Permission transfer method and system for digital key offline condition of trusted execution environment
A digital key and execution environment technology, applied in digital transmission systems, services based on specific environments, transmission systems, etc., to ensure privacy and security, and resist man-in-the-middle attacks and replay attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0064] According to a trusted execution environment digital key offline authority transfer method provided by the present invention, comprising:
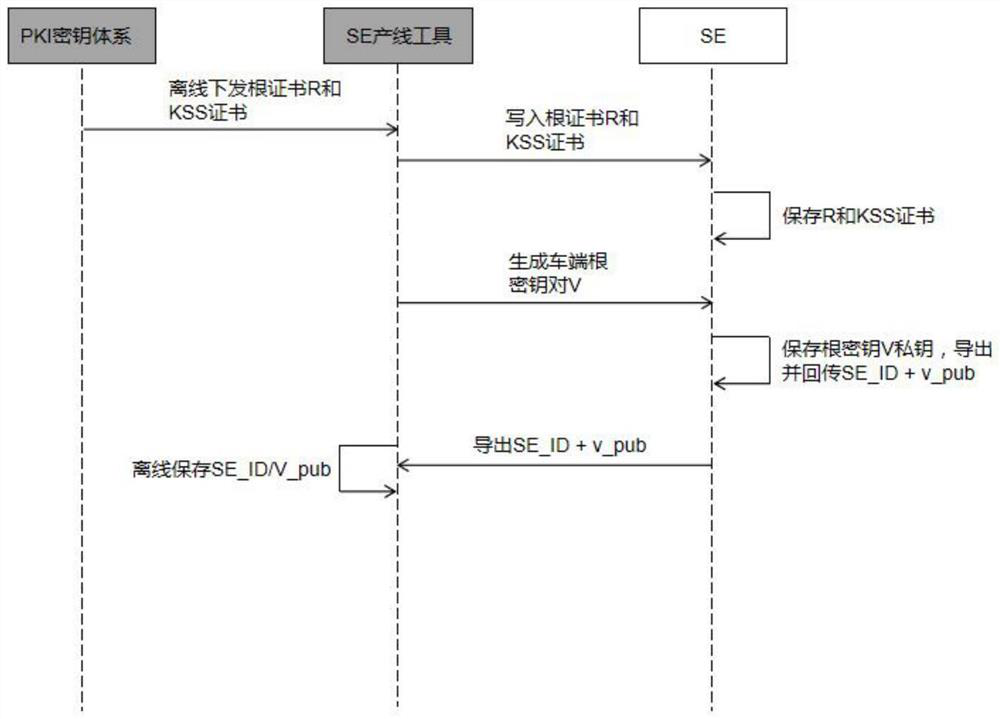
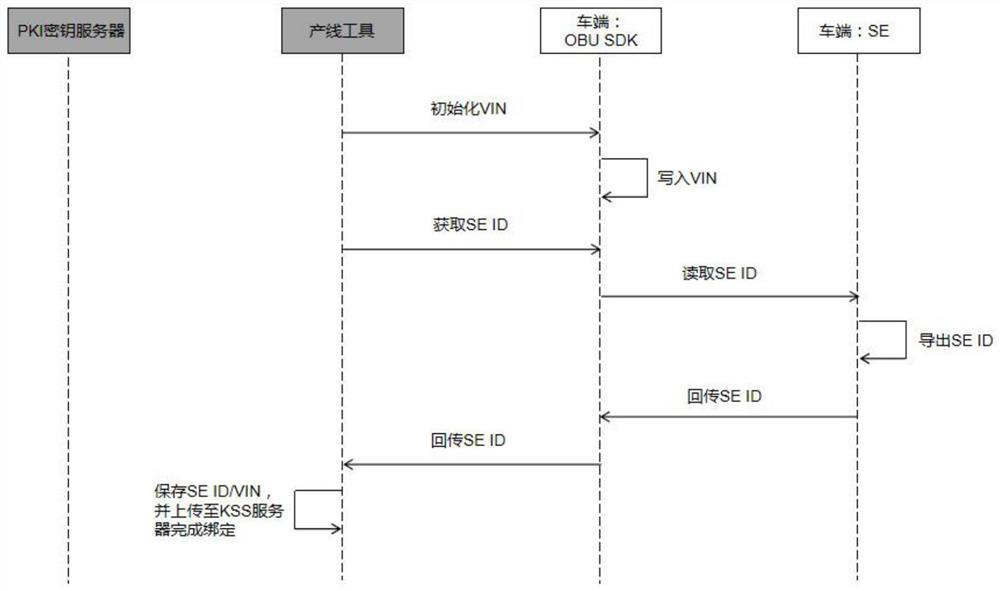
[0065] Step S1: Import the cloud root key and vehicle identification code at the vehicle-end production line stage, bind the vehicle identification code with the SE ID, and fill the SE with the root certificate to generate the vehicle-end root key;
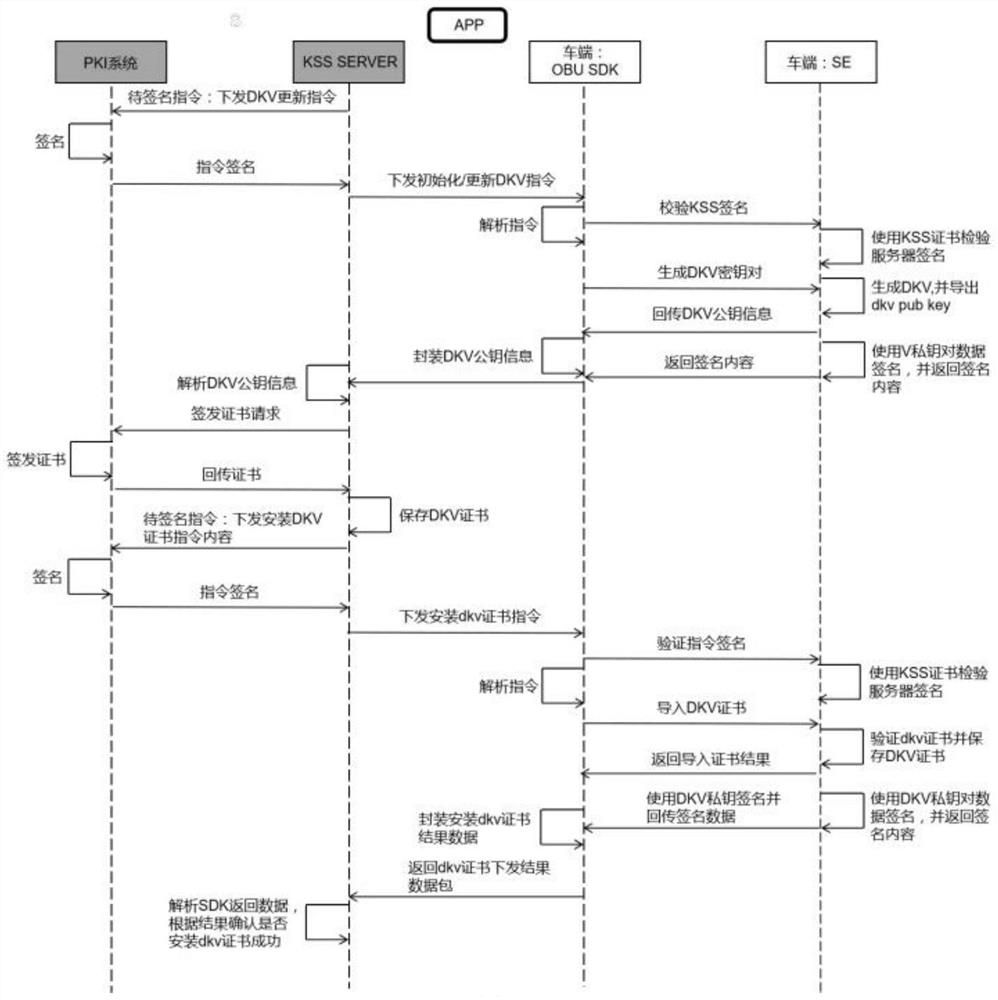
[0066] Step S2: Generate the car-end digital key key based on the car-end root key and derive the car-end digital key key;
[0067] Step S3: Generate a mobile phone digital key key, and authenticate the generated mobile phone digital key key with the vehicle digital key key;
[0068] Step S4: Through the trusted execution environment and the technical characteristics of the trusted clock, based on the generated car-end root key and the car-end digital key, the authority transfer of the digital key under offline conditions is realized.
[0069] Specifically, the step S1 adopts:
[0070...
Embodiment 2
[0091] Embodiment 2 is a preferred example of embodiment 1
[0092] The technical problems to be solved by the present invention include: designing a digital key authority transfer protocol in related offline scenarios to ensure the privacy and integrity of digital keys, and designing a trusted clock in offline scenarios to ensure that authority is withdrawn within a specified time.
[0093] People often pass through road sections without network while driving, and dual offline requires that the required functions (opening and closing locks, key sharing and recovery, etc.) can be completed even when the car terminal and mobile terminal are both offline. For opening and closing the lock, the digital key has been authorized and authenticated, and it only needs to be opened and closed after the Bluetooth connection or NFC connection. However, if you want to hand over the digital key to a third party and continuously control it, you cannot use the cloud to obtain friends’ public k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com