Multi surce audit data business uniformity judging method based on state conversion table
A state transition and data business technology, applied in the field of network security, can solve problems such as low audit supervision intensity, lack of consistency judgment function, and insufficient audit data sources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
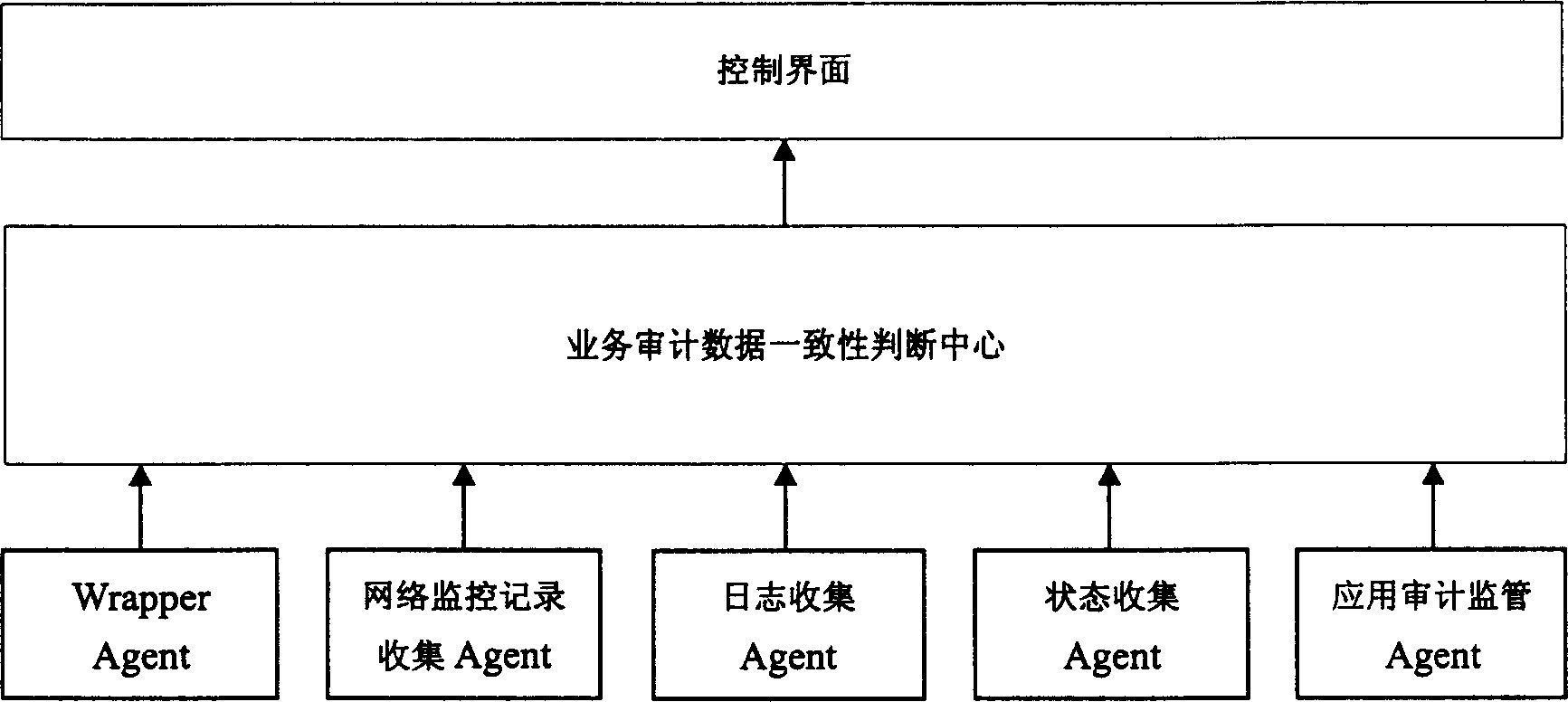
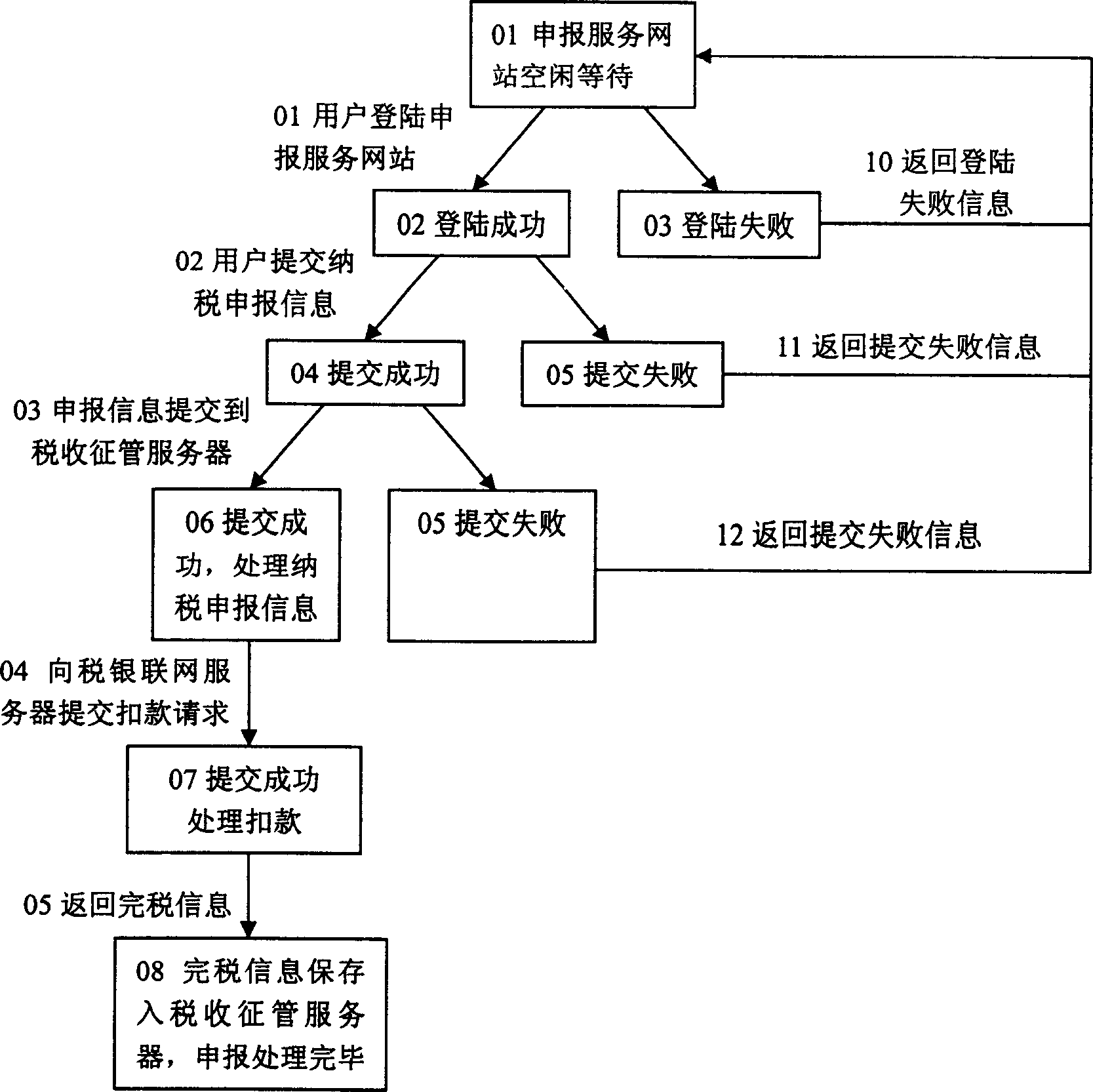
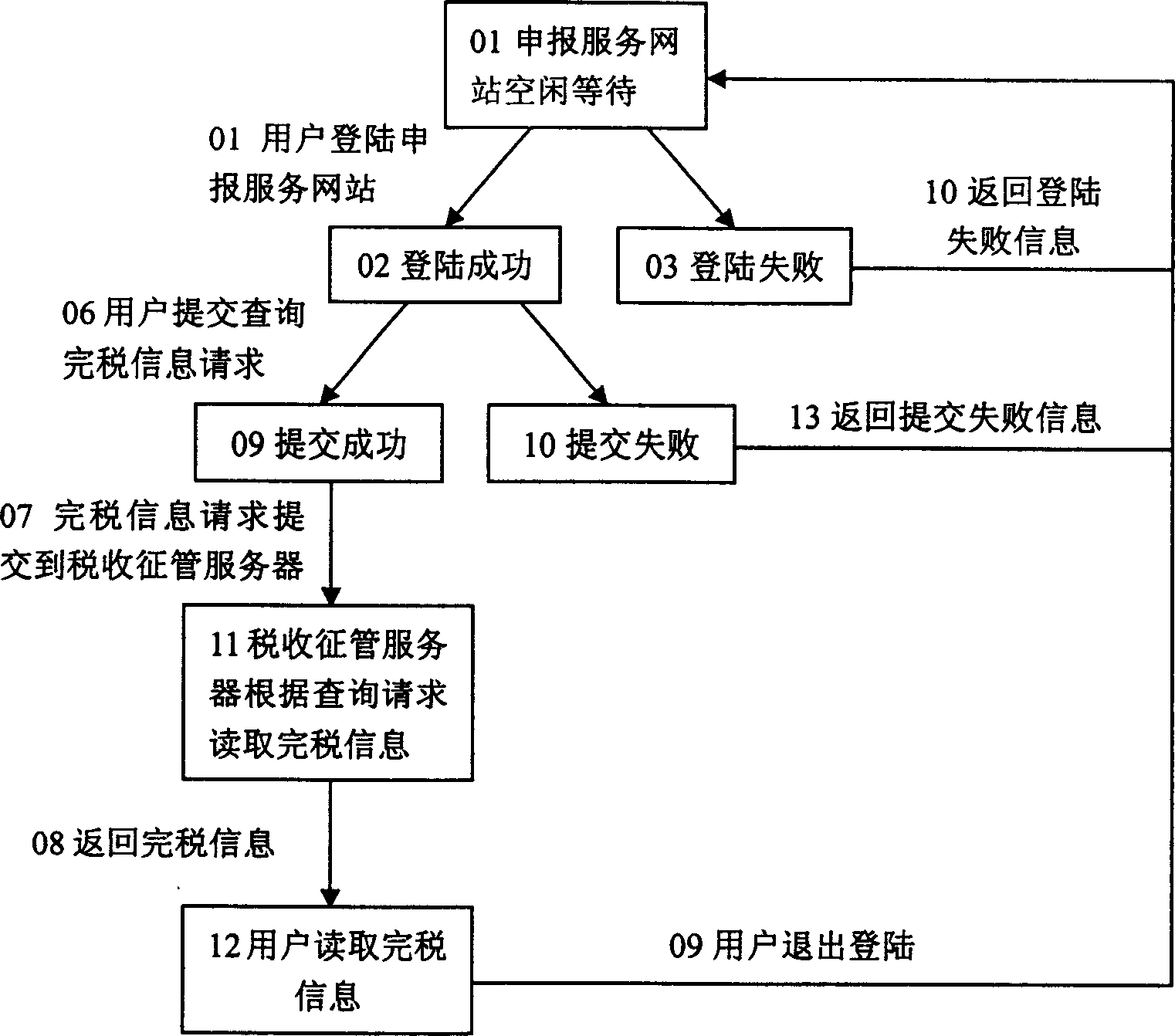
[0058] like figure 1 Shown, the inventive method is carried out by distributed data collection agent (Agent), the system that business audit data consistency judgment center and control interface form carry out, and the main effect of all kinds of data collection agents (Agent) is to realize original data collection, according to Certain templates and security policies are used to extract and identify information, transform the original information into standardized business audit information representation, and report to the business audit data consistency judgment center. The present invention includes five kinds of data acquisition agents (Agent), including:
[0059] (1) The log collection agent (Agent) is responsible for collecting system logs and internal events including mainstream operating systems (Windows series, UNIX series), logs generated by various application platforms and database platforms, and logs generated by application systems (document transfer, etc.) , ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com