System and method for distributed authorization for access to communications device
A technology of communication equipment and equipment, applied in the field of communication, capable of solving security threats, exposure, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
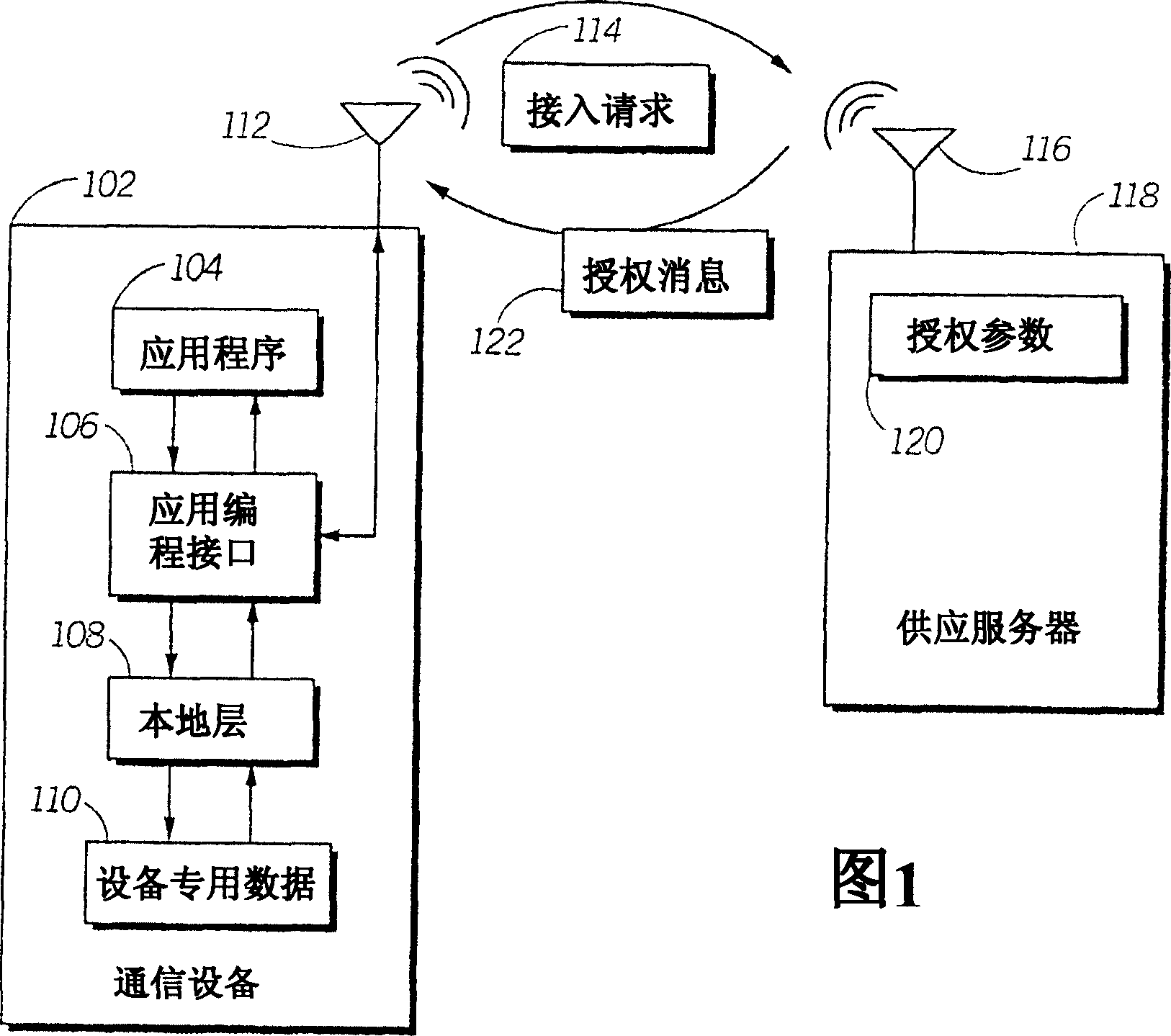
[0013] Figure 1 illustrates a distributed authorization architecture with which an embodiment of the present invention may operate. As shown in the figure, the communication device 102 can communicate wirelessly with the authorization server 118 to initiate and confirm requests made by applications running on the communication device 102 to access the device specific data 110 . For example, communication device 102 may be or include a cellular telephone, a network wireless device such as a personal digital assistant (PDA) or personal information manager (PIM) equipped with an IEEE 802.11b or other wireless interface, a laptop computer or a wireless device equipped with an 802.11b or Other laptops with other wireless interfaces, or other communication or user equipment. The communication device 102 may communicate with the authorization server 118 via the antenna 112, eg, in the 800 / 900 MHz, 1.9 GHz, 2.4 GHz or other frequency bands, or through an optical or other link.
[001...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com