Secret image sharing and recovering method based on block chain
A technology of secret image and recovery method, which is applied in the field of information security, can solve problems such as consuming large computing resources, achieve the effect of solving low efficiency, reducing computing burden, and ensuring data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The accompanying drawings constituting a part of the present invention are used to provide further understanding of the present invention, and the exemplary embodiments of the present invention and their descriptions are used to explain the present invention and do not constitute an improper limitation of the present invention.
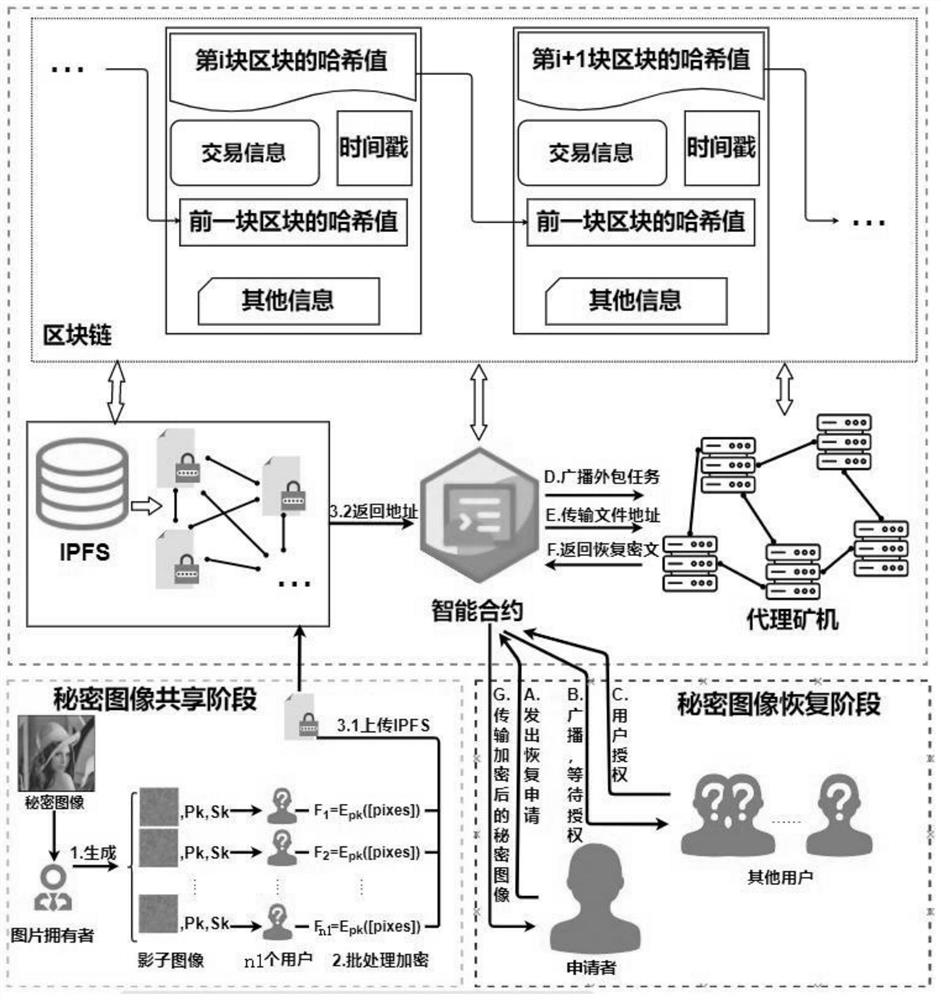
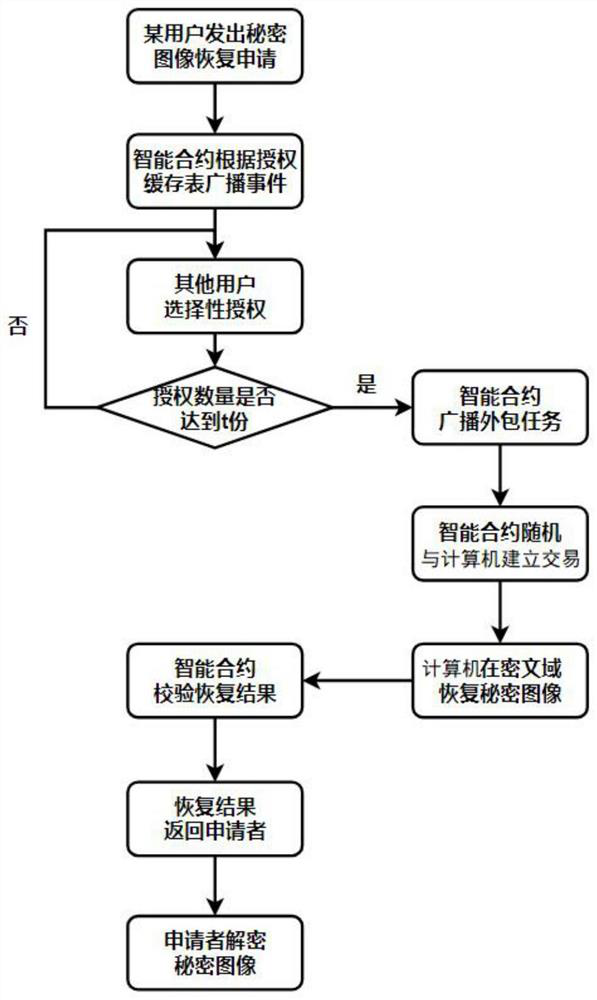
[0052] This example provides a secure and efficient method for sharing and restoring secret images based on blockchain, such as figure 1 As shown, the method mainly includes the sharing and recovery stages of the secret image.
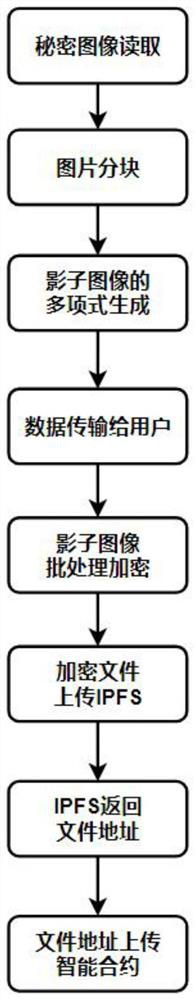
[0053] Sharing stage of secret image: This example uses the construction-generating polynomial method to generate a shadow image, and then encrypts it using the BFV scheme and uploads it to the IPFS system, such as figure 2 The specific steps are as follows:
[0054] Step 1: Generate a set of shadow images from the secret image, specifically: dividing the secret image pixels into several groups, each group containing ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com