Method of updating revocation list
A technology of revocation list and identifier, applied in the direction of digital data authentication, computer security device, transmission system, etc., can solve problems such as difficulty in determining
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
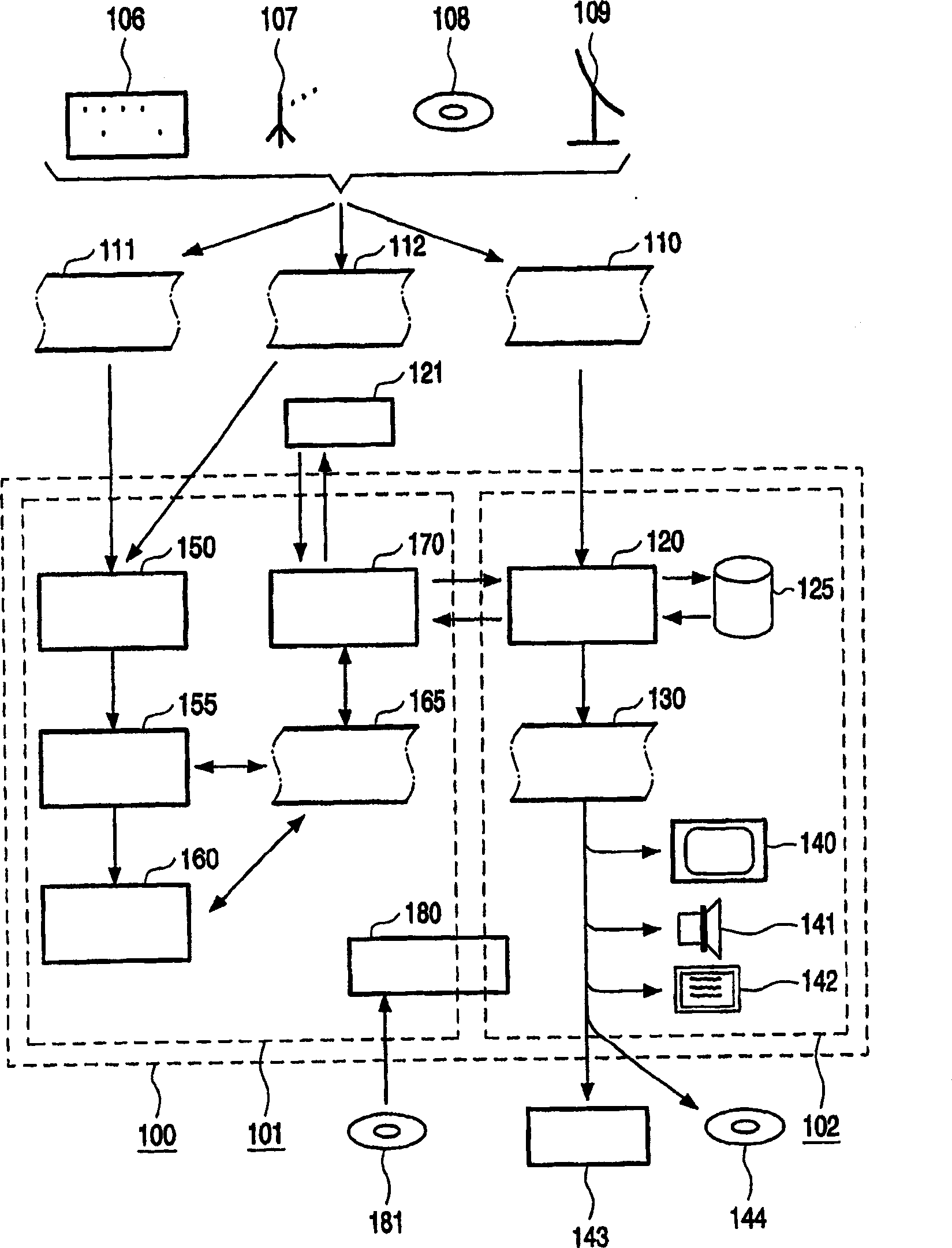
[0038] figure 1 A system 100 is schematically represented. System 100 may be implemented as a dedicated device or as a group of devices. It may contain one or more processing units to implement the required functions.
[0039] The data structures and program instructions for these processing units may be incorporated with the device or stored and / or distributed in a medium 181 such as a CD-ROM. A general-purpose device such as a personal computer or a PDA can also be used to implement the present invention by using a computer program product to distribute the program incorporating the present invention.
[0040] The system 100 comprises different subsystems 101 and 102 .
[0041] Subsystem 101 is concerned with the handling of local revocation lists; subsystem 102 is capable of controlling access to content material 110 . This access control system 102 typically has an access device 120 that processes content material obtained from a different source, such as a different d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com