VPN client end safety strategy exchange and storage method
A security policy and client technology, applied in the field of security policy storage and exchange, can solve problems such as hindering the popularization of VPN, complicated client configuration, etc., and achieve the effect of convenient use, convenient network management, and improved security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
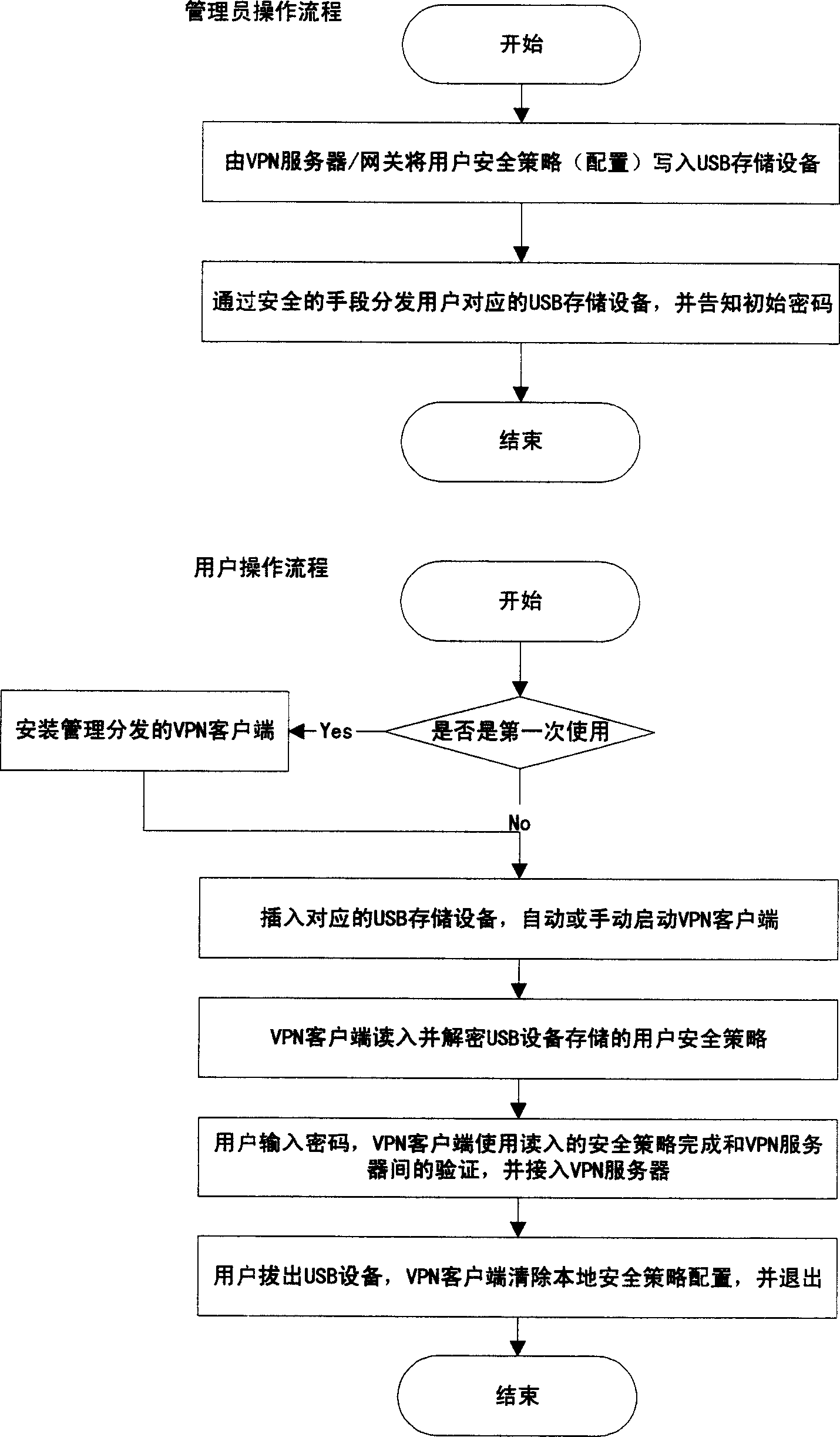
[0021] The present invention will be described in further detail below in conjunction with accompanying drawing:
[0022] see figure 1 As shown, before distributing the USB storage device of the VPN client, the administrator inserts the USB storage device into the VPN server (gateway) or its control device, and writes the security policy and configuration of the corresponding user in the USB storage device. The writing process Needs to be automated. The user's security configuration policy includes but is not limited to: user name, user private certificate, gateway public key (certificate), gateway IP, VPN system shared key and other configurations of the VPN client. The written security configuration policy is encrypted using the built-in shared key of the gateway and the client program. The encryption algorithm is a symmetric encryption algorithm, which can be but not limited to 3DES, AES and other algorithms.
[0023] In order to ensure the security of storage, an encrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com