Verifying method for network file system service
A network file system and authentication method technology, applied in the field of server authentication, can solve problems such as low efficiency and inaccessible servers, and achieve the effects of improving efficiency, reducing the number of DNS queries, and increasing the response speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
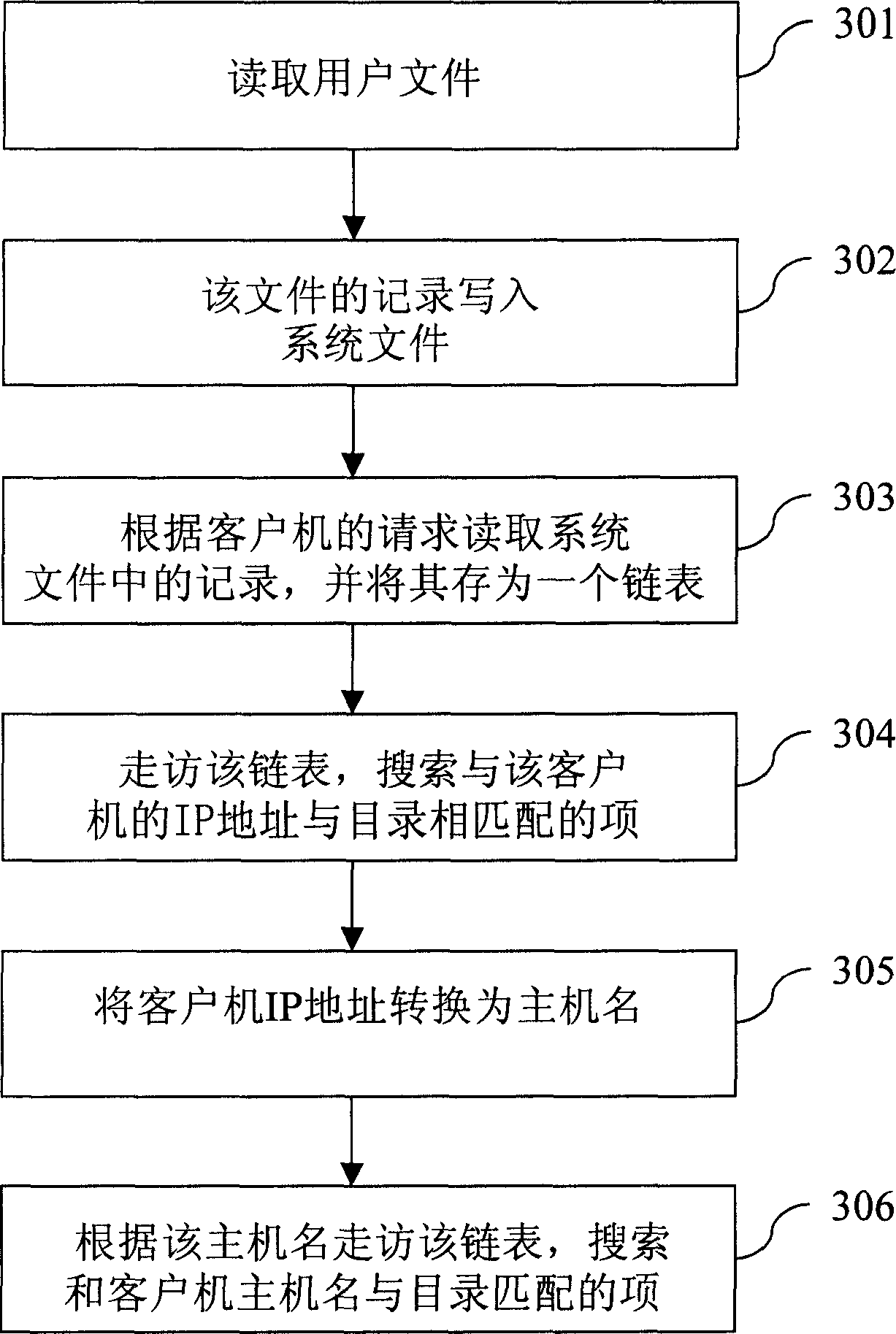
[0083] see image 3 , is the flow chart of the network file system service authentication method of the present invention, first step 301 reads the user file; step 302 writes the record of the file into the system file; then step 303 reads the system file according to the access request of the client Record, and it is stored as a linked list; Then step 304 visits this linked list, searches for the item that matches with the IP address of the client computer that sends the request and directory; Step 305 converts the IP address of the client computer that sends the request into the host name; Finally, step 306 visits the linked list according to the host name, and searches for an item matching the client host name and directory.
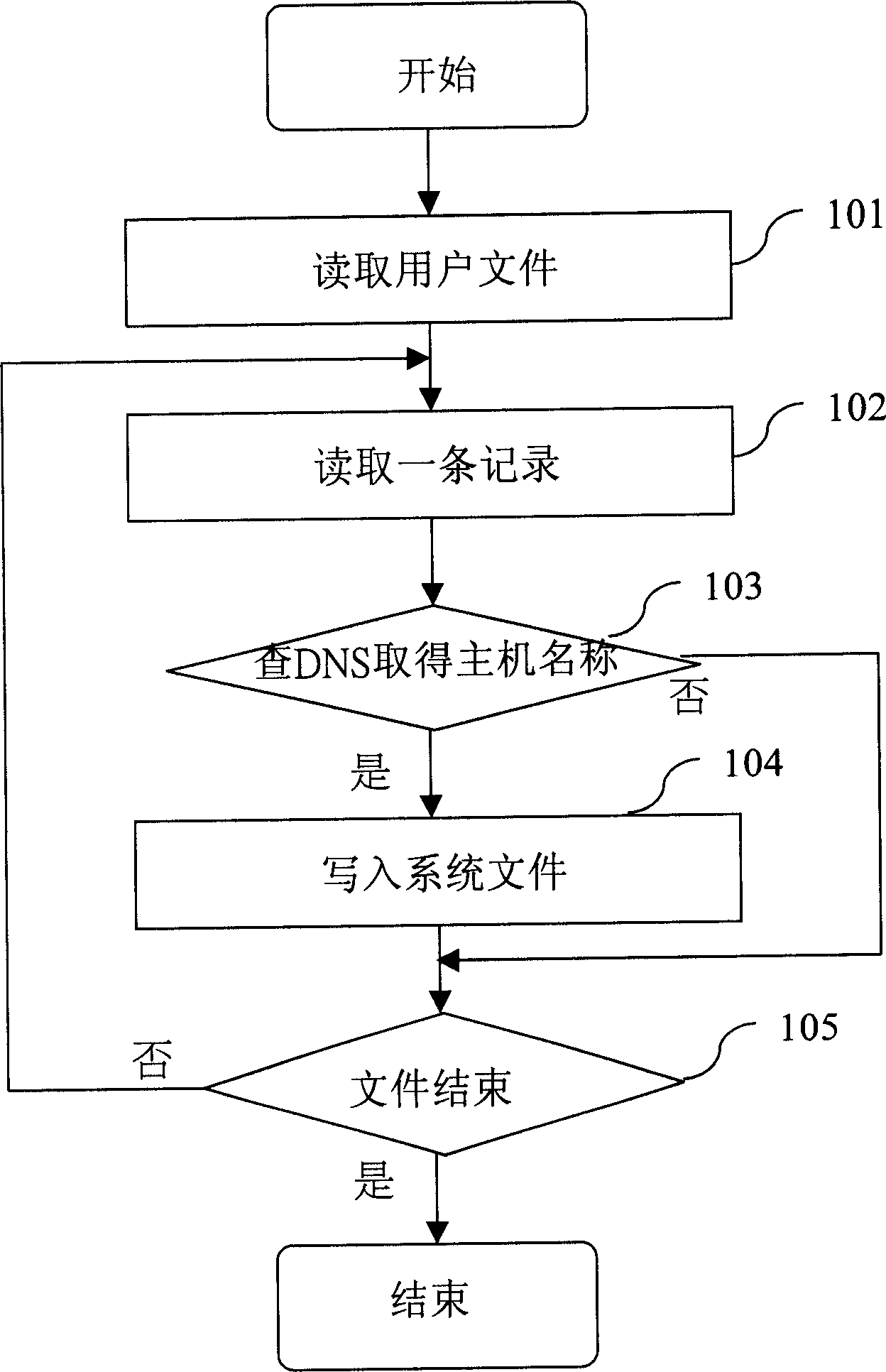
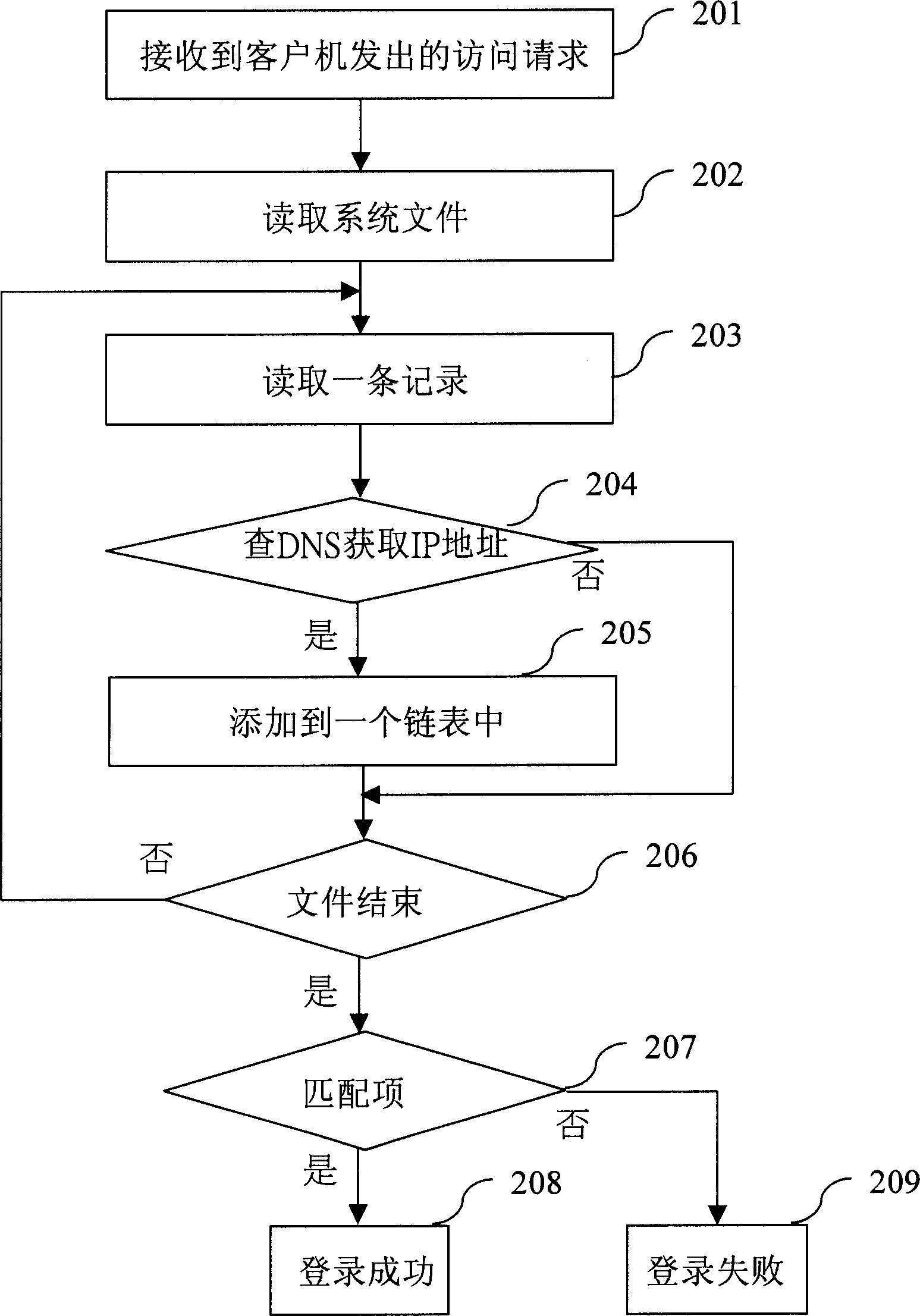
[0084] In the above process, compared with the prior art, the present invention aims at the traditional figure 1 and figure 2 The two flows shown are modified separately.
[0085] See first Figure 4 , for the present invention parses user file a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com