Detection equipment authentication method, detection equipment authentication device and electronic equipment
A technology of detection equipment and authentication method, applied in the field of information security, can solve problems such as data leakage of automobile manufacturers, irregular use of automobile diagnostic equipment, and failure to obtain the authorization of the diagnosed automobile, so as to reduce the risk of leakage and standardize the use of the effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057]In the following description, specific details such as specific system structures and technologies are presented for the purpose of illustration rather than limitation, so as to thoroughly understand the embodiments of the present application. It will be apparent, however, to one skilled in the art that the present application may be practiced in other embodiments without these specific details. In other instances, detailed descriptions of well-known systems, devices, circuits, and methods are omitted so as not to obscure the description of the present application with unnecessary detail.
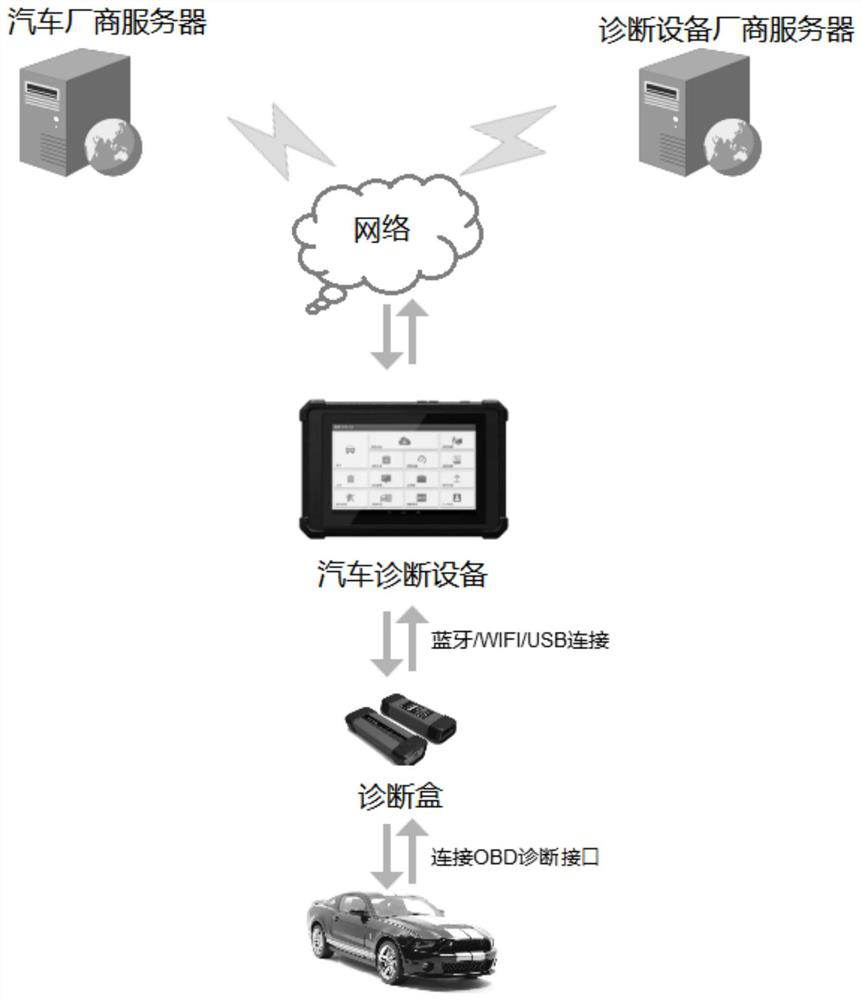
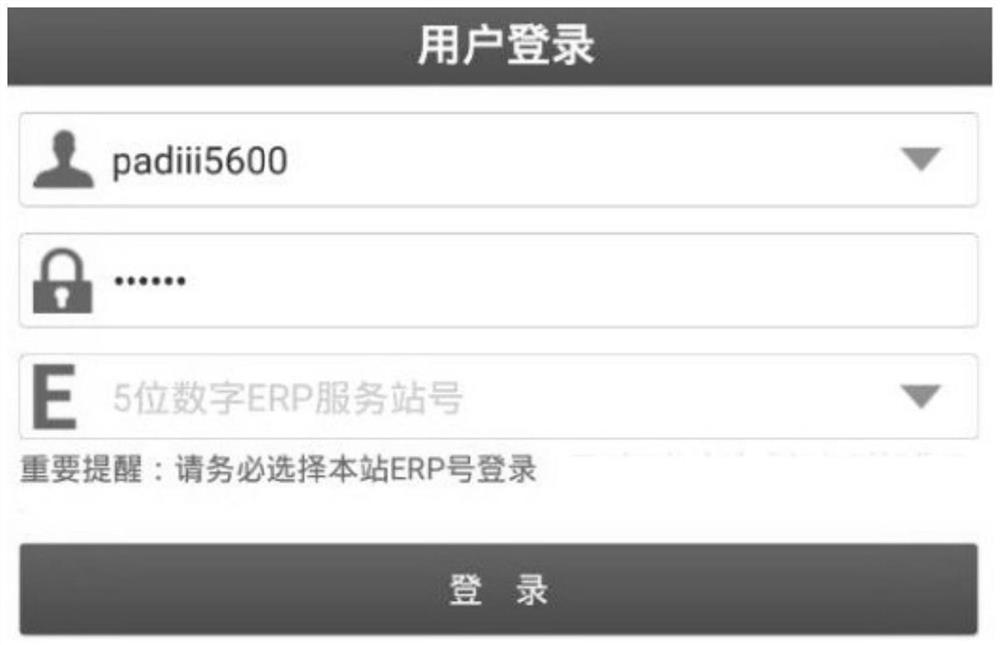
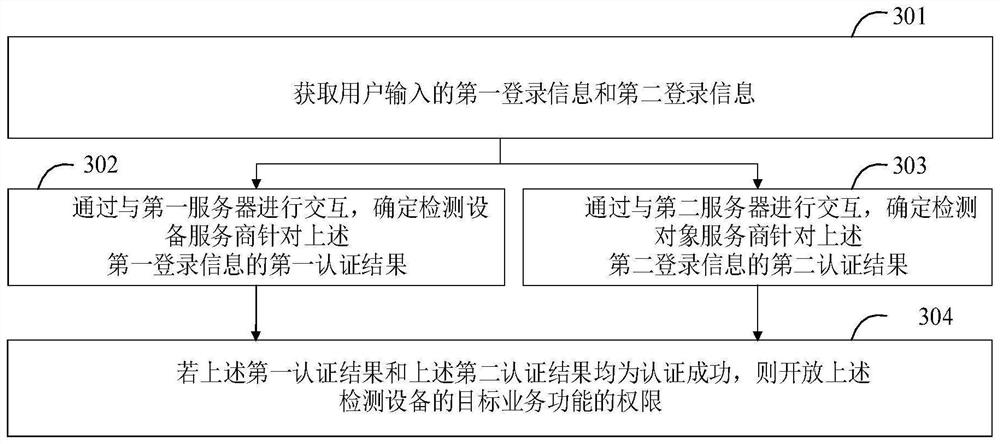
[0058] Currently, cars and car diagnostic equipment are often not produced by the same manufacturers. When a car breaks down and needs to be diagnosed, the car owner usually drives the car to a car sales service 4S store. In the prior art, when the staff of the 4S shop uses the vehicle diagnostic equipment, they only need to input the user name and password, and then the server of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com