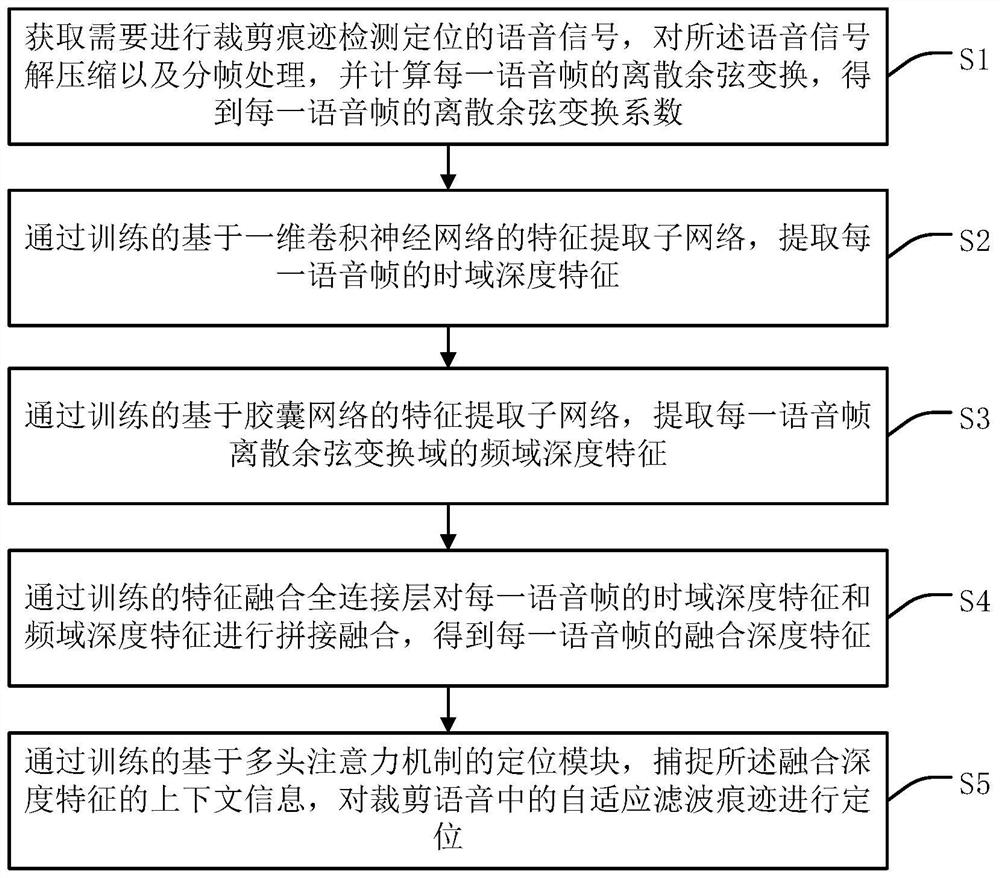
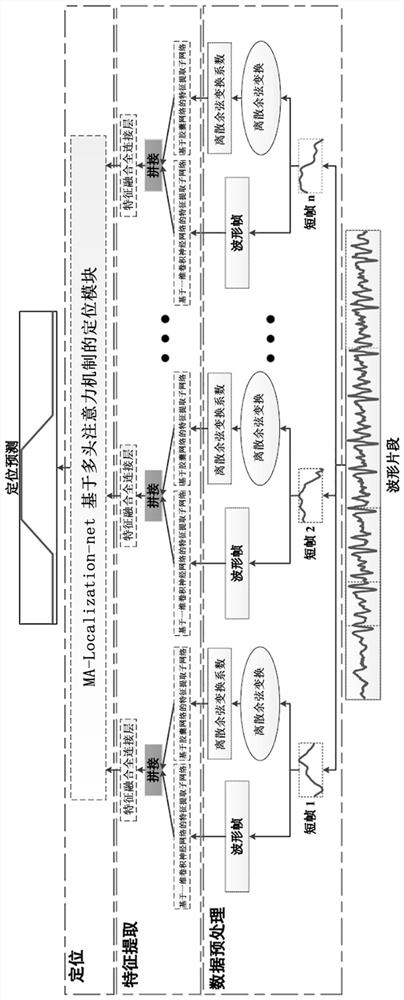
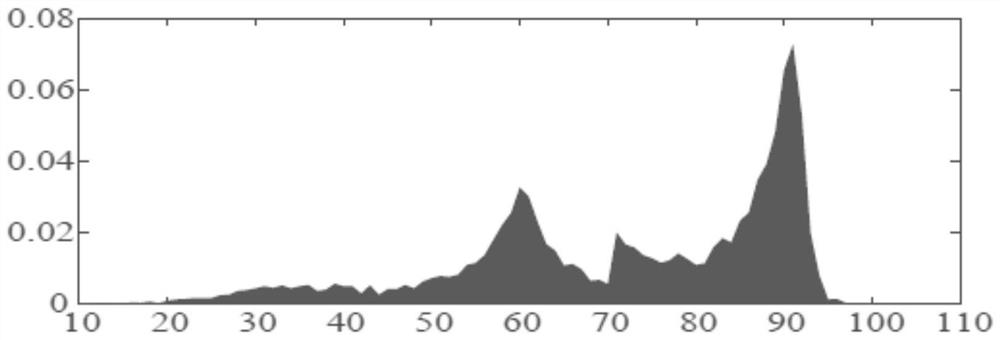
Voice cutting trace positioning method based on double-domain depth features and attention mechanism
A technology of deep features and localization methods, applied in speech analysis, instruments, etc., can solve the problem that there is no good method to detect clipping marks and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] In order to make the object, technical solution and advantages of the present invention more clear and definite, the present invention will be further described in detail below with reference to the accompanying drawings and examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
[0064] In recent years, the emergence of digital audio editing software has enabled some users who do not have knowledge of speech signal processing to easily process digital audio, so digital audio editing software has attracted a large number of users. With these convenient audio editing software, criminals can easily delete some words in a recording to generate fake voices with completely different semantics. These fake voices are very likely to be used as evidence in court, or spread among the general public, causing a series of security issues.
[0065] In the prior art, detecting ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com