Encryption method and system for communication between mobile terminal and vehicle
A mobile terminal and vehicle communication technology, applied in the field of vehicle communication, can solve problems such as information security issues that have not been considered
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
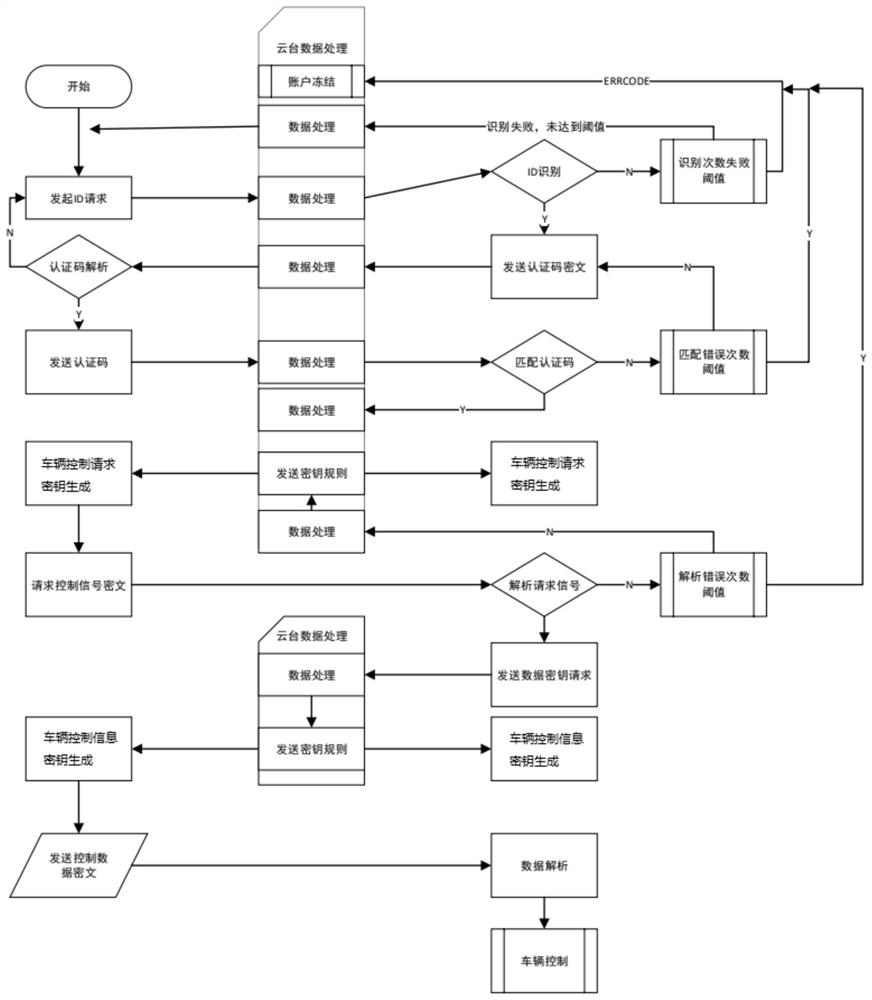
[0033] Such as figure 1 As shown, the public network cloud platform module corresponds to the cloud platform data processing, the left side is the mobile terminal information processing flow, and the right side is the vehicle computer processing flow. An encryption method for communication between a mobile terminal and a vehicle, comprising the following steps:
[0034] (1) The mobile terminal initiates an identification request;
[0035] (2) After successful identification, the public network cloud platform processes the ciphertext of the authentication code generated by the vehicle computer and delivers it to the mobile terminal, and the mobile terminal sends the analyzed vehicle authentication code to the vehicle computer through the public network cloud platform;
[0036] (3) The vehicle computer performs matching after receiving the vehicle authentication code. If the matching is successful, a key generation request is initiated, and if the matching fails, an error messa...
Embodiment 2
[0052] An encryption system for communication between a mobile terminal and a vehicle, including a mobile terminal module, a vehicle computer module and a public network cloud platform module, such as figure 1 As shown, the public network cloud platform module corresponds to the cloud platform data processing, the left side of which is the information processing flow of the mobile terminal module, and the right side is the processing flow of the vehicle computer module.
[0053]The mobile terminal module implements user operations and initiates an identification request. After the identification is successful, it sends the analyzed vehicle authentication code to the vehicle computer. After the public network cloud platform issues the vehicle control request key rule, the mobile terminal passes the control request signal through the encrypted key. The key is encrypted and sent to the vehicle computer. After the public network cloud platform publishes the vehicle control informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com