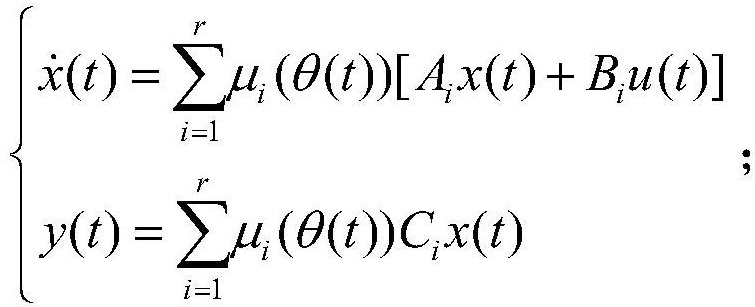Event-triggered DOFF quantization controller design method under spoofing attack
A spoofing attack and event-triggered technology, applied in the direction of adaptive control, general control system, control/regulation system, etc., can solve the problem of unstable T-S fuzzy system, save network bandwidth, and relieve the effect of assumption limitation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
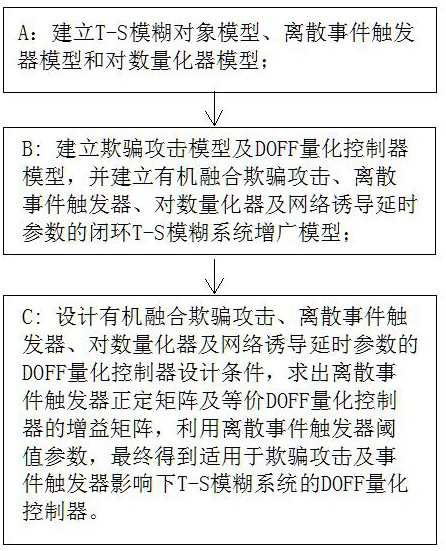
[0074] Below in conjunction with accompanying drawing and embodiment the present invention is described in detail:
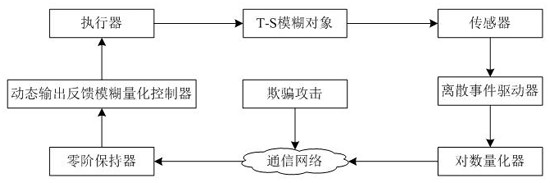
[0075] The event-triggered output feedback control of T-S fuzzy system under spoofing attack is as follows: figure 1 As shown in , the sensor periodically samples the measurement output of the T-S fuzzy object, the sensor sampled data is sent to the discrete event trigger, and the discrete event trigger judges whether the trigger condition is met: if it is satisfied, the sampled data is sent; otherwise, the sampled data is discarded. The quantizer quantifies the data sent by the discrete event trigger, and the quantized data is sent to the zero-order keeper through the communication network. The communication network is affected by spoofing attacks. The DOFF quantization controller receives the zero-order keeper data and calculates the control signal, and the actuator Adjust the T-S fuzzy object state according to the control signal.
[0076] Such as figure ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com