User vulnerability analysis method oriented to social engineering attack
An analysis method and engineering technology, applied in neural learning methods, instruments, biological neural network models, etc., can solve problems such as difficult to meet the needs of network confrontation and low efficiency of attack methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
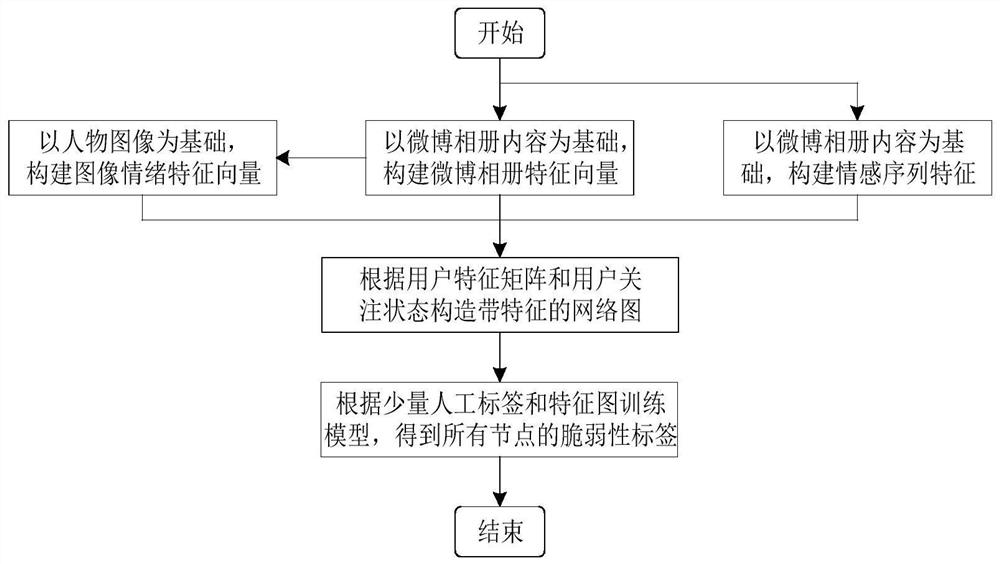
[0056] Such as figure 1 As shown, a user vulnerability analysis method for social engineering attacks, the steps are:
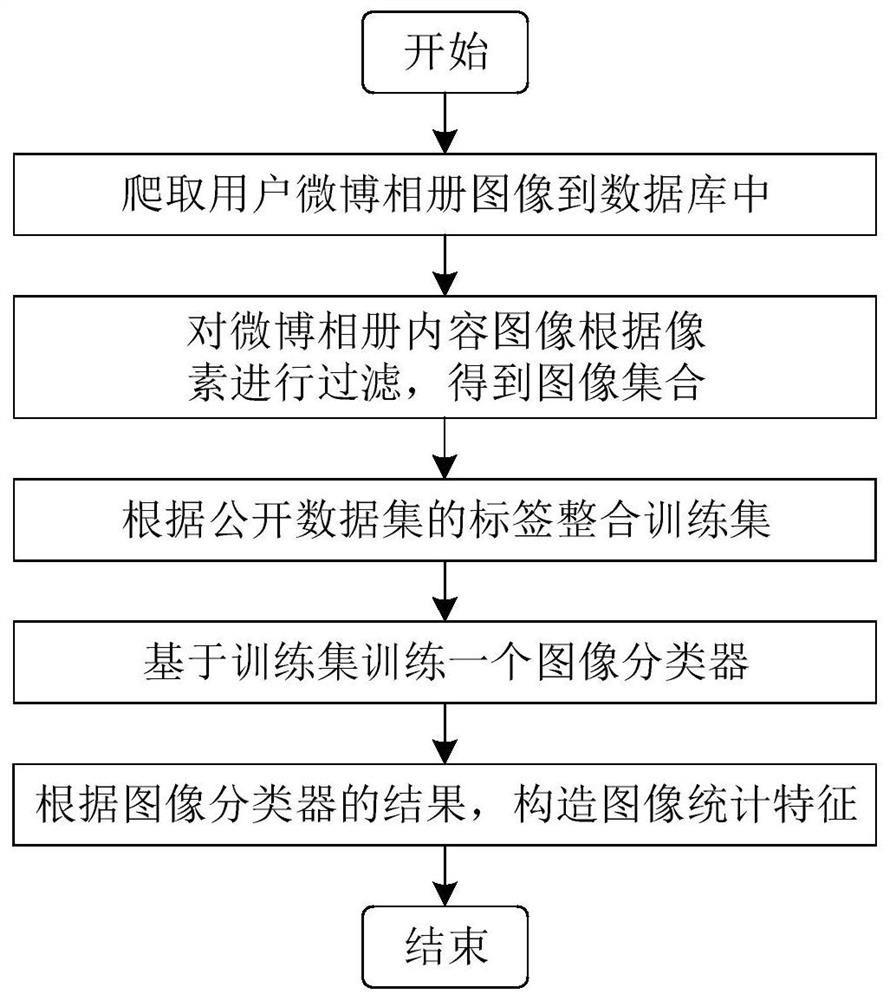
[0057] Step (1) Based on the content of the microblog album, the image classification algorithm is used to divide the images in the album into four categories: people, scenery, animals and animation, and the feature vector F of the microblog album is constructed by combining statistical methods 1 ;
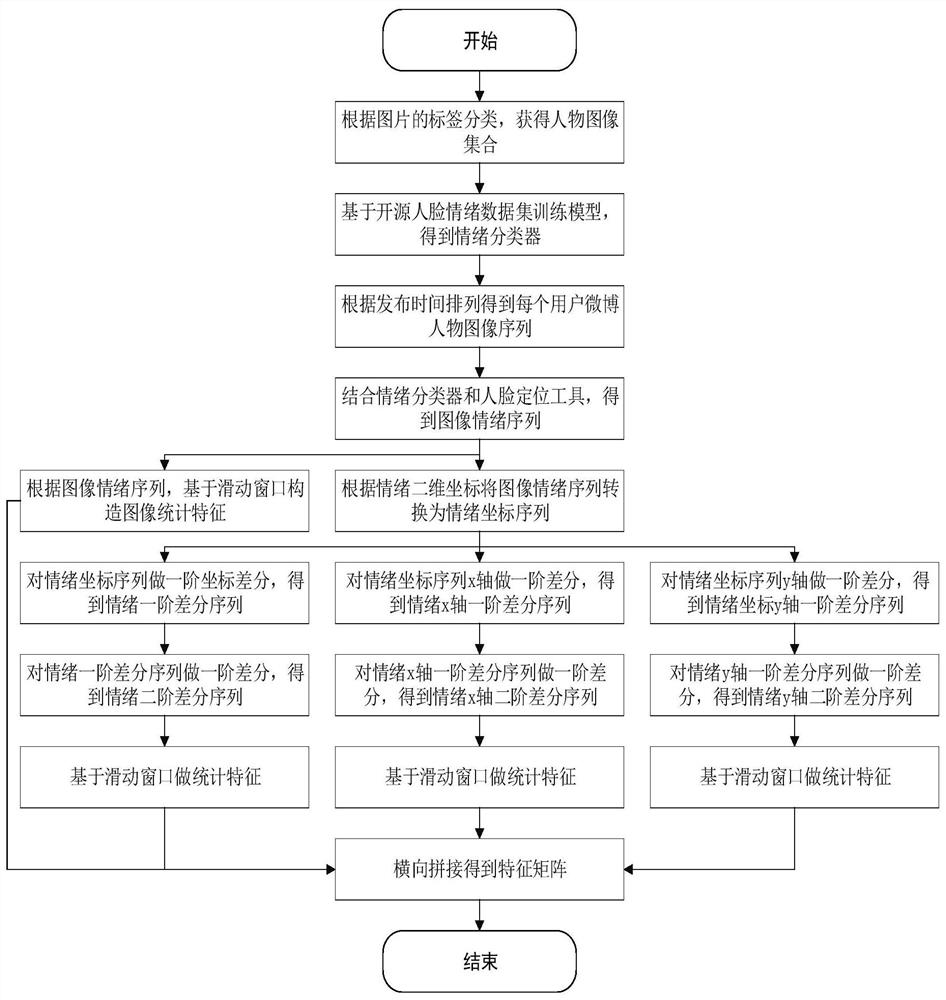
[0058] Step (2) Perform face positioning on the person image, extract the face image, perform facial emotion recognition on the face image, obtain the emotional sequence of each user according to the time sequence of the image, and construct the image by combining the emotional t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com