Intelligent data checking method, device and equipment
A data and intelligent technology, applied in the field of data processing, can solve problems such as high cost, incomplete data coverage, and heavy workload of manually writing check scripts, and achieve the effect of many check rules and low input cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
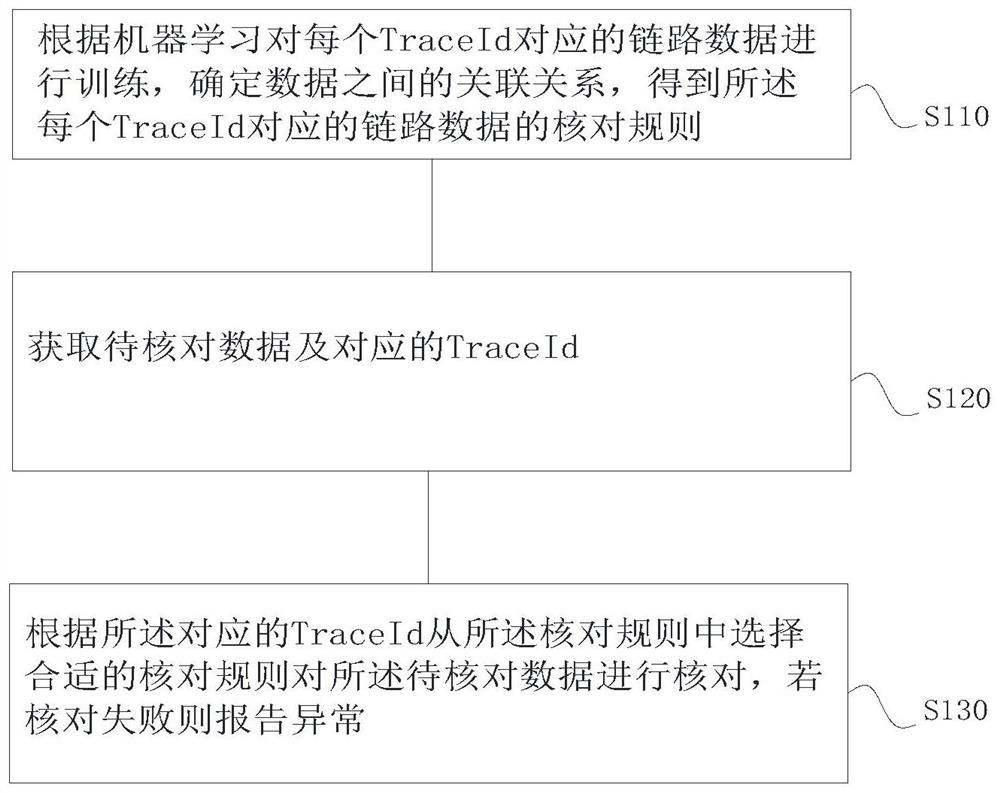
[0044] Such as figure 1 As shown, a method for intelligent data checking, comprising the following steps:
[0045] S110. Train the link data corresponding to each TraceId according to machine learning, determine the association relationship between the data, and obtain the checking rules of the link data corresponding to each TraceId;
[0046] S120. Obtain the data to be checked and the corresponding TraceId;
[0047] S130. Select an appropriate verification rule from the verification rules according to the corresponding TraceId to verify the data to be verified, and report an exception if the verification fails.
[0048]According to implementation 1, when the software is tested, a unique TraceId will be generated following the request sent out, and the TraceId will accompany the request from beginning to end, recording the complete call link during the request execution process, which can be used for logs For information query and positioning, add a field to record TraceId ...
Embodiment 2
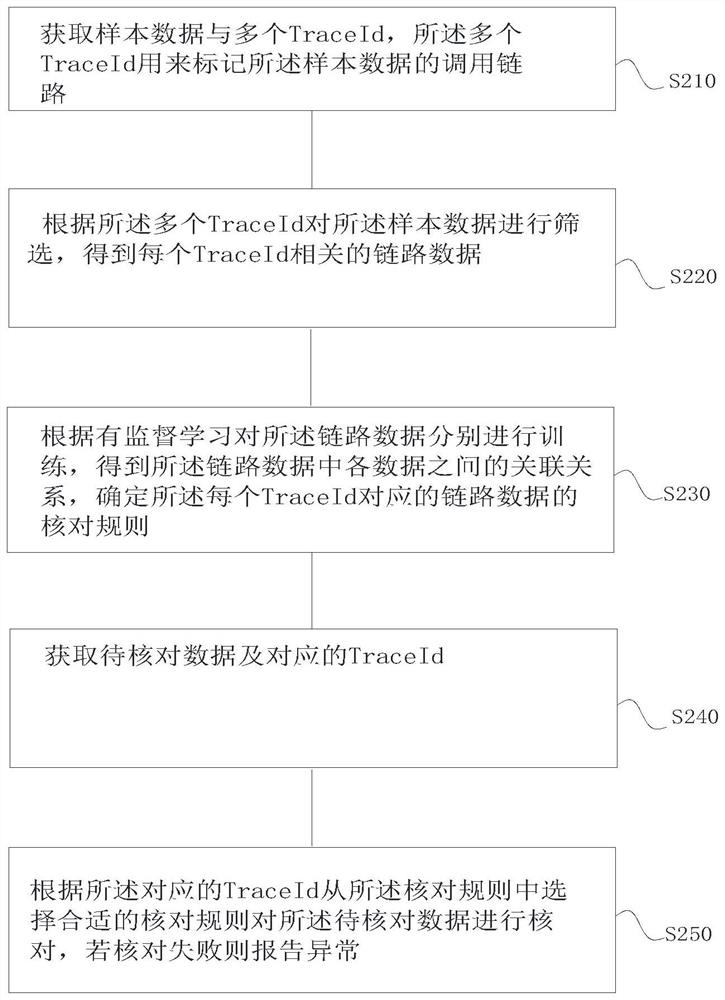
[0050] Such as figure 2 As shown, a method for data intelligent verification includes:
[0051] S210. Obtain sample data and multiple TraceIds, where the multiple TraceIds are used to mark the calling link of the sample data;
[0052] S220. Filter the sample data according to the multiple TraceIds to obtain link data related to each TraceId;
[0053] S230. Perform training on the link data according to supervised learning, obtain the association relationship between the data in the link data, and determine the checking rules of the link data corresponding to each TraceId;
[0054] S240. Obtain the data to be checked and the corresponding TraceId;
[0055] S250. Select an appropriate verification rule from the verification rules according to the corresponding TraceId to verify the data to be verified, and report an exception if the verification fails.
[0056] According to Example 2, under the trend of microservices, the log information of a call is distributed in different...
Embodiment 3
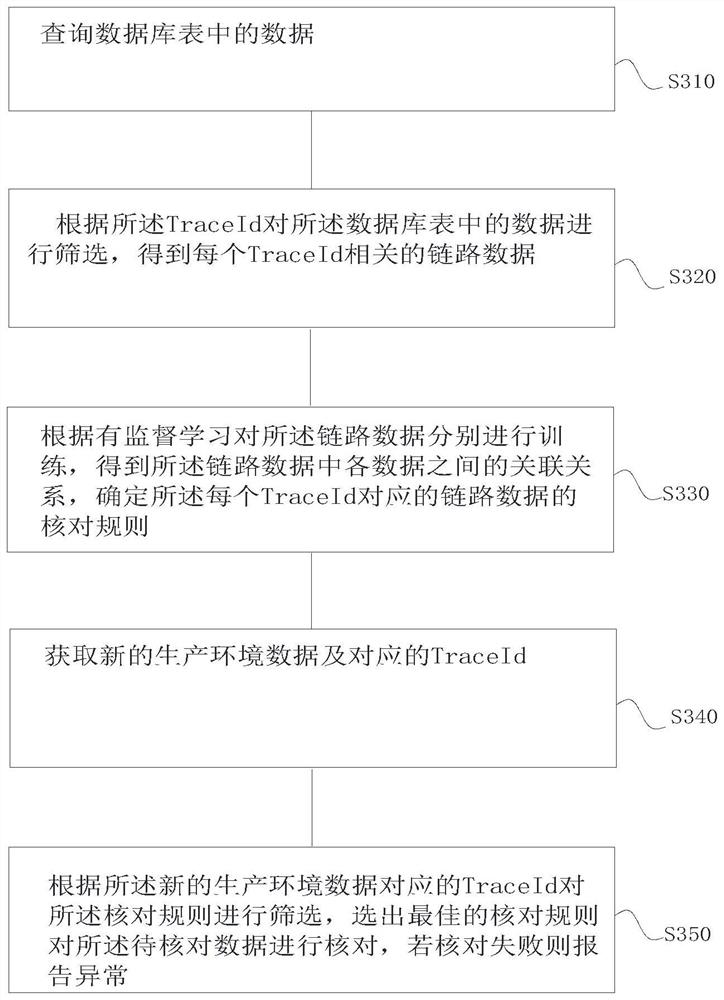
[0058] Such as image 3 As shown, a specific implementation method can be:
[0059] S310. Query the data in the database table;
[0060] The backend interface generates a unique TraceId for each call, and passes it down as the context, so that the entire call chain can be connected through the TraceId, and at the same time, a field for recording the TraceId is added to each table in the database. , the TraceId is also stored in the library, so that the link data can be associated through the TraceId, the data in all tables of all databases can be queried as sample data, and all TraceIds can be intercepted from it.
[0061] S320. Filter the data in the database table according to the TraceId to obtain link data related to each TraceId;
[0062] Use TraceId to filter the query results, that is, filter the sample data through TraceId to get all the data under one call, that is, the link data corresponding to each TraceId, and use it as training data.
[0063] S330. Perform tra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com