Cloud security computing method and device based on cloud fault-tolerant technology, and storage medium
A fault-tolerant technology and computing method technology, applied in the field of cloud security computing method and device, storage medium, to achieve the effect of rapid restart, easy migration and deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
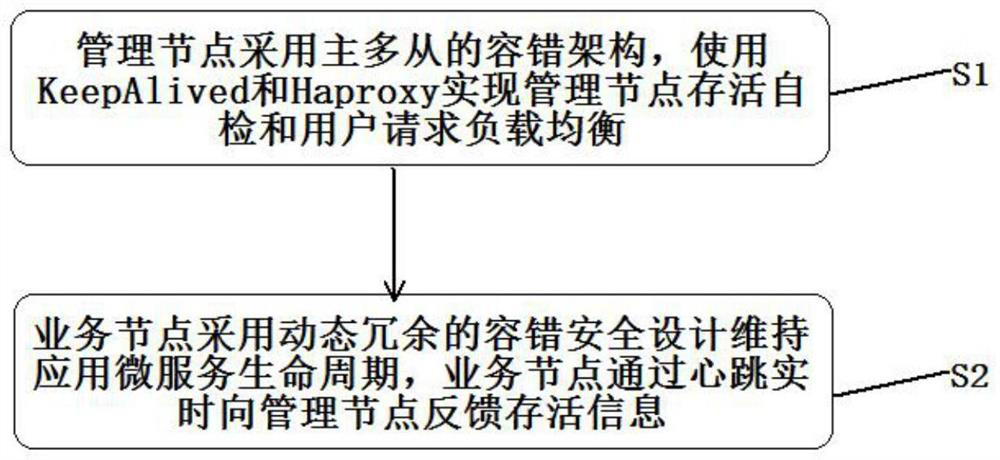
[0043] like figure 1 As shown, the implementation of the present invention provides a cloud security computing method based on cloud fault tolerance, comprising the following steps:
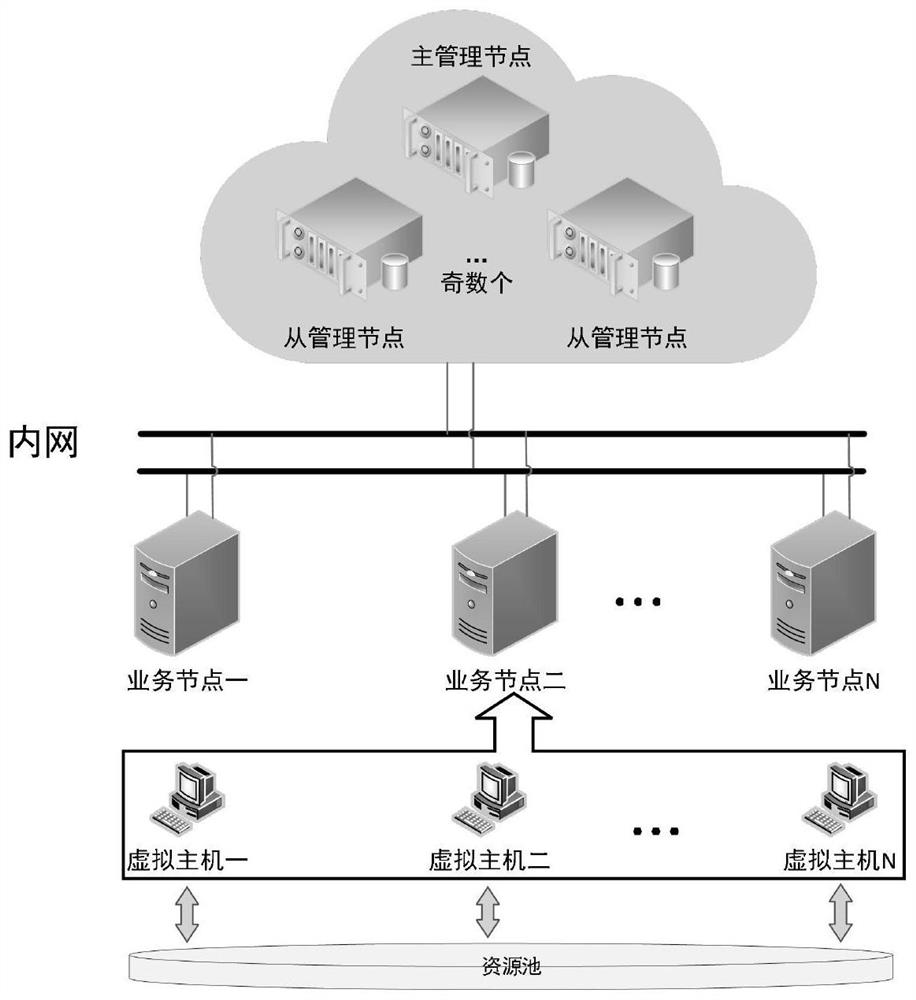
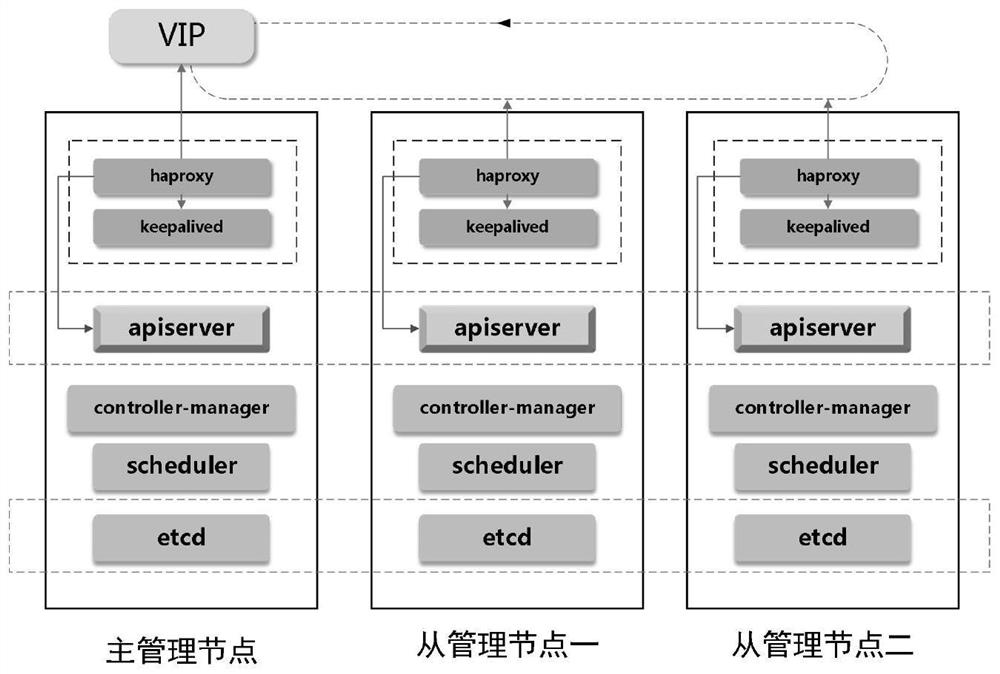
[0044] Step S1, the management node adopts a master-multi-slave fault-tolerant architecture, and uses KeepAlived and Haproxy to implement self-checking of management node survival and load balancing of user requests;
[0045] In step S2, the business node adopts a dynamic redundant fault-tolerant security design to maintain the life cycle of the application microservice, and the business node feeds back survival information to the management node in real time through the heartbeat;
[0046] Among them, the application microservices report the life cycle to the management node based on the probe mechanism, and the application microservices exchange input and output information through redundant voting.
[0047] The computing method of this embodiment can optimize the traditional cloud computing m...
Embodiment 2
[0078] The present invention also provides a cloud security computing device based on cloud fault-tolerant technology, including:
[0079] Management fault-tolerant module, which is used for management nodes to adopt a master-multi-slave fault-tolerant architecture, and uses KeepAlived and Haproxy to achieve self-check of management node survival and load balancing of user requests;
[0080] The application fault-tolerant module is used for business nodes to adopt dynamic redundant fault-tolerant security design to maintain the life cycle of application microservices, and business nodes feed back survival information to management nodes in real time through heartbeat;
[0081] Among them, the application microservice reports the life cycle to the management node based on the probe mechanism, and the application microservice exchanges input and output information through redundant voting.
Embodiment 3
[0083] The present invention also provides a storage medium, where the storage medium stores machine-executable instructions, and when the machine-executable instructions are invoked and executed by a processor, the machine-executable instructions cause the processor to implement cloud-based fault tolerance Technology's cloud security meter approach.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com