Space crowdsourcing task allocation privacy protection method and system
A task allocation and privacy protection technology, applied in the field of spatial crowdsourcing privacy protection, can solve the problems of difficult task allocation, key management, user revocation and accountability cannot be well implemented, and meet the requirements of multi-user searchable encryption , Realize the effect of user revocation and accountability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
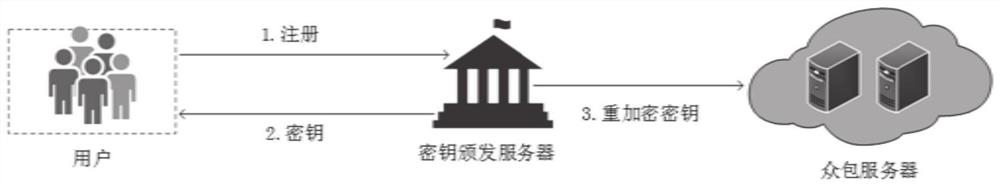
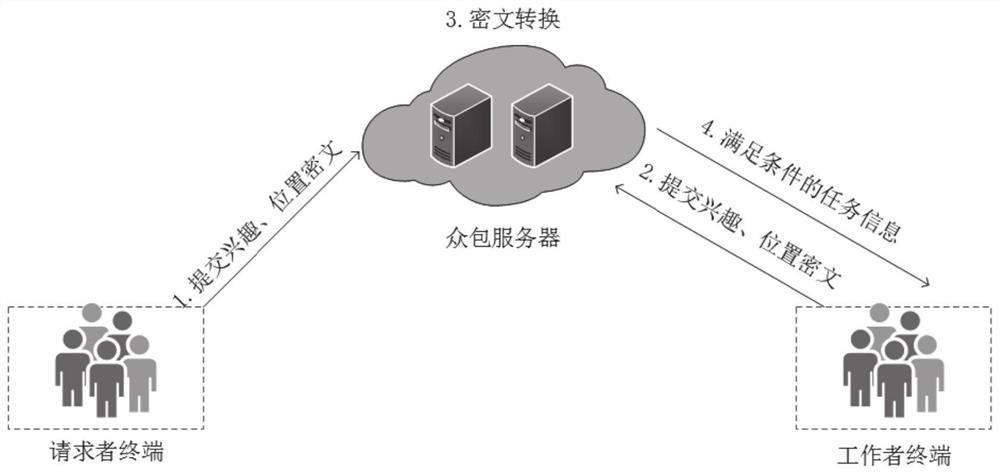
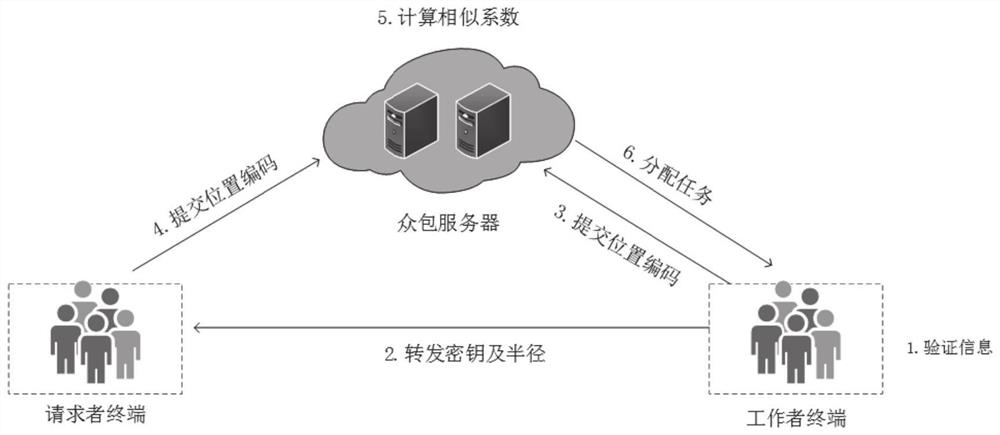
[0074] Embodiment one, such as Figure 1-3 As shown, this embodiment provides a privacy protection method for spatial crowdsourcing task assignment, which is applied to a requester terminal. The requester terminal sends a registration request to the key issuing server, and receives the task encryption key returned by the key issuing server; uses the task encryption key to encrypt the task message to obtain the ciphertext of the task message, and submits it to the crowdsourcing server; the receiving worker terminal Send the radius message (by verifying the signature, it can be proved that the worker is negotiating the radius with the requester), and after verifying its validity, upload the task location grid code set and the radius trapdoor to the crowdsourcing server; the receiving worker terminal The task result information sent, and the accountability information can be sent to the crowdsourcing server. It specifically includes the initialization phase, registration phase, ...
Embodiment 2
[0107] Embodiment two, such as Figure 1-3 As shown, this embodiment provides a privacy protection method for spatial crowdsourcing task assignment, which is applied to worker terminals. The worker terminal sends a registration request to the key issuing server, and receives the worker encryption key returned by the key issuing server; uses the worker encryption key to encrypt the worker message to obtain the ciphertext of the worker message, and submits it to the crowdsourcing server; After receiving the ciphertext of the requester's identity information sent by the crowdsourcing server and verifying its validity, upload the task worker grid code set and radius ciphertext to the crowdsourcing server; receive the final task information sent by the crowdsourcing server, and send Accountability information is sent to the crowdsourcing server or task result information is sent to the requester terminal. It specifically includes the initialization phase, registration phase, encry...
Embodiment 3
[0140] Embodiment three, such as Figure 1-3 As shown, this embodiment provides a privacy protection method for spatial crowdsourcing task allocation, which is applied to crowdsourcing servers. The crowdsourcing server receives the task re-encryption key and the worker re-encryption key of the key issuing server, the task message ciphertext of the requester terminal and the worker message ciphertext of the worker terminal, and obtains by re-encryption and inner product calculation The requester’s identity information that satisfies the worker’s requirements, encrypts and signs the requester’s identity information and forwards the ciphertext of the requester’s identity information to the worker’s terminal; receives the requester’s terminal’s task position grid code set and radius trapdoor , and the worker grid encoding set and radius ciphertext of the worker terminal, and after verification and intersection calculation, the final task information is obtained and sent to the wor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com