Alliance chain privacy protection method based on secure multi-party computing
A secure multi-party computing and privacy protection technology, applied in the field of alliance chain privacy protection, to achieve the effect of untraceability and verifiability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
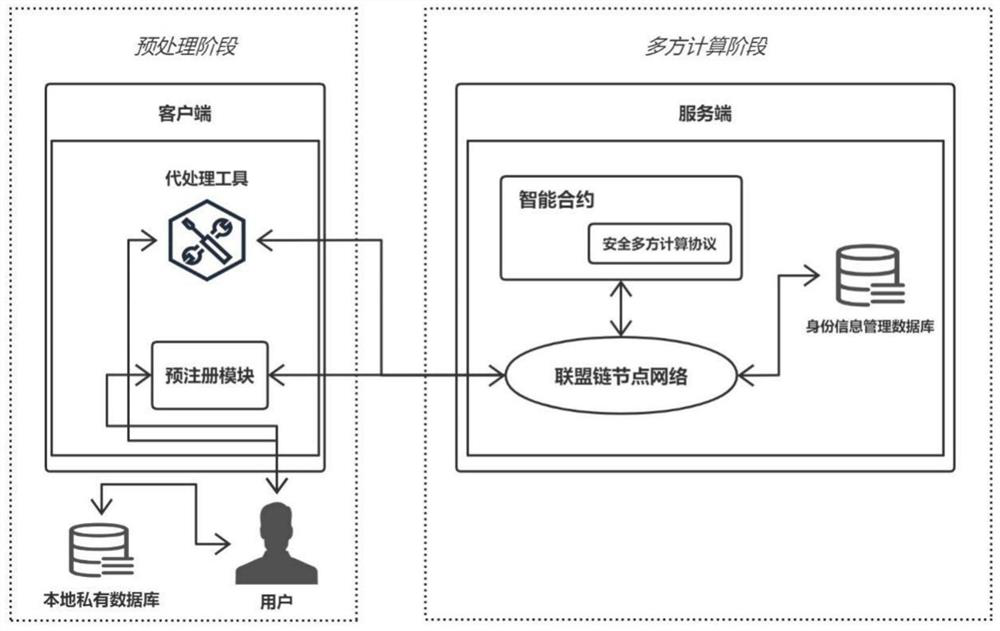
[0061] like figure 1 As shown, this embodiment elaborates on the privacy protection in the multi-party computing scenario empowered by the alliance chain. For example, in a multi-party voting scenario, voters who do not trust each other have needs such as identity information privacy protection, voting data privacy protection, and voting verification.
[0062] This embodiment describes the use of the method of the present invention to realize the anonymous security voting system in the alliance chain, including the following process:
[0063] Step 1: Voters preprocess the identity information to realize anonymous voting on the alliance chain, which specifically includes the following sub-steps:
[0064] Step 1.1: Each voter must present a certificate that can prove his true identity to the credential management agency, so as to obtain an authentication certificate. and each authenticated voter P i (i=1,2,...,n) will be assigned a processing tool AT i , thereafter, voter P ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com