Method for constructing hash function with secret key based on chaotic neural network and enhanced iterative structure
A neural network and iterative structure technology, applied in the field of application cryptography, can solve problems such as security loopholes, and achieve the effect of improving security, improving collision resistance, and enhancing practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] The present invention will be described in detail below with reference to the accompanying drawings and embodiments.
[0053] Embodiment symbol description
[0054]
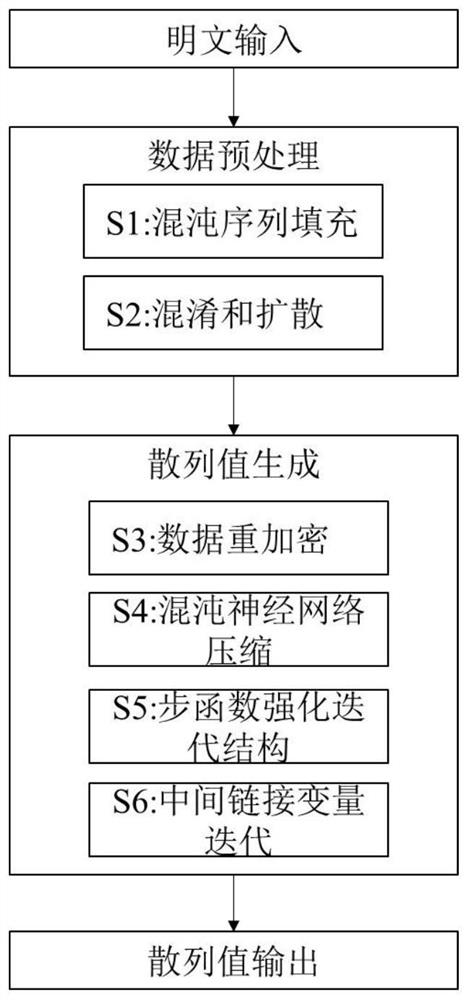
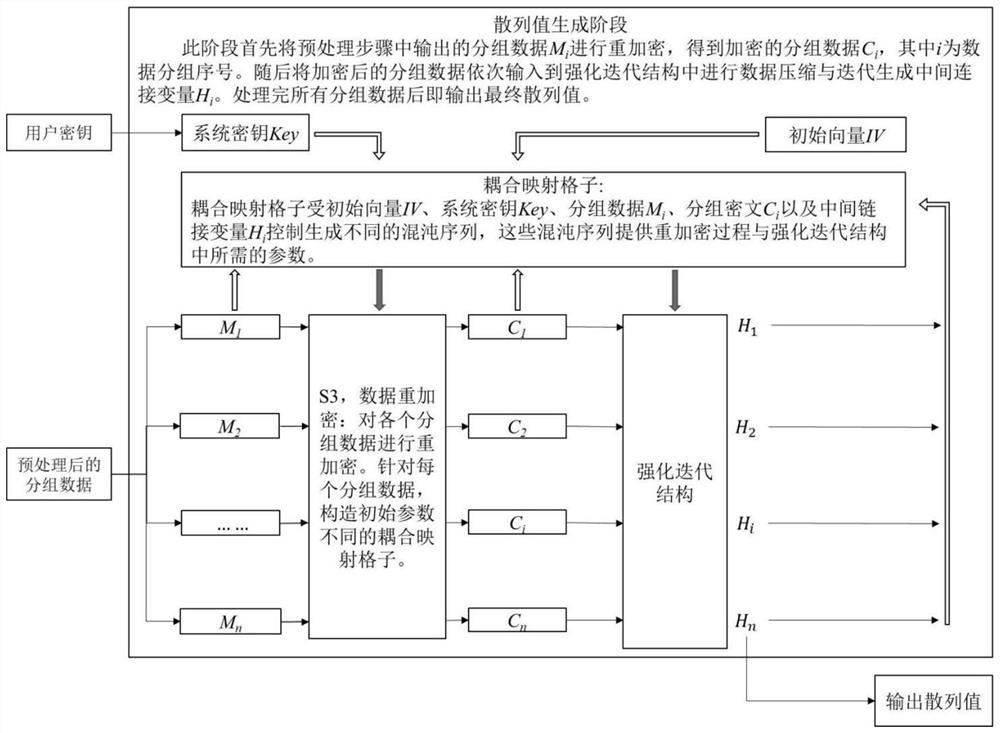
[0055] Such as figure 1 As shown, based on the construction method of the keyed hash function based on the chaotic neural network and the enhanced iterative structure, the hash function proposed by the present invention has 6 processing steps in total, wherein step S1 and step S2 are preprocessing stages, and plaintext filling and Plaintext encryption; Steps S3-S6 are the hash value generation stage of the hash function, performing data grouping, re-encryption, compression and iteration.
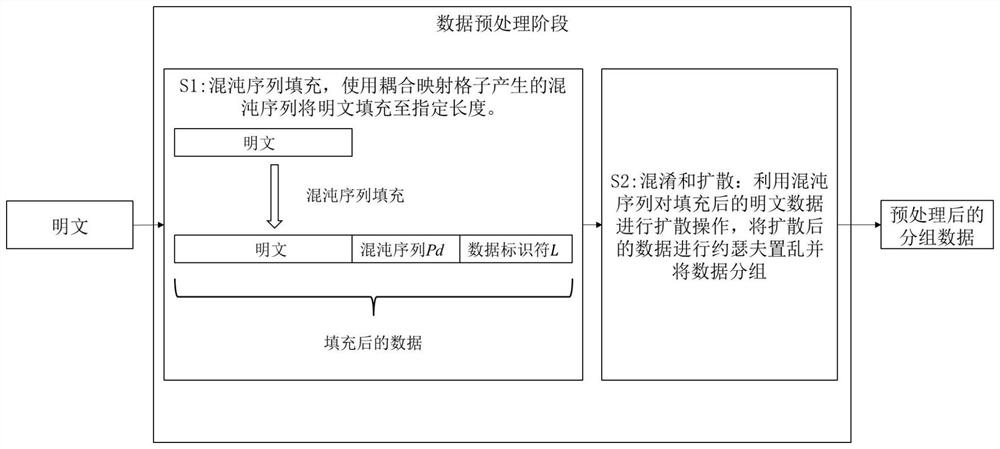
[0056] Such as figure 2 As shown, it is the data preprocessing stage of the present invention. The purpose of this stage is to fill and encrypt the plaintext for processing in subsequent steps, including step S1 and step S2; at this stage, first use the chaotic sequence to fill the plaintext data; filling method s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com