Data security protection method and device, medium and electronic equipment
A data security and security technology, applied in the fields of media and electronic equipment, devices, and data security protection methods, can solve problems such as hidden dangers of enterprise confidential information leakage, and achieve the effects of improving data security, eliminating leakage, and reducing development costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
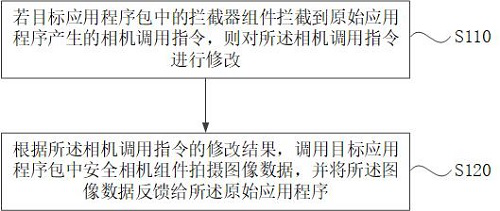
[0023] figure 1 It is a flow chart of a data security protection method provided in Embodiment 1 of the present application. This embodiment is applicable to the situation of using the office application to take pictures during the process of using the office application to work. The method can be executed by the data security protection device provided in the embodiment of the present application, the device can be realized by software and / or hardware, and can be integrated into the electronic device running the system.
[0024] Such as figure 1 As shown, the data security protection method includes:
[0025] S110. If the interceptor component in the target application package intercepts the camera call instruction generated by the original application program, modify the camera call instruction.
[0026] After the target application package is installed on the terminal device, the target application package is started. Specifically, the bootstrap component is started first...
Embodiment 2
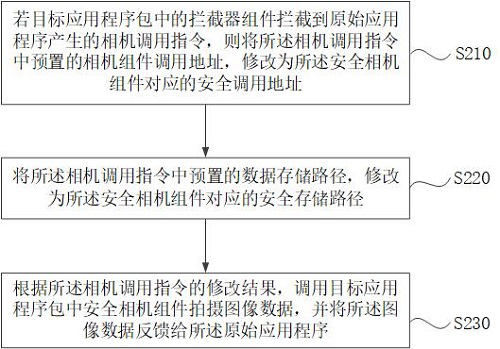
[0043] figure 2 It is a flow chart of another data security protection method provided in Embodiment 2 of the present application. This embodiment is further optimized on the basis of the foregoing embodiments. Specifically, the modification of the camera call instruction includes: modifying the camera component call address preset in the camera call instruction to the security call address corresponding to the security camera component; The data storage path preset in the instruction is modified to the security storage path corresponding to the security camera component.
[0044] Such as figure 2 As shown, the data security protection method includes:
[0045] S210. If the interceptor component in the target application package intercepts the camera call command generated by the original application program, modify the camera component call address preset in the camera call command to the security call corresponding to the security camera component address.
[0046] Am...
Embodiment 3
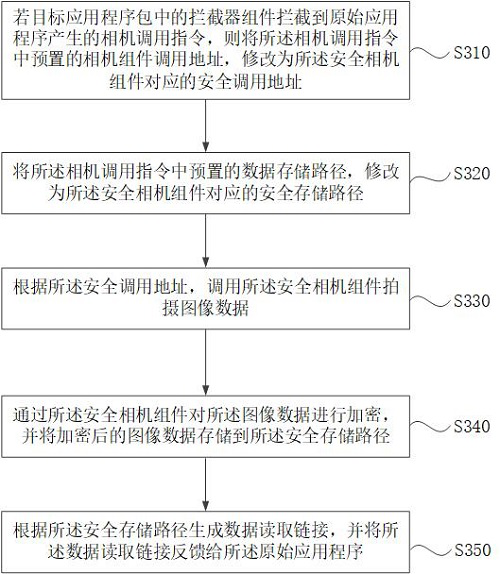
[0052] image 3 It is a flow chart of another data security protection method provided in Embodiment 3 of the present application. This embodiment is further optimized on the basis of the foregoing embodiments. The specific optimization is that, according to the modification result of the camera call instruction, call the security camera component in the target application package to capture image data, and feed the image data back to the original application program, including: according to the security call address, Calling the secure camera component to take image data; encrypting the image data through the secure camera component, and storing the encrypted image data in the secure storage path; generating a data read link according to the secure storage path , and feed back the data read link to the original application program.
[0053] Such as image 3 As shown, the data security protection method includes:
[0054] S310. If the interceptor component in the target ap...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com