SQL injection statement analysis method based on tree structure
An analysis method and tree structure technology, applied in special data processing applications, instruments, platform integrity maintenance, etc., can solve problems such as inability to effectively and accurately analyze key information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
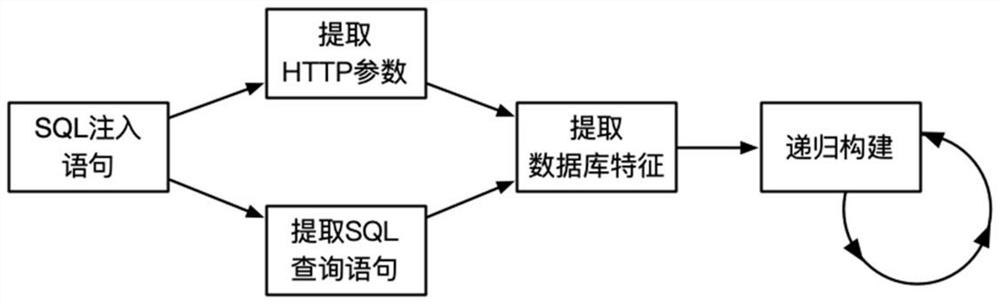
[0020] Such as figure 1 As shown, a tree-structure-based SQL injection statement parsing method of the present invention, through pre-steps such as extracting HTTP parameters, extracting SQL query statements, and extracting database features, then recursively builds a hierarchical tree, so that the processing flow of the SQL injection statement It is more optimized and the analysis results are more fine-grained. Specifically include the following steps:
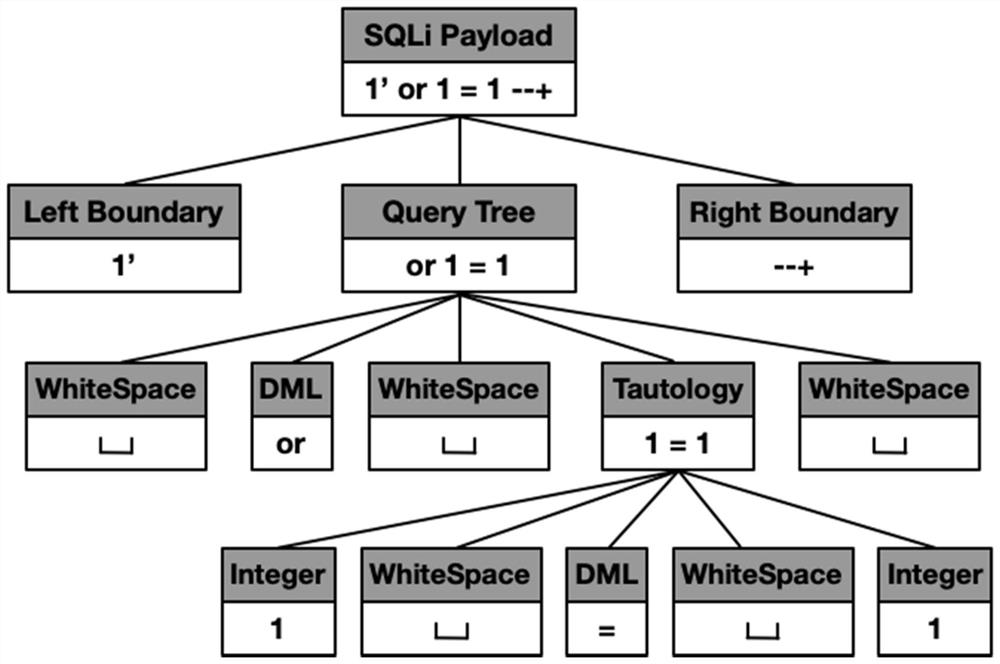
[0021] (1) The SQL injection statement S is [1'or 1=1--+], including the left HTTP parameter [1'], the middle SQL query statement [or 1=1], and the right HTTP parameter [--+] three parts. First extract its HTTP parameters, that is, extract the content that plays an auxiliary role for SQL injection according to its semantics. Specifically, the leftmost and rightmost contents in the SQL injection statement are named S BL ,S BR .
[0022] (2) Extract the SQL query statement in the SQL injection statement, that is, the middl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com