Digital cipher lock with secure secondary authorization unlocking function
A coded lock and digital technology, applied in the field of digital coded locks, can solve problems such as inappropriateness, potential safety hazards, limited parameters, etc., and achieve the effect of improving security, high security, and eliminating super passwords
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] Now in conjunction with accompanying drawing, technical solution and embodiment are further described:
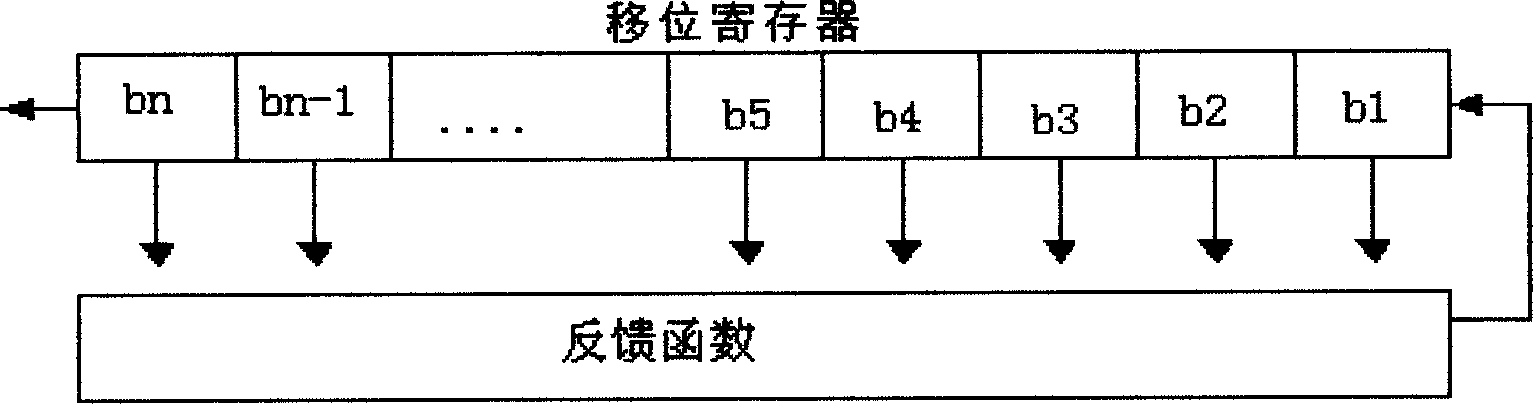
[0022] figure 1 , Schematic diagram of the feedback shift register.
[0023] Shift register sequences are used in cryptography and coding theory. Since the beginning of the electronic age, sequence ciphers based on shift registers have been widely used in encryption operations in military cryptography. A feedback shift register consists of two parts: the shift register and the feedback function. A shift register is a sequence of bits. Each time a bit is needed, all bits in the shift register are shifted to the right (left) by one bit, and the new leftmost (right) bit is calculated based on other bits in the shift register. The feedback function performs logic operations with certain bits in the shift register (these bits are called tap sequences) in a certain way to form the new leftmost (right) bit of the shift cycle.
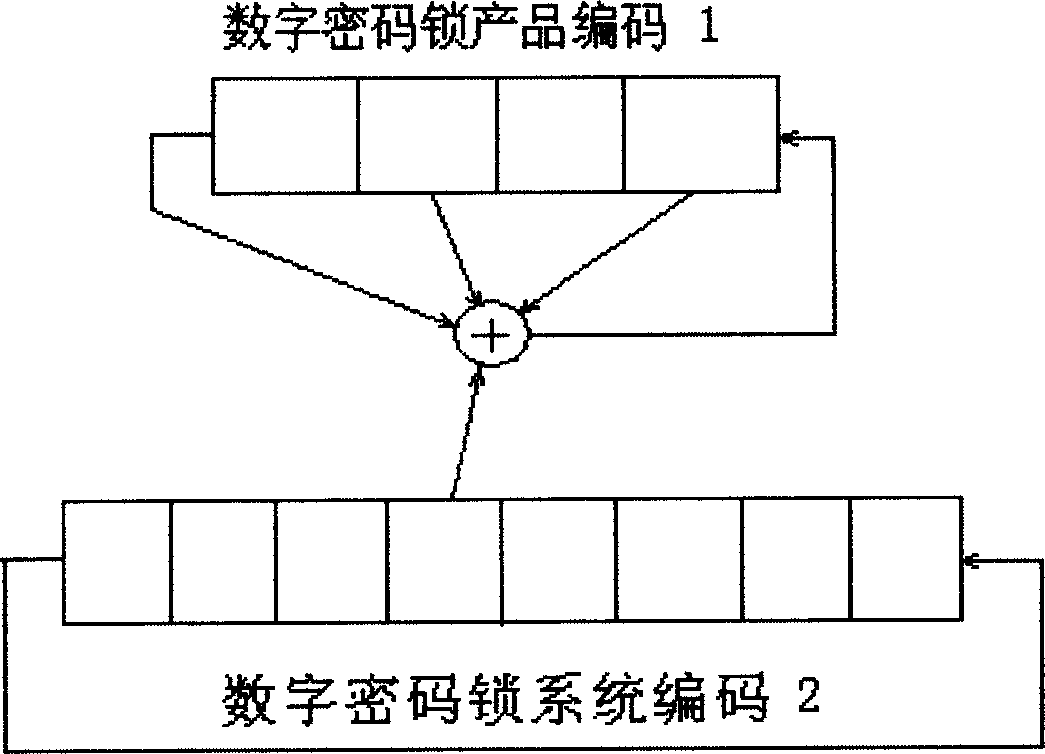
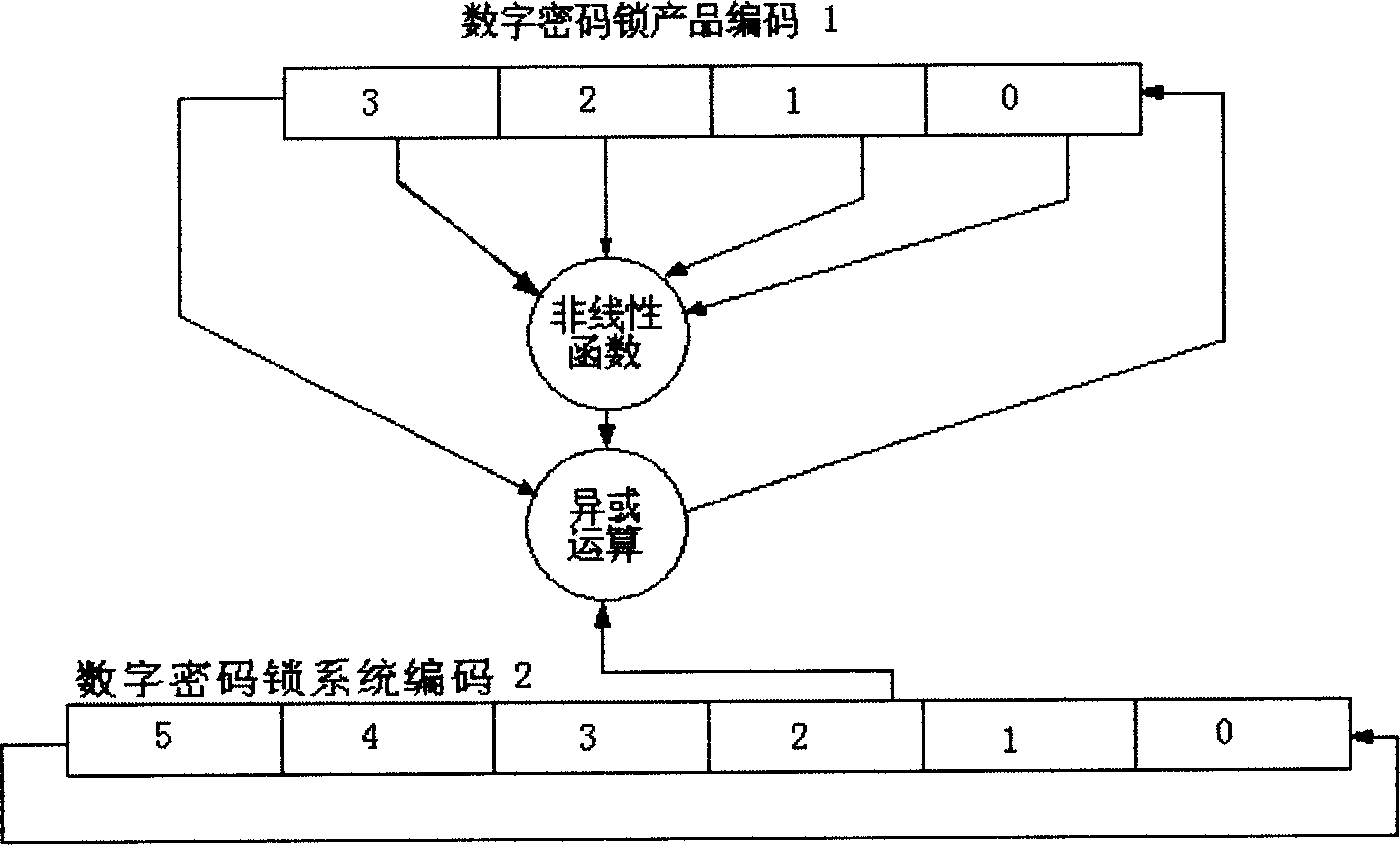
[0024] figure 2 , The schematic diagram ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com