keys
A proxy signature and proxy signer technology, which is applied in the field of identity-based multiple proxy signatures and devices for protecting private keys, can solve the problems of key protection that cannot be solved in application scenarios, cannot be protected by multiple proxy signature keys, etc. Avoid revocation of identity problems and the effect of resisting key leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The present invention will be further described in detail below in conjunction with the accompanying drawings.
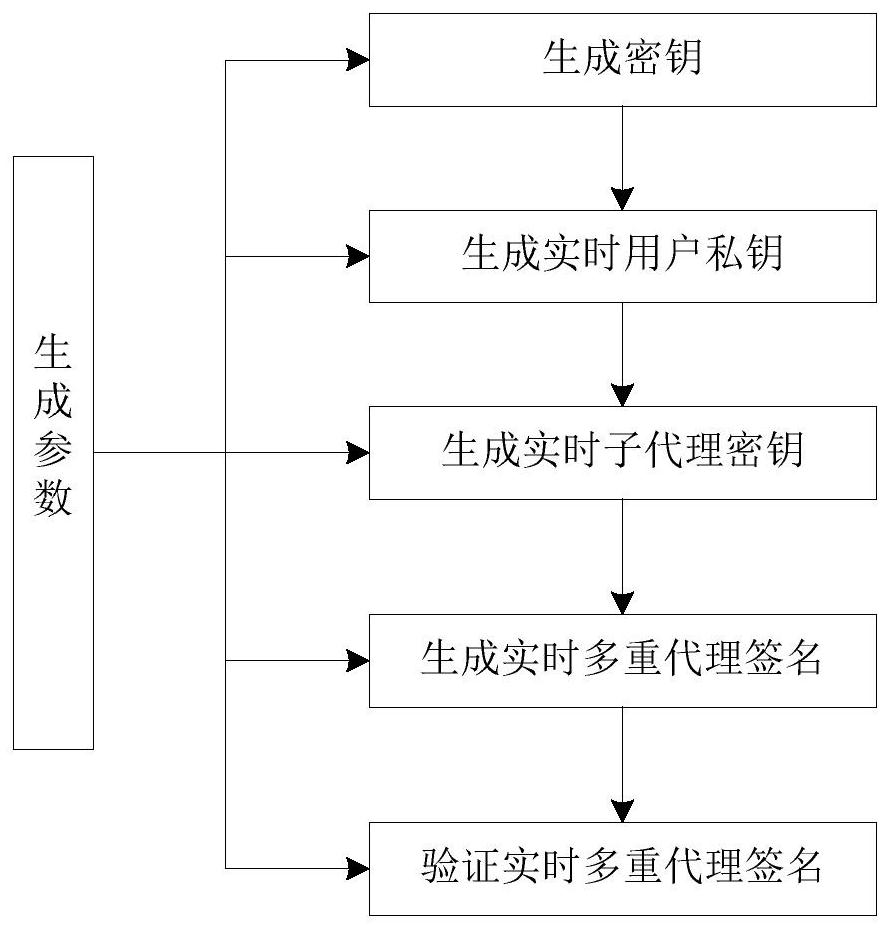
[0050] The invention provides an identity-based multiple proxy signature method for protecting private keys. A credible facilitator is set up, and the facilitator helps the proxy signer generate an initial private key and a public key, and checks the proxy private key at the starting point of each time period. Update, generate the sub-agent keys of n proxy signers, n proxy signers jointly generate multiple proxy signatures, and the message verifier uses the identity of the original signer and the identity of the n proxy signers after receiving the multiple proxy signatures Verify multi-proxy signatures. like figure 1 shown, including the following steps:
[0051] Step 1: Build an identity-based multi-agent signature system and establish system parameters.
[0052] The identity-based multi-agent signature system constructed by the present invention includes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com