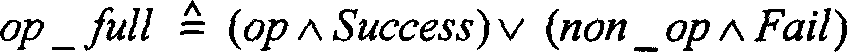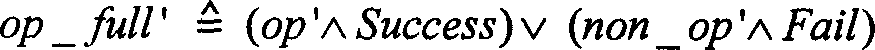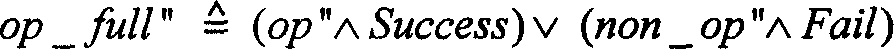Test example generation method of safety data base management system
A test case generation and management system technology, applied in the direction of software testing/debugging, program control devices, etc., can solve problems such as difficult to find problems, lack of pertinence and dependence of test cases
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0098] Taking the LOIS security database management system developed by the State Key Laboratory of Information Security, Institute of Software, Chinese Academy of Sciences as an example, the test case generation method for the security database management system provided by the present invention will be described in detail below.
[0099] There are two modes of autonomous authorization related operations in the SDBMS model of the system: one is to authorize users directly, and the other is to authorize roles first, and then activate roles by users. The direct authorization operation GrantPermToUser is an administrative operation that requires the existence of an authorized user who has not been granted this permission. It depends on multiple operations, such as creating a user, creating a security label, creating a data object, connecting, etc. Before performing a test for this operation, you should ensure that you have performed a test for the above operation. And any type ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com