A privacy protection identity authentication system and method for Internet of Vehicles
A privacy protection and identity authentication technology, applied in the field of wireless network security, can solve problems such as witch attacks, achieve the effect of improving performance, avoiding certificate storage and management overhead, and ensuring anonymity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
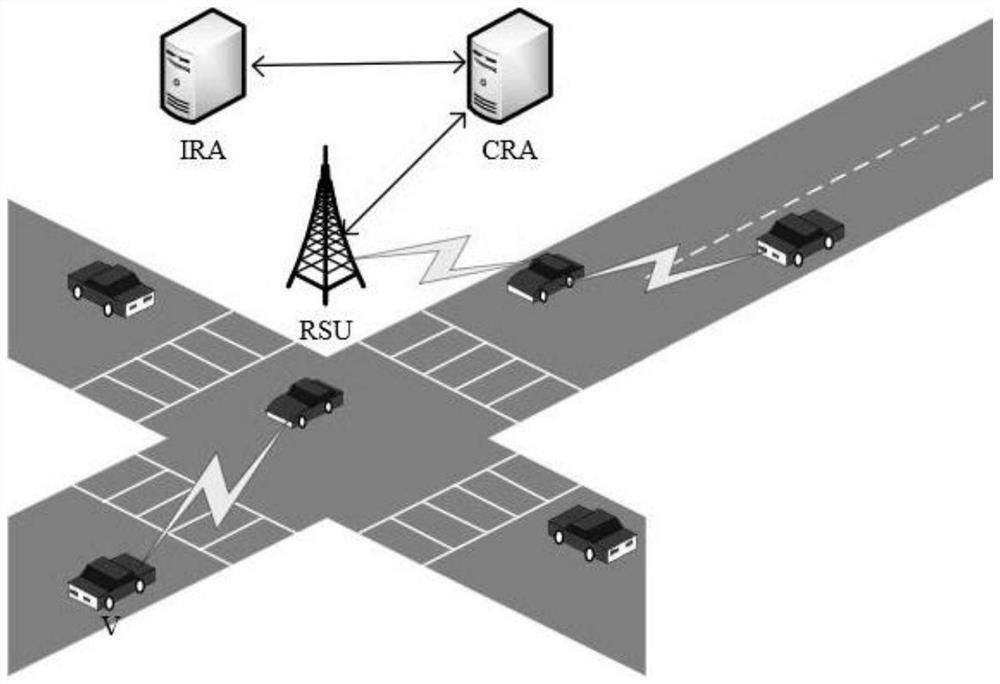
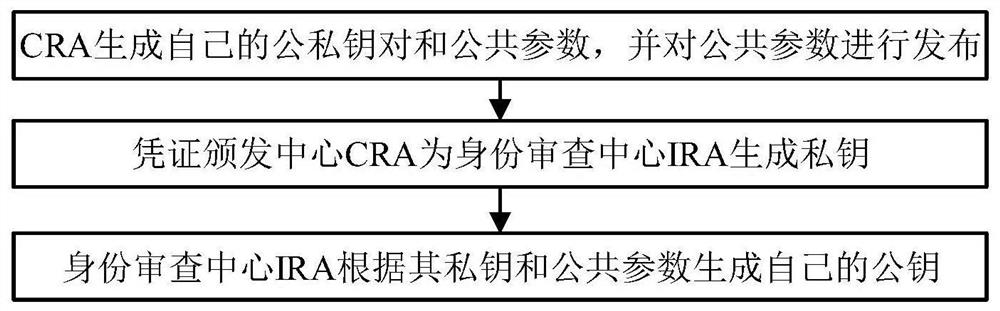
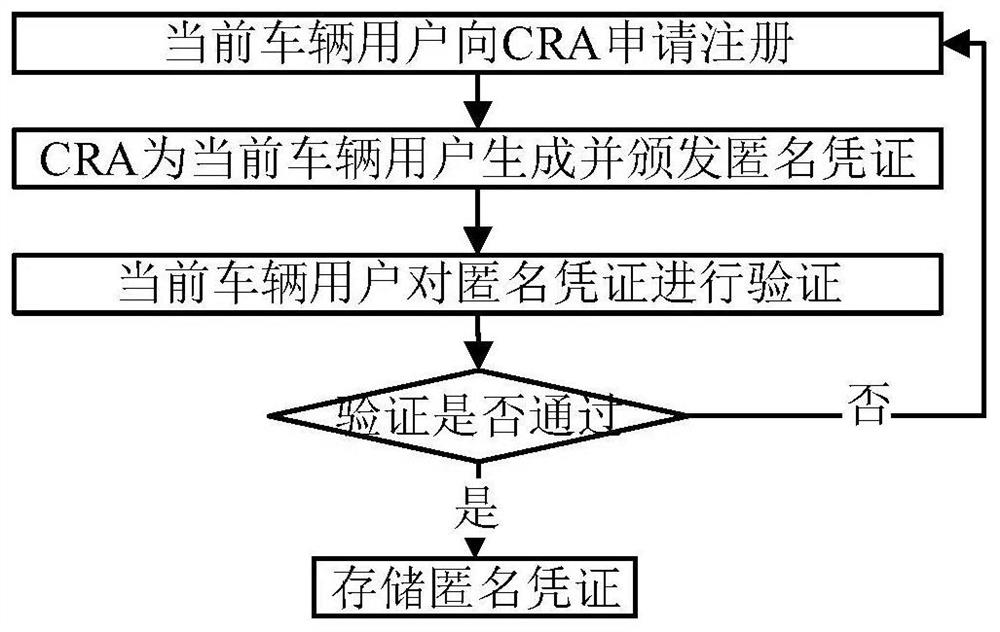
[0040] The purpose of the present invention is to provide a privacy-protected identity authentication system and method oriented to the Internet of Vehicles. A third-party trust agency issues anonymous certificates to vehicle users who apply for registration, and the user has only one legally available certificate at the same time, ensuring that the user is at the same time. Complete identity authentication without revealing your true identity. At the same time, under special circumstances, you can restore the identity of vehicle users who have illegal behaviors in the network through a third-party authentication agency to ensure the conditional anonymity and effective authentication of users. Limit malicious users in the network from causing Sybil attacks.
[0041] figure 1 It is a schematic framework diagram of the privacy protection identit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com