System call white list generation method for interpreted language source program
An interpreted language, source program technology, applied in program control devices, creation/generation of source code, software engineering design, etc., can solve problems such as inability to cover branches, system calls cannot be analyzed, etc., to achieve the effect of enhancing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
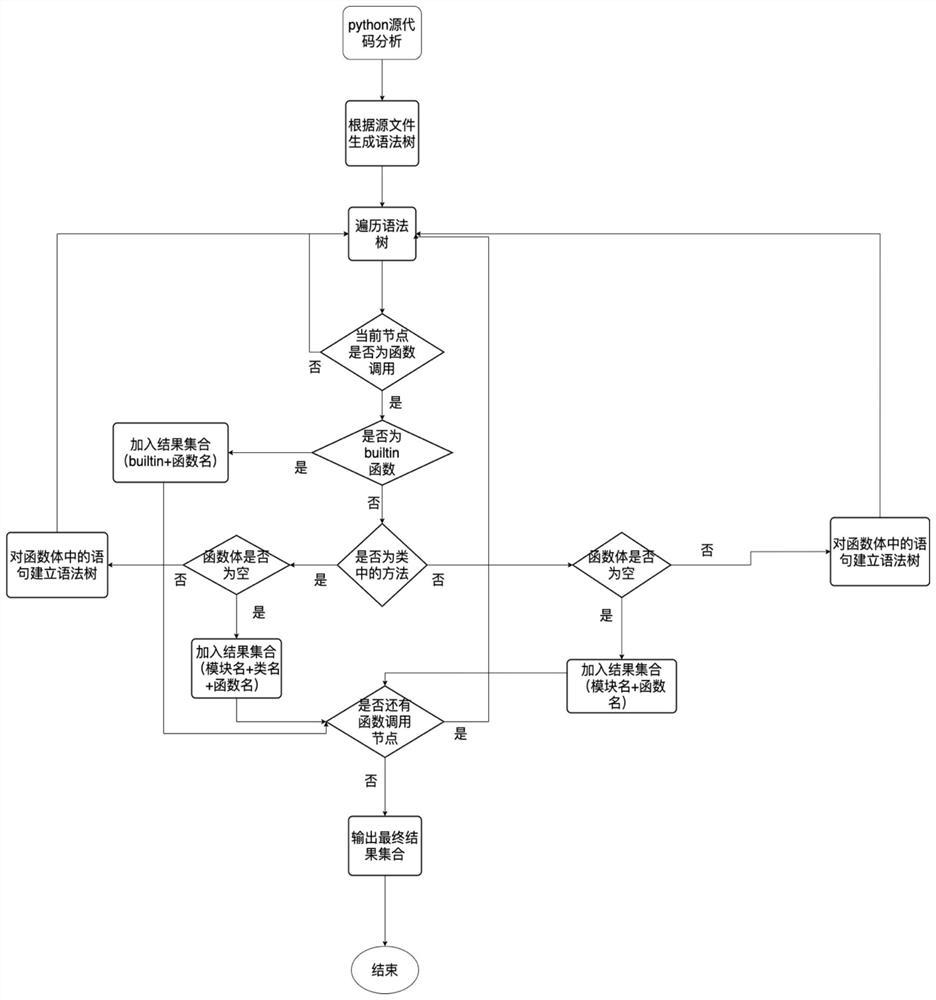
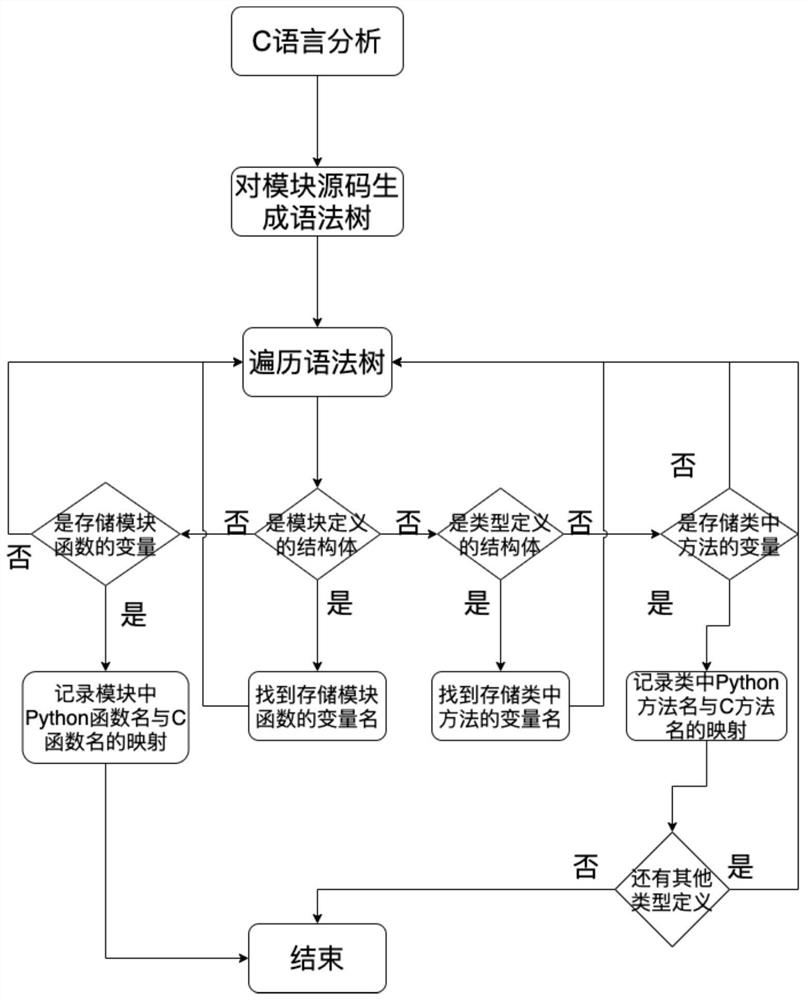
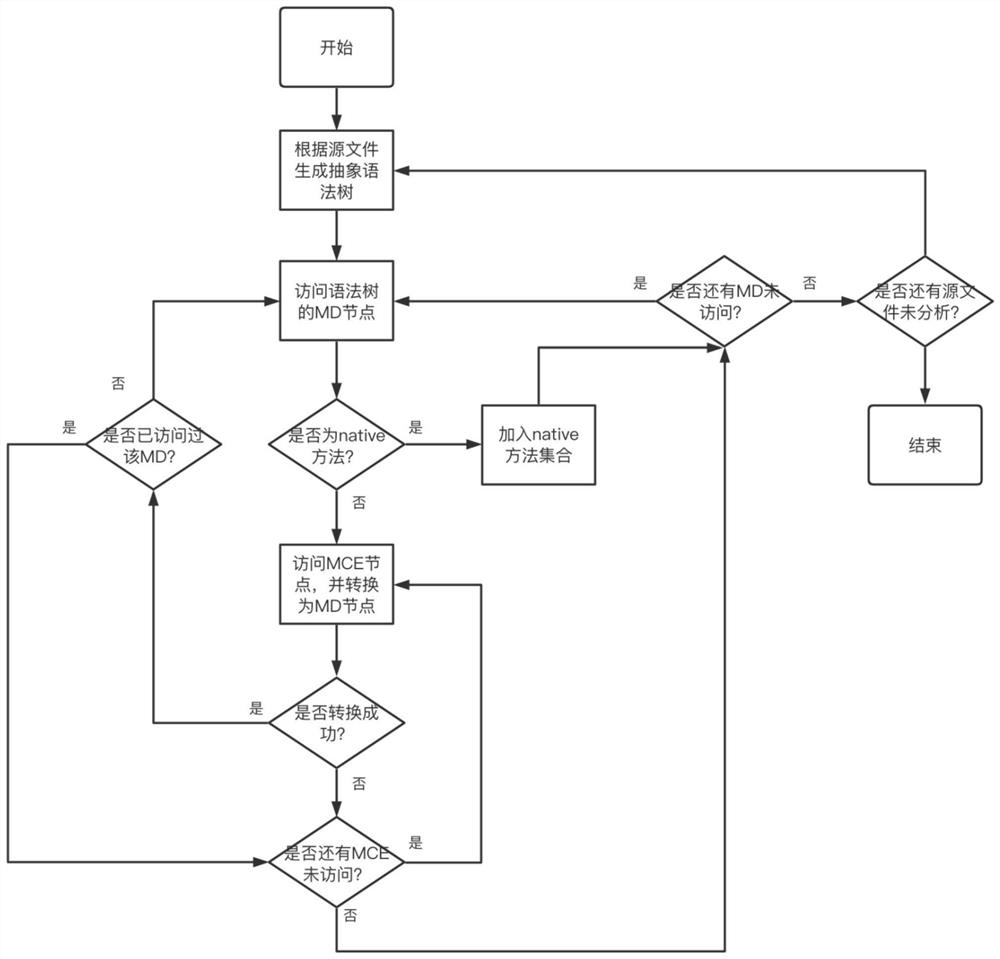
[0039] The Python system call analysis part has three main parts. Python source program analysis, C source program analysis, and binary file analysis. The Python version used in the experiments is Python 3.6.
[0040] Python source program analysis
[0041] Python source program analysis process such as figure 1 shown. In order to find out the function written in C used in the source file, we need to visit each function call node on the syntax tree, and use the inference function of astroid to infer the relevant information of the function call. If the function is a builtin function, then directly It is added to the result set in the form of "builtin + function name"; if the function is a method in a certain class, it is also necessary to judge whether its function body in the syntax tree is empty, if it is empty, it indicates that it is in C language The function written, this type of function also needs to be added to the result set, in the form of "module name + class n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com