Equipment access method, data transmission method and computer readable storage medium
A device access and transmission method technology, applied in the field of communications, can solve the problems affecting the security and reliability of the device system, the low security of the plaintext transmission authentication vector, and the easy leakage of the shared symmetric key, so as to improve the security and reliability. Effectiveness of reliability, enhanced security, and guaranteed benefits
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
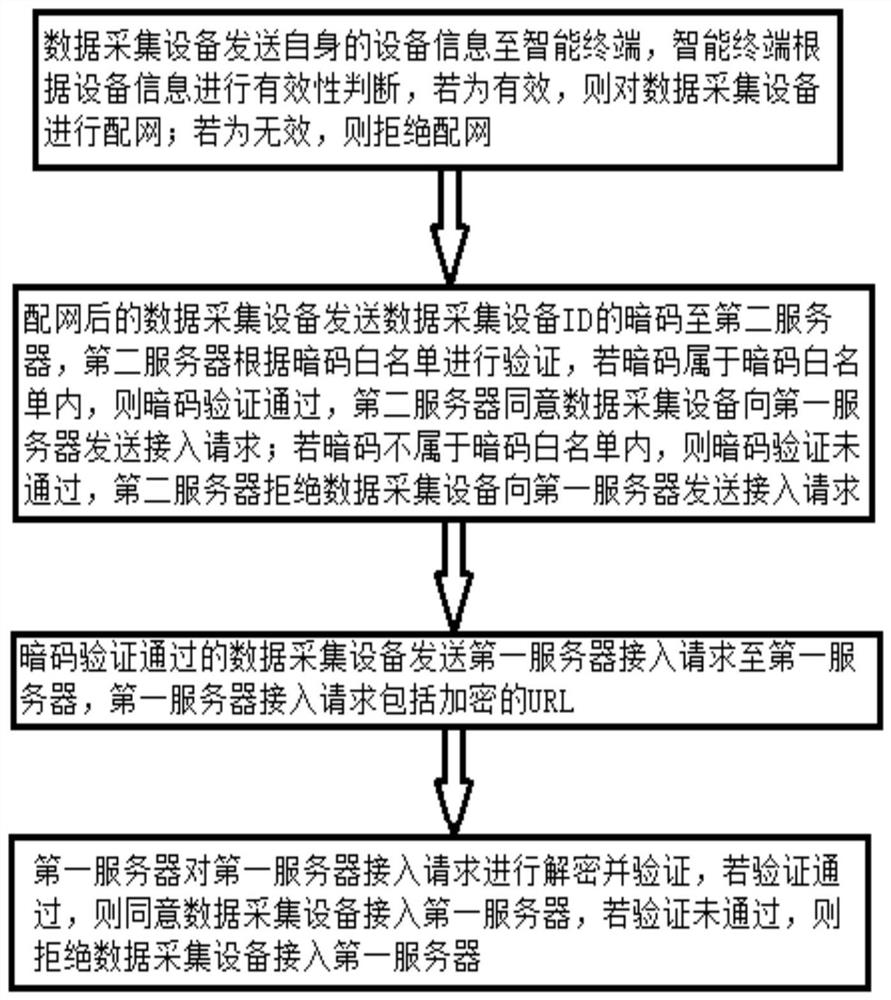
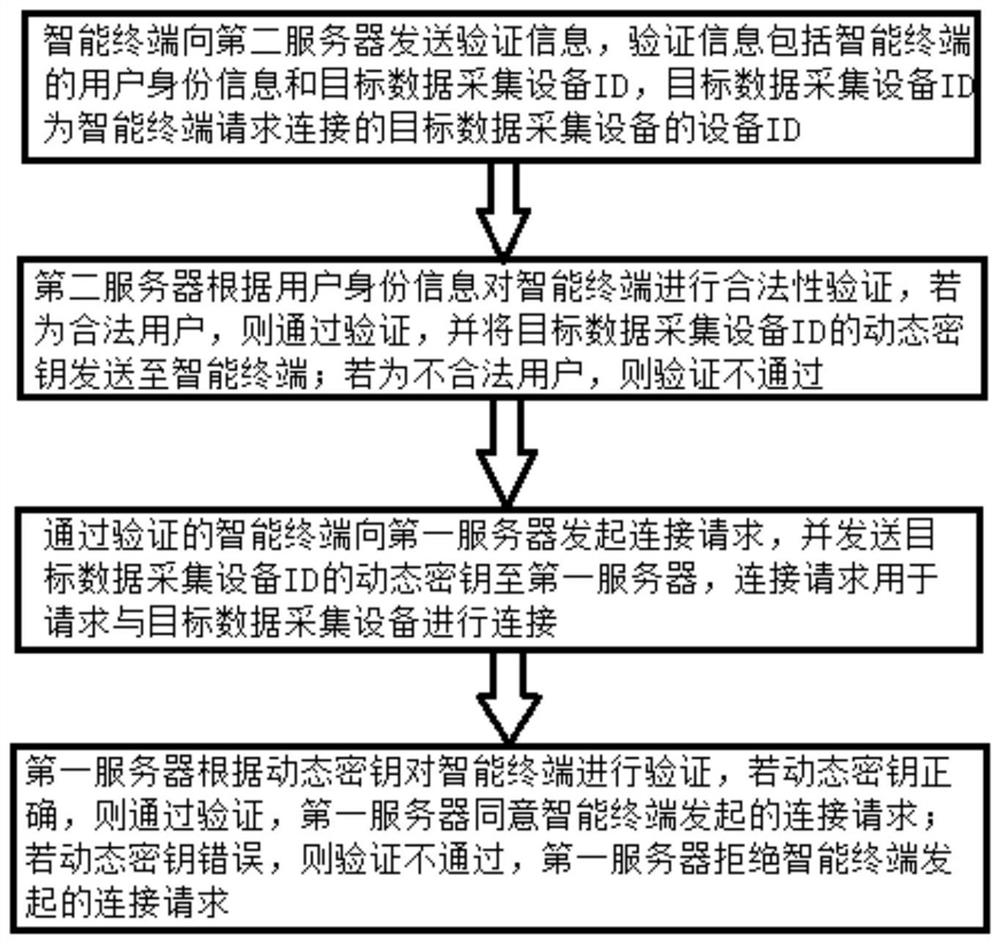
[0054] In order to make the purpose, technical solutions and advantages of this application clearer, the following in conjunction with the attached Figure 1-6 And embodiment, this application is described in further detail. It should be understood that the specific embodiments described here are only used to explain the present application, not to limit the present application.
[0055] In traditional technology, due to the possibility of private connection and counterfeiting of data collection equipment, most systems cannot effectively identify the legitimacy of data collection equipment, and once the system is attacked by fake equipment, it is easy to cause the real data collection equipment to be unable to access and use At the same time, it will also bring great risks to the system, such as data leakage or distributed denial of service attacks, and even cause internal network paralysis; in view of the openness of the network, the reliability of data acquisition equipment ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com