Network security control method and device for industrial control system
An industrial control system and network security technology, which is applied in the field of network security control methods and devices of industrial control systems, can solve the problems of too strict network security protection of industrial control terminals, failure to meet security protection requirements, and reduced network security protection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
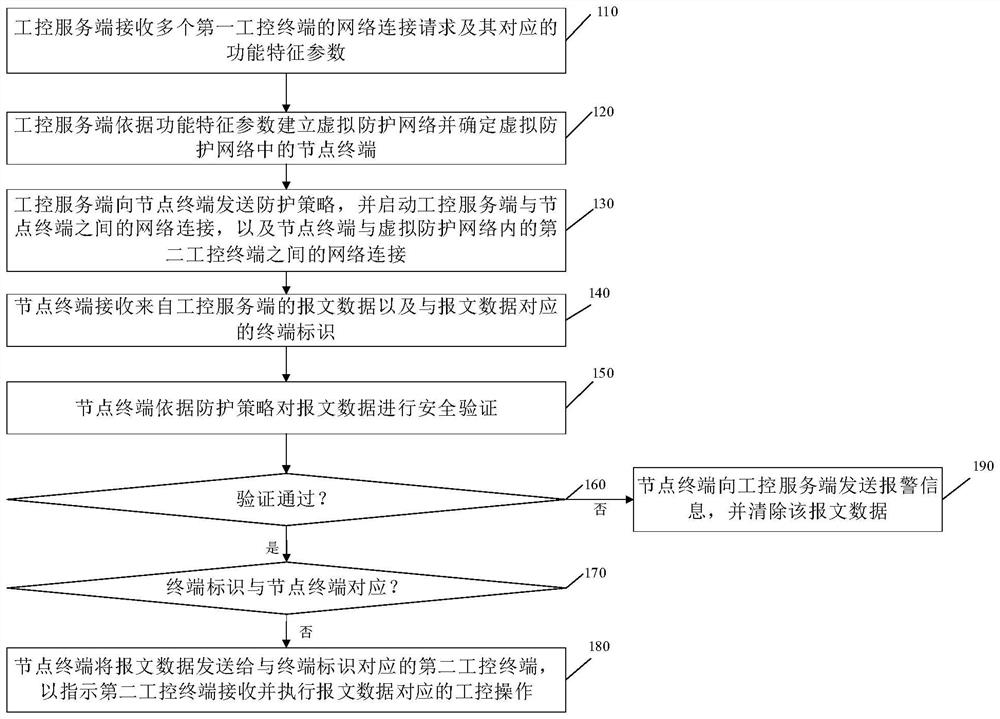
[0046] Such as figure 1 As shown, the network security control method of the industrial control system provided by the present application includes the following steps:
[0047] S110: The industrial control server receives network connection requests from a plurality of first industrial control terminals and corresponding functional characteristic parameters.
[0048] In this application, the network security control device of the industrial control system includes an industrial control server and at least one industrial control terminal. The industrial control server performs configuration, maintenance and other operations based on the industrial control host connected to it. Each industrial control terminal is a terminal device with processor function.
[0049] The control object is the target object that needs to be controlled by the industrial control terminal, including but not limited to steel industry, petroleum, chemical industry and other industrial control objects, ...
Embodiment 2
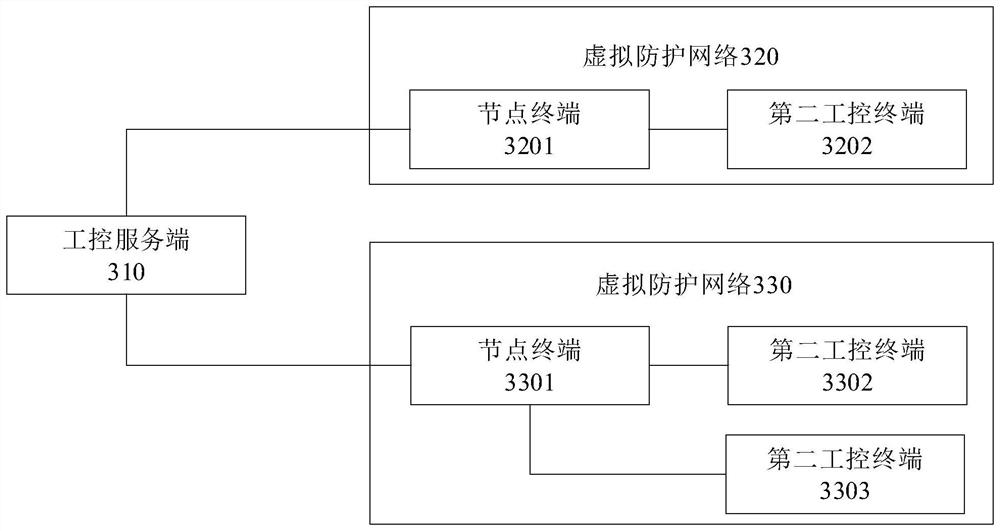
[0095] Such as image 3 As shown, the network security control device of the industrial control system provided by this application includes an industrial control server 310 and a plurality of virtual protection networks (such as image 3 320-330 in ), the industrial control server 310 is connected to multiple virtual protection networks respectively.
[0096] Each virtual protection network includes a node terminal (such as image 3 3201, 3301 in ) and at least one second industrial control terminal (such as image 3 3202, 3302-3303), the node terminals are respectively connected to at least one second industrial control terminal network.
[0097] The node terminal includes a protection strategy, and the node terminal performs security verification on the message data transmitted by the industrial control server according to the protection strategy, and transmits the verified message data to the second industrial control terminal in the same virtual protection network.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com