Categorization of host security levels based on functionality implemented inside secure hardware
A security level and security technology, applied in the level field, can solve the problem of not being able to provide enough information for security level judgment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
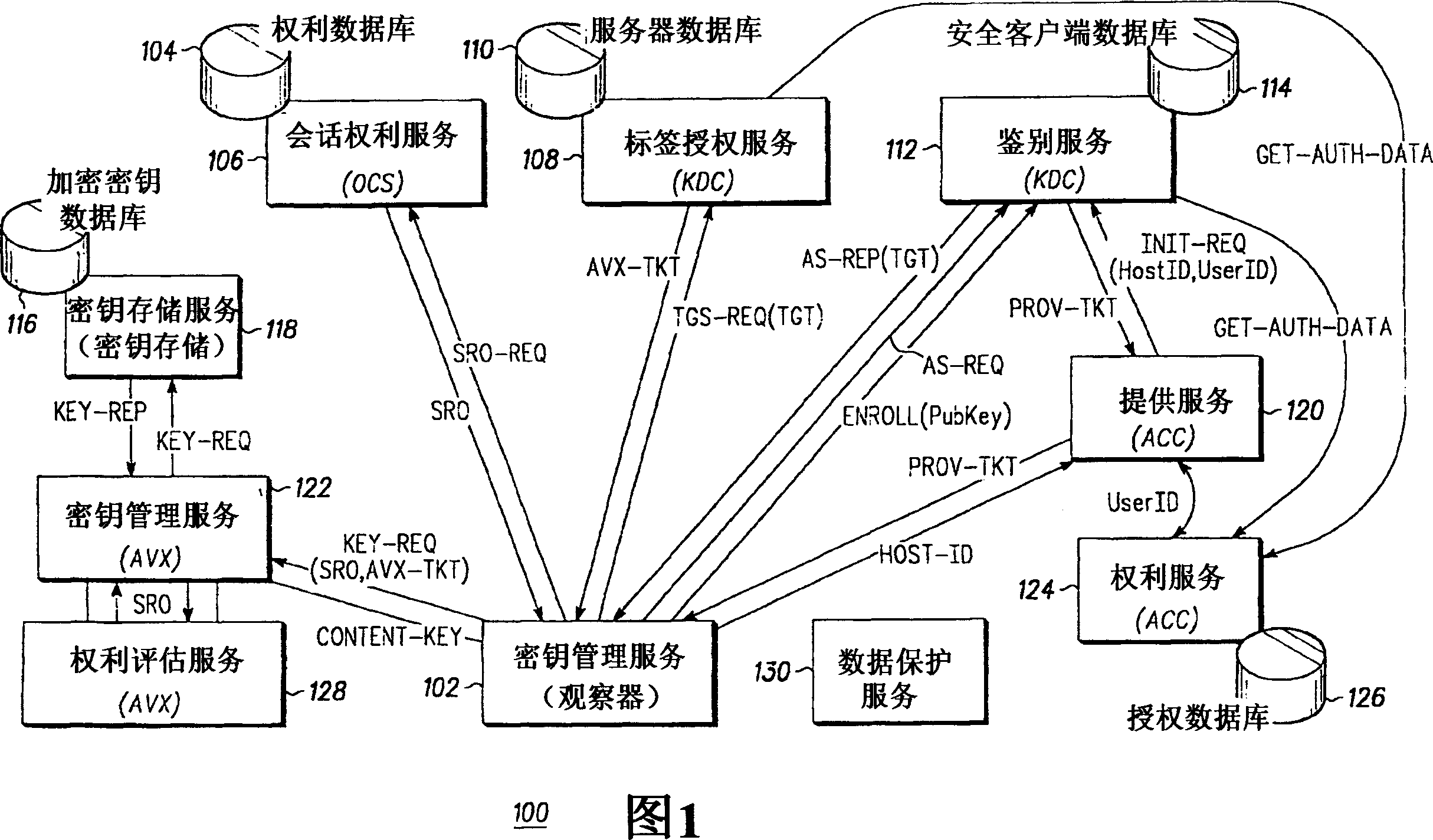
[0021] Figure 1 illustrates the components of an Internet Protocol Rights Management (IPRM) system suitable for use with the present invention.
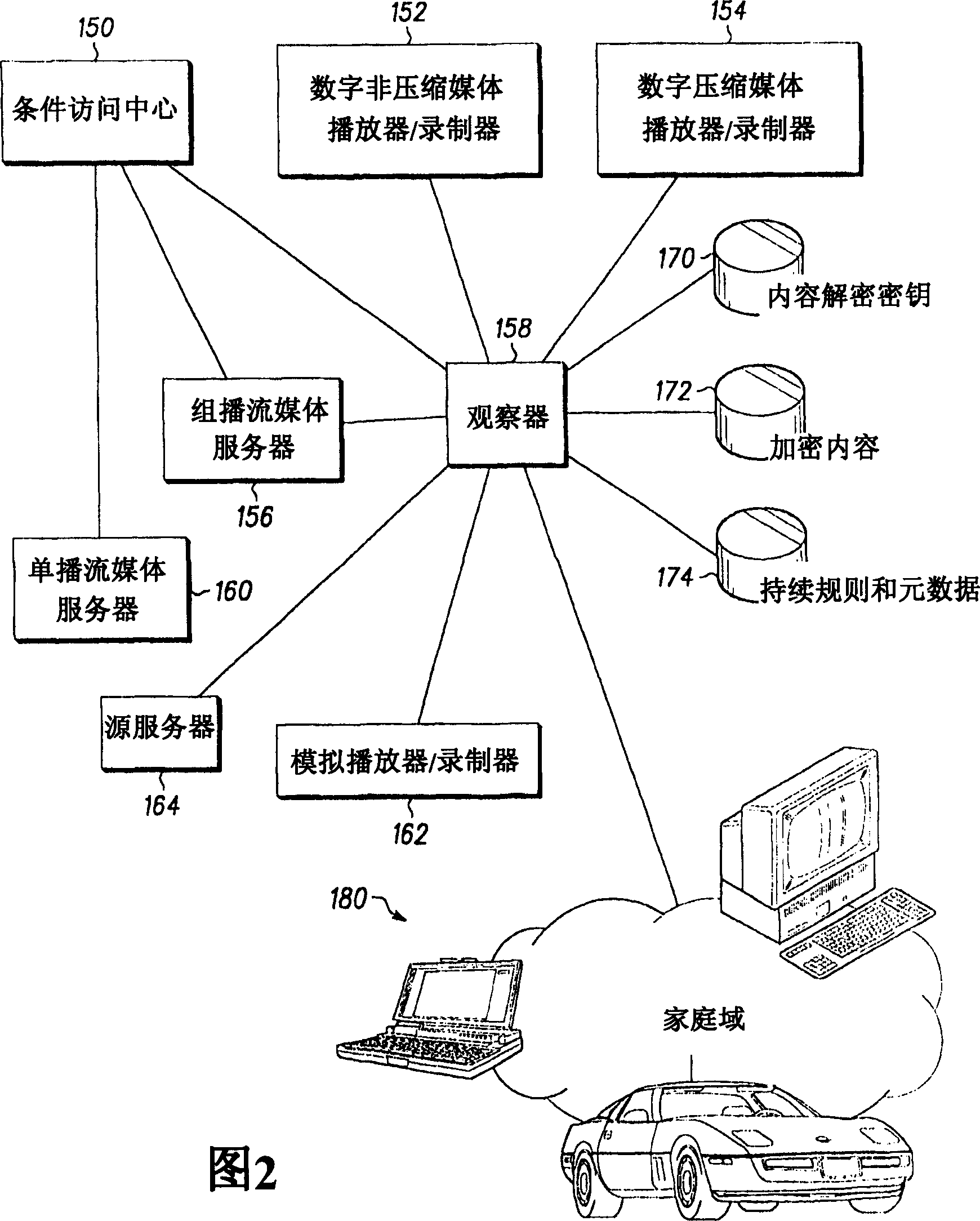
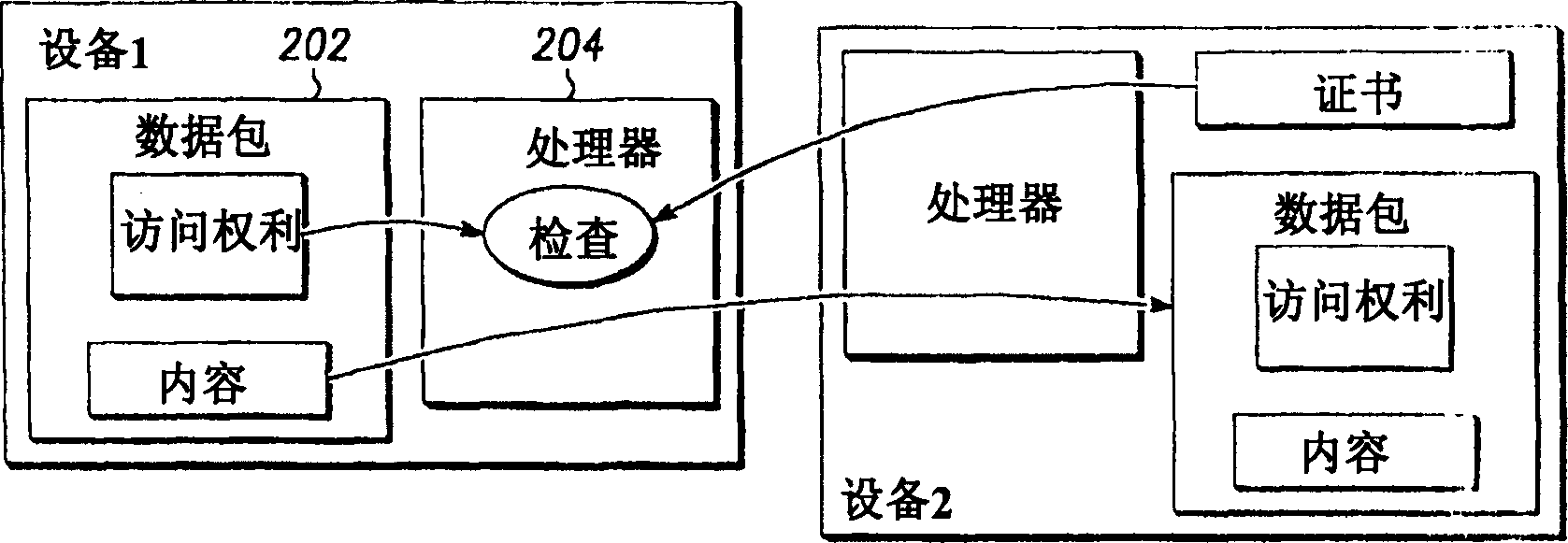
[0022] In FIG. 1, logical components represented by blocks illustrate functions that are preferably used to perform the functions of the physical components enclosed in parentheses. Note that Figure 1 is only a broad and general schematic of a content delivery network. The functions represented by the logic components may differ from those shown in Figure 1 and remain within the scope of the invention. Logical components may be added, modified, or removed in FIG. 1 . Physical components are examples taken of logical components described in datagrams. In general, the invention can be used with any number and type of devices connected by a digital network.
[0023] Figure 1 illustrates the interfaces in IPRM designed for secure content distribution and rights enforcement by content and service providers. For example, such systems a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com