Digital signature supporting personal trusted device and its method for implementing signature
A digital signature and device technology, applied in the field of information security, can solve the problems of attacking signature software, unable to directly provide digital signature services, attacking smart card drivers, etc., to achieve the effect of convenient use and portability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
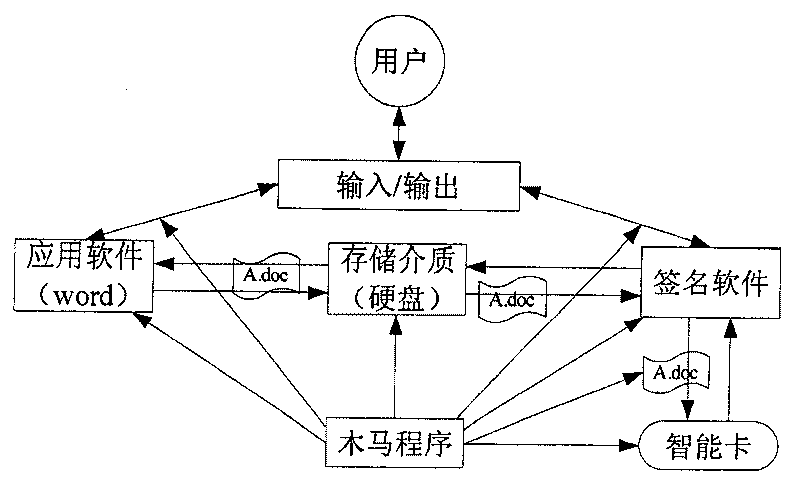
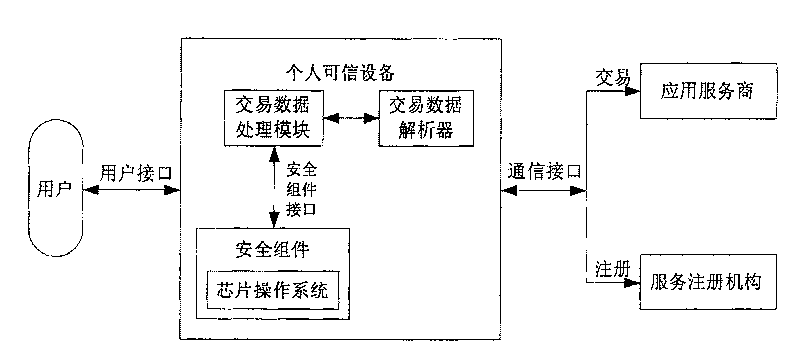
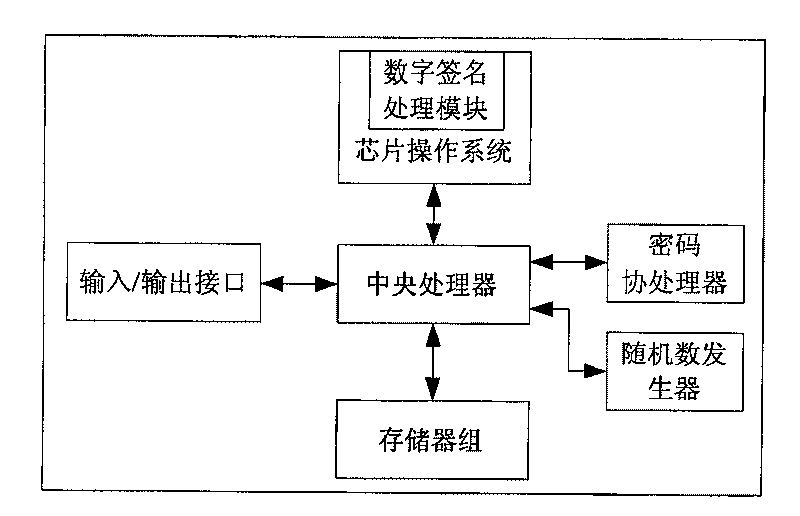
[0062] As mentioned above, information security includes the security of data storage, computing, and data transmission. These security needs to be guaranteed by the hardware and software that constitute the computing environment. Although the existing smart card or USB KEY can guarantee the security of data storage and data calculation, it can realize a personal security environment in a certain sense. However, since it does not have a keyboard and display screen, its storage and calculation functions depend on the data interaction between them and the personal computer, so it is difficult to ensure the security of data transmission. Though personal computer has keyboard and display screen, is convenient for people to carry out corresponding computing work, but the security of itself lacks guarantee.
[0063] The inventor has analyzed the deficiencies of the above-mentioned smart card and personal computer, and thinks that it is necessary to combine the safety and reliability...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com