Data processing system and method for network flow monitoring
A data processing system and network traffic technology, which is applied in the field of data processing systems for network traffic monitoring, can solve a large number of data processing and analysis problems, achieve efficient data organization forms and systems, avoid leakage risks, and enhance security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The technical solutions of the present invention will be further described below with reference to the accompanying drawings.
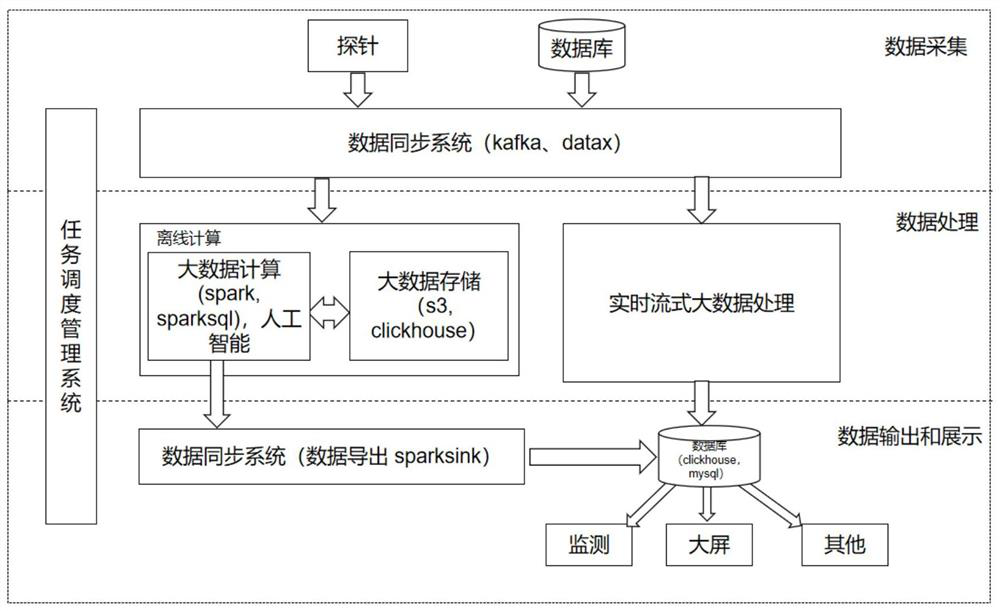
[0028] A data processing system for network traffic monitoring, comprising a data acquisition layer, a data processing layer and a data output and display layer, specifically:
[0029] Data collection layer: collect network traffic monitoring data. There are two sources of network traffic monitoring data. One is the interaction information between the user's intranet client and the server collected by the Kelai probe. The data is passed in through kafka and the format is json. The information mainly includes client_ip, server_ip, client_port, Server_port, flow_end_time and other fields, through which offline statistics and real-time calculations can be performed. The data in Kafka is written to S3 and clickhouse for storage after cleaning and conversion. Clickhouse only saves data for nearly seven days for data query and For ad hoc computing, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com