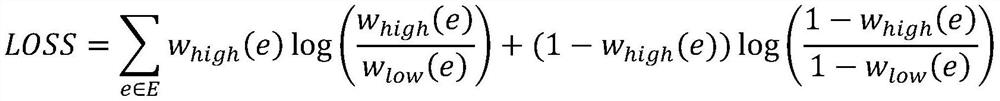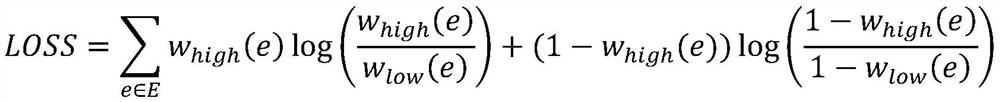Manifold-based attack identification method for dimension reduction and clustering of network data packet features
A network data packet and attack identification technology, applied in the information field, can solve the problems of dimension disaster, direct distance and geodesic distance deviation, etc., and achieve the effect of less data samples
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
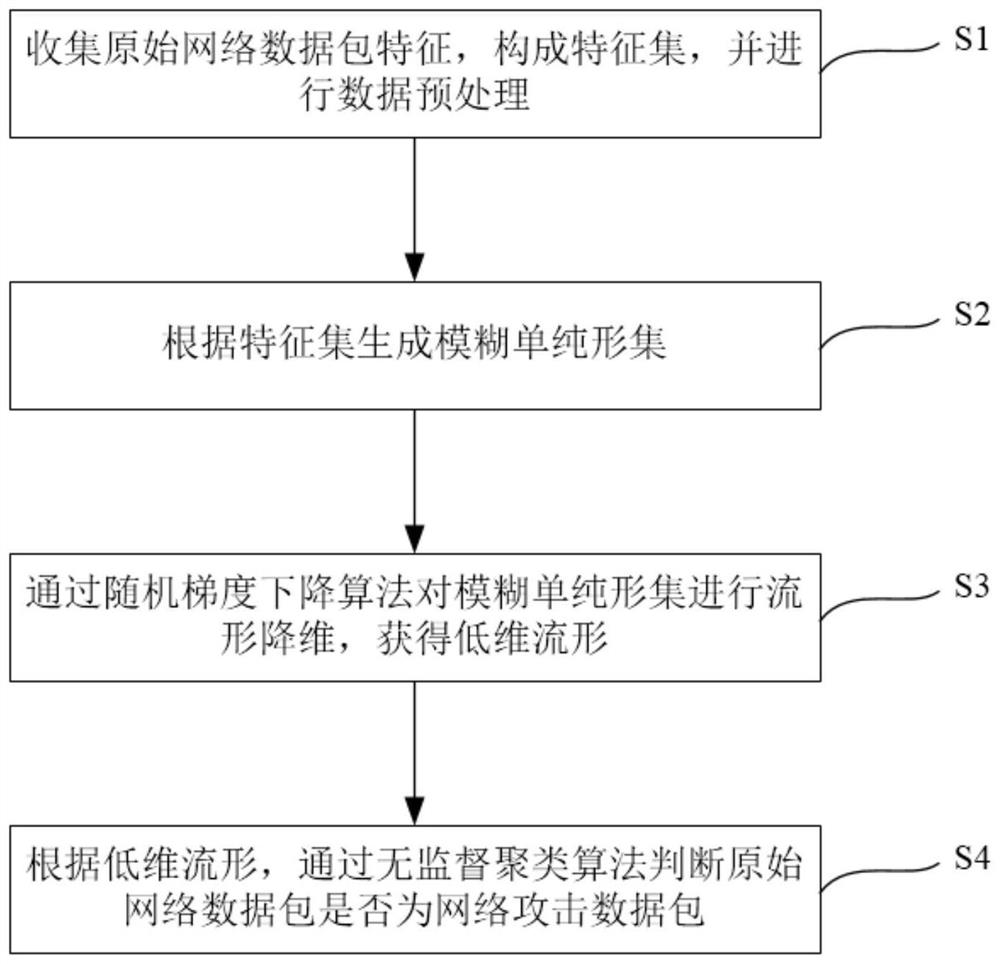
[0046] A manifold-based network packet feature dimensionality reduction and clustering attack identification method, such as figure 1 ,include:
[0047] S1. Collect original network data packet features, form a feature set, and perform data preprocessing;
[0048] S2. Generate a fuzzy simplex set according to the feature set;
[0049] S3. The stochastic gradient descent algorithm is used to reduce the manifold dimension of the fuzzy simplex set to obtain a low-dimensional manifold;
[0050] S4. According to the low-dimensional manifold, determine whether the original network data packet is a network attack data packet through an unsupervised clustering algorithm.
[0051] In step S1, separate continuous features and discrete features in the original data set, among which protocol_type, service, flag, land, logged_in, is_host_login, is_guest_login, a total of 7 features are discrete features, and the remaining 34 are continuous features.
[0052] Use the upper and lower quar...
Embodiment 2
[0079] In this embodiment, the same data points in the fuzzy simplicity of continuous features and discrete features are operated to take intersection or union, integrate different distance metrics, and regenerate low-dimensional manifolds. The formula for taking the union is as follows: The intersection goes on like this:
[0080] W(x,y)=∪(W a (x,y),W b (x,y))
[0081] where W is the connection probability between two points in the fuzzy simplex, and the subscript indicates that it originates from different fuzzy simplex.
[0082] Others are the same as in Example 1.
Embodiment 3
[0084] An electronic device includes a memory and a processor, the memory stores a computer program, and the processor invokes the program instructions to execute the attack identification method described in Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com