Access authenitcation method of radio local neet mobile terminal
A wireless local area network and mobile terminal technology, applied in the field of access authentication mechanism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
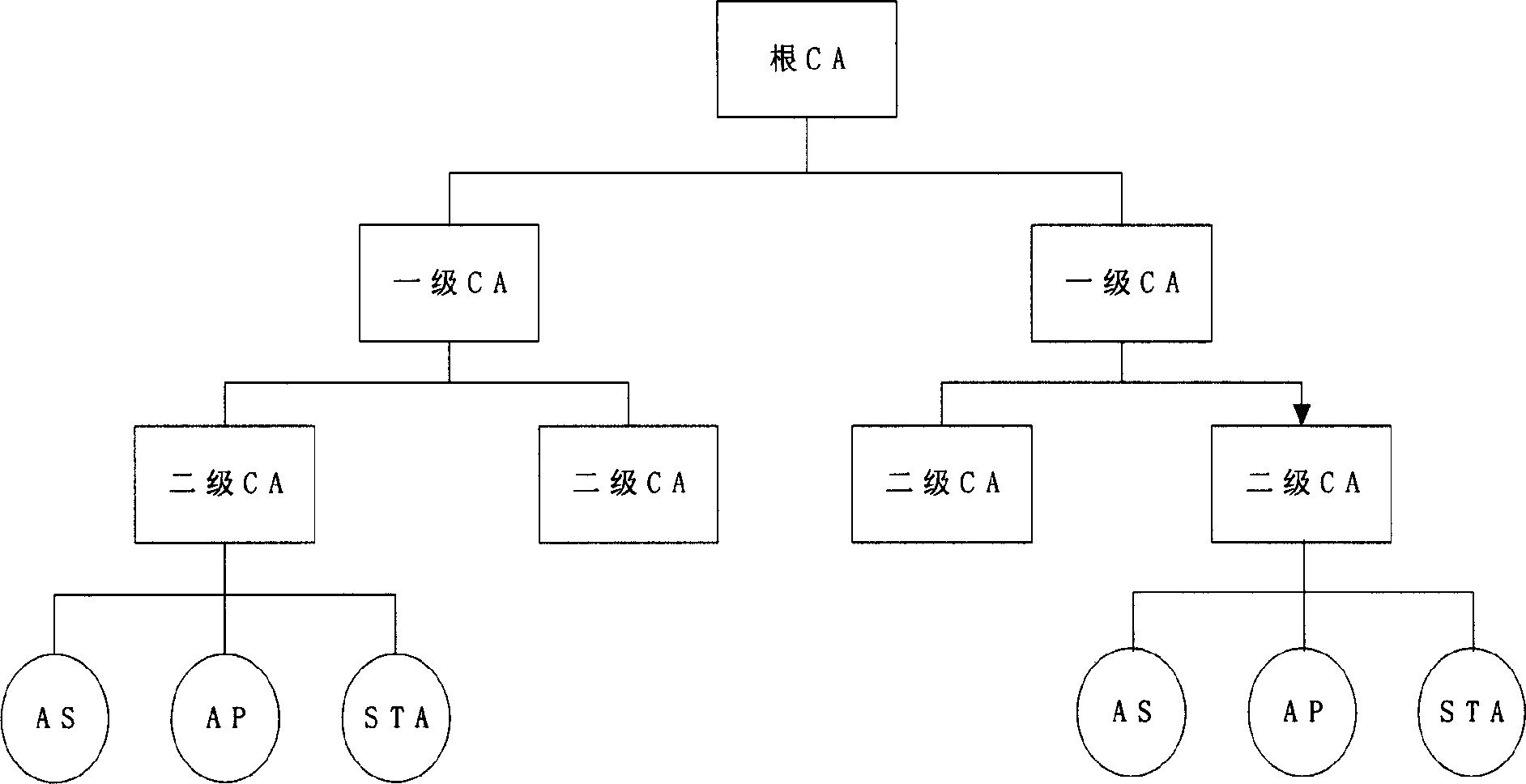
[0025] In the WAPI standard, ASU has both the functions of a certificate authentication center and a WAPI authentication server. It can be considered to divide the ASU into two different entities, CA and AS. The CA is responsible for certificate management, and the AS is responsible for authenticating the identities of STAs and APs. Such as figure 1 As shown, the certificate management in WAPI can adopt the architecture in the current PKI (Public Key Infrastructure), and the CA is divided into multi-level CAs such as root CA, first-level CA, and second-level CA, which correspond to the actual application environment. Each level of management organization, each level of CA is responsible for managing the lower level of CA certificates and the user (AS, AP and STA) certificates of the organization, each level of organization users in addition to holding the local CA issued to their own WAPI certificate, also holds a The certificate chain from the user certificate to the root CA...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com