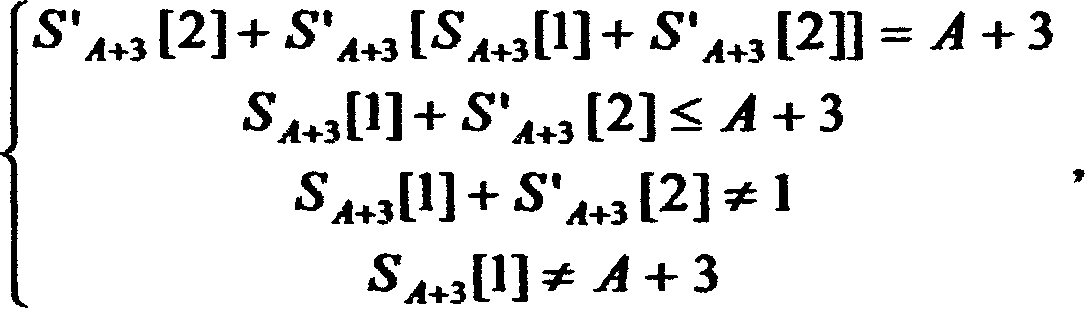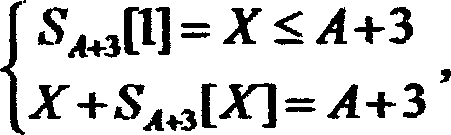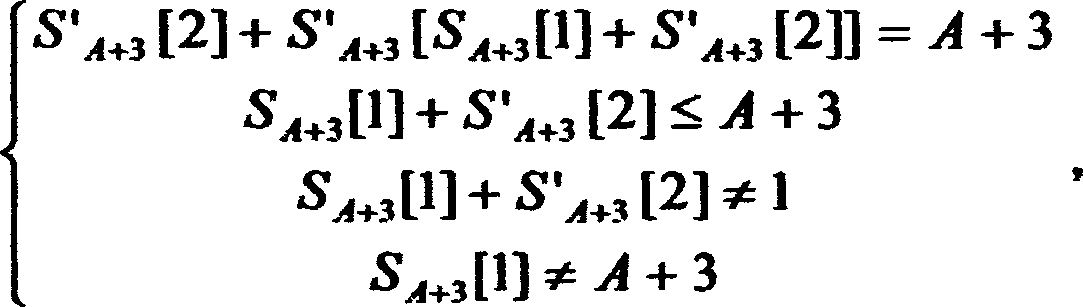Method of deciphering wired cipher in the same privacy
A password and privacy technology, applied in the field of cryptanalysis, can solve the problems of long cracking time, insufficient cracking accuracy, and low practicability of the original method, so as to shorten the cracking time and improve the accuracy.
Inactive Publication Date: 2005-05-18
SOUTHEAST UNIV
View PDF0 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
After research, when enough IVs that meet the cracking conditions are captured, although the above-mentioned IV Weakness method has a high correct rate of recovering the secret key SK, the cracking time spent at this time is very long
If fewer IVs are captured, the correct rate of cracking is not high enough
Moreover, the IV Weakness method has a higher success rate only when the traversed IV space is large. In practice, the attacker sometimes has no chance to traverse a large IV space, so the original method is not very practical.
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
The method of cracking the Wired Equivalent Privacy Class Cipher involves cracking a cryptographic protocol such as WEP based on the RC4 algorithm. This method uses the second output byte of PRGA to crack, that is, in the running process of RC4, the arrangement generated when KSA step A+3 is set as S A+3 , and let S A+3 The arrangement obtained directly after the first cycle of PRGA is S′ A+3 , at this time the second output byte of PRGA is S′ A+3 [S' A+3 [2]+S' A+3 [S A+3 [1]+S' A+3 [2]]]; in S' A+3 [2]+S' A+3 [S A+3 [1]+S' A+3 [2]]=A+3 is established, and considering the influence of all Swaps on S after the step A+3 of KSA, the second output byte will be S' with a certain probability A+3 [A+3], when S again A+3 [A+3] did not participate in the exchange in the first cycle of the above PRGA with S' A+3 [A+3]=S A+3 [A+3], so at this time S' A+3 [A+3]=S A+3 [A+3]=S A+2 [j A+3 ], search S A+2 The median is S' A+3 The unit of [A+3] can get j A+3 , and get an estimate of the key K[A+3]=j A+3 -j A+2 -S A+2 [i A+3 ].
Description
technical field The invention relates to the technical field of cryptanalysis, and in particular to cracking cryptographic protocols such as WEP based on the RC4 algorithm. Background technique RC4 (Rivest Cipher4, Rivest Cipher 4) is a sequence encryption algorithm invented by RSA Company, and it is one of the most widely used sequence encryption algorithms at present. The RC4 algorithm consists of two parts: 1. key scheduling algorithm (KSA, key timing algorithm): an initial arrangement S composed of elements 0, 1, ..., N-1 is generated by inputting a random key K of L bytes, N is generally 256; 2. Pseudo Random Generation Algorithm (PRGA, pseudo-random generation algorithm): PRGA generates a pseudo-random key sequence by means of S generated by KSA. When encrypting, the pseudo-random key sequence is different or different from the plaintext sequence to obtain the ciphertext sequence. When decrypting, only the same pseudo-random key sequence is d...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L9/00H04L9/14H04L9/32
Inventor 曹秀英耿嘉
Owner SOUTHEAST UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com