Method and equipment for finishing entrance guard authentication using wireless communication device
A wireless communication device, access control technology, applied in the direction of wireless communication, security communication device, security device, etc., can solve the problems of abnormal control, inability to read data, and difficulty, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
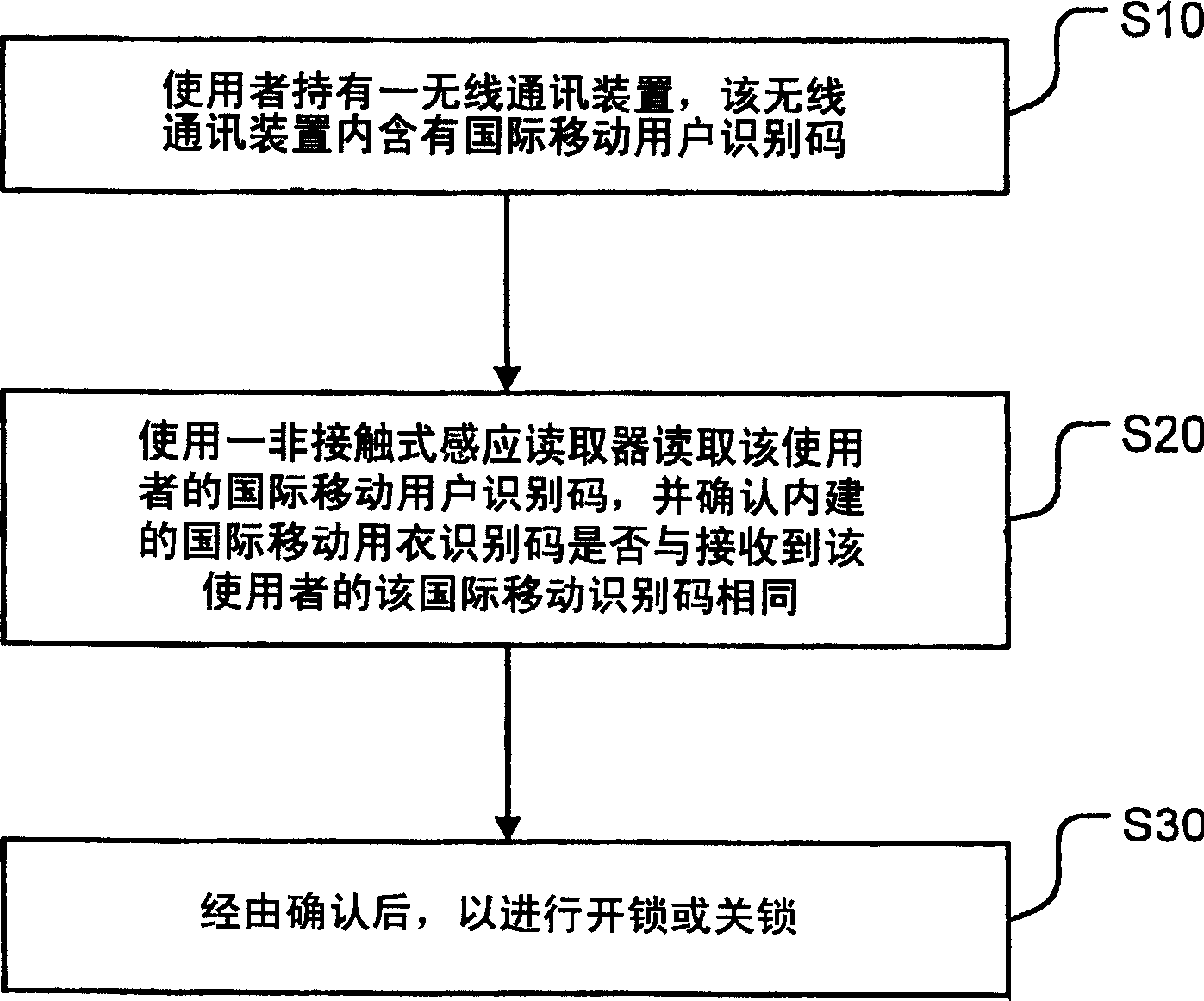
[0017] In order to have a further understanding and understanding of the features and achieved effects of the present invention, preferred embodiments and coordination are described in detail as follows.
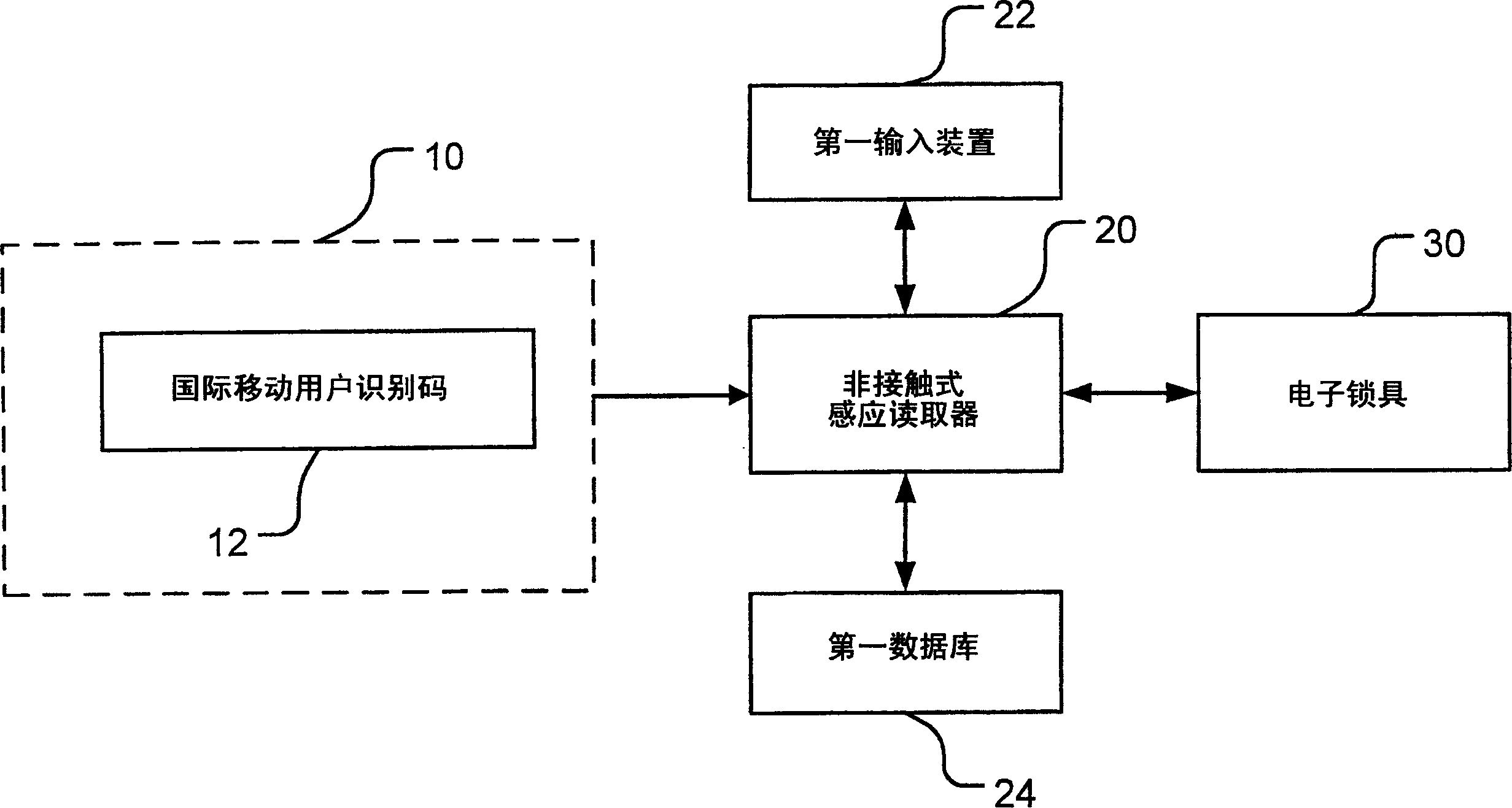
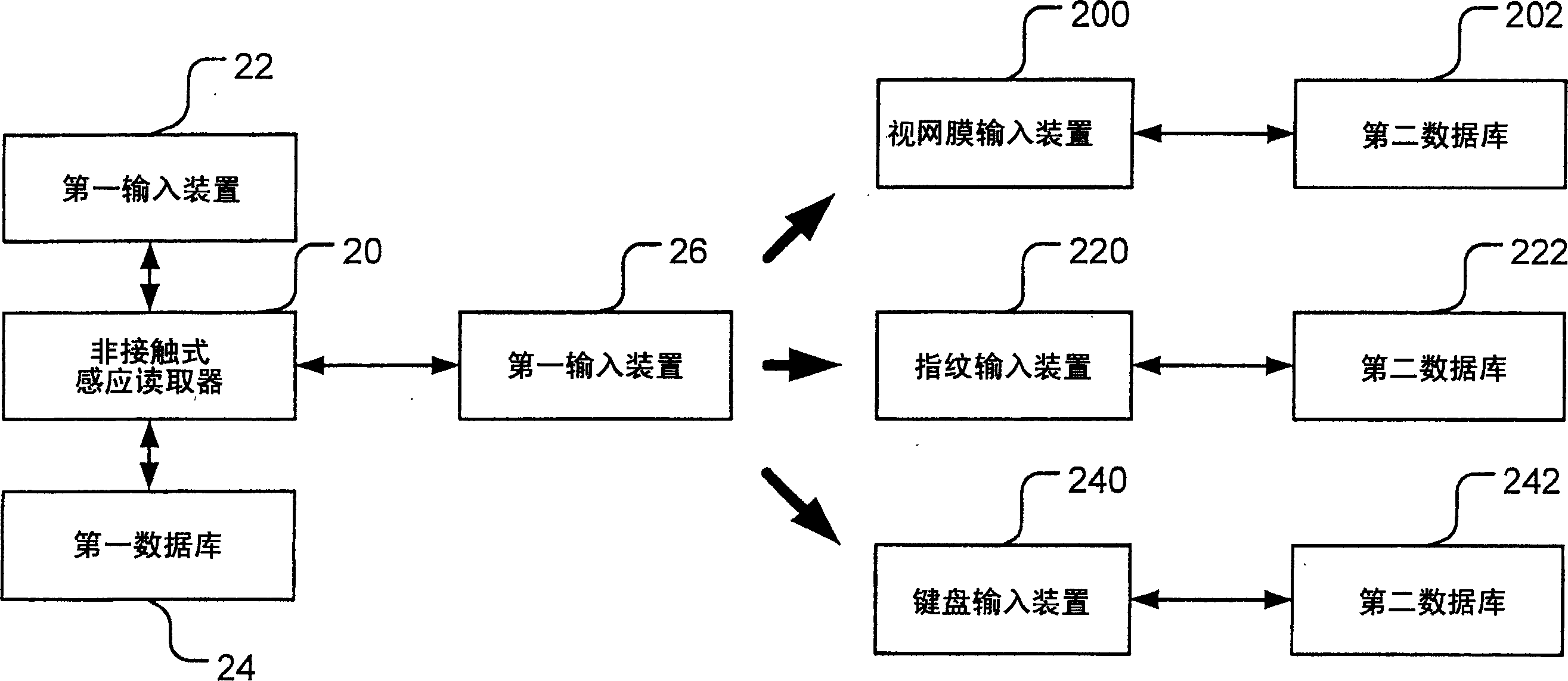
[0018] The present invention mainly discloses the uniqueness of an International Mobile Subscriber Identity (IMSI) using a wireless communication device, and uses it in access control to improve its security mechanism, and even add a password mechanism-retina or fingerprint identification A method and a device for making it have another layer of safety protection function. The wireless communication device of the present invention is described by taking a mobile phone as an example.
[0019] Such as figure 1 As shown, it is a schematic block diagram of a preferred embodiment of the present invention. Generally, a unique International Mobile Subscriber Identity (IMSI) 12 is included in the mobile phone 10, and the International Mobile Subscriber Identity (IMSI) 12 can be pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com