Patents
Literature
43results about How to "Not easy to decipher" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
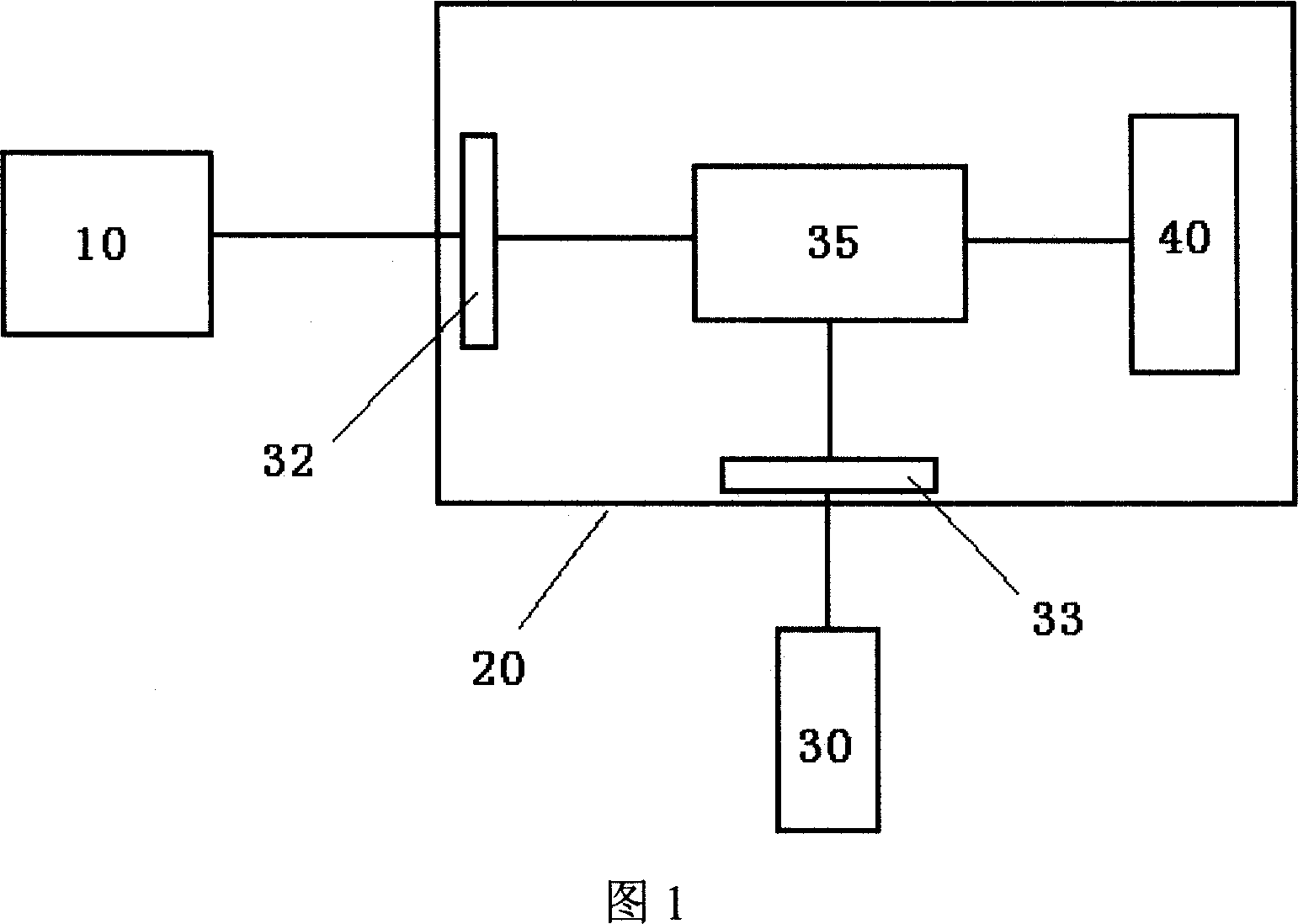
Mobile phone unlocking method based on voice recognition
InactiveCN102752453AImprove securityImprove reliabilitySubstation equipmentKey pressingStorage security
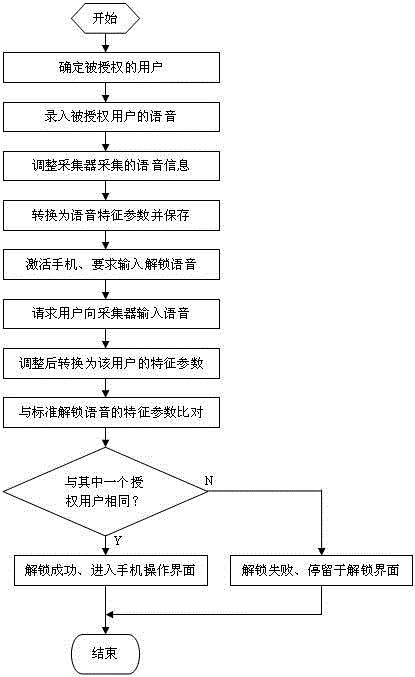
The invention discloses a mobile phone unlocking method based on voice recognition, and the method comprises following steps of recording and storing standard unlocking voice; requiring the unlocking voice when requesting the user to actuate the mobile phone; inputting the voice and converting the voice into voice characteristic parameters; and comparing the voice characteristic parameters of the request user with the standard voice characteristic parameters, and enabling successful unlocking if the voice characteristic parameters are identical to the voice characteristic parameters of one authorized user. Due to the adoption of the method, the problem that the unlocking password is easy to decipher or to peer can be overcome, the collected voice information is finally converted to the voice characteristic parameters after being corrected and adjusted, so that the accuracy of the characteristic parameter calculation result is improved, and the reliability of the voice unlocking is further improved; the information content is compared with the voice characteristic parameters, the unlocking can be completed when the inputted voice characteristic parameters completely conform to the standard unlocking voice, the unlocking voice is not easy to decode, the storage security of the private data of the mobile phone is high, and the stored private data of the mobile phone is not easy to leak; and in the unlocking process, the keystroke operation is not needed, so that convenience in use can be realized.
Owner:CHENGDU CK SCI & TECH
Text-message distribution system capable of identifying encrypted bar code and realization method thereof
InactiveCN104166923ACan't decipherImprove distribution efficiencyCo-operative working arrangementsCommerceUser privacyBarcode
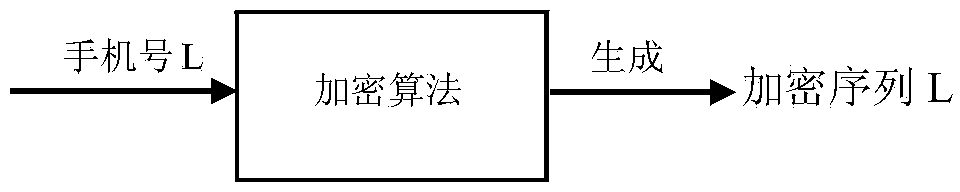
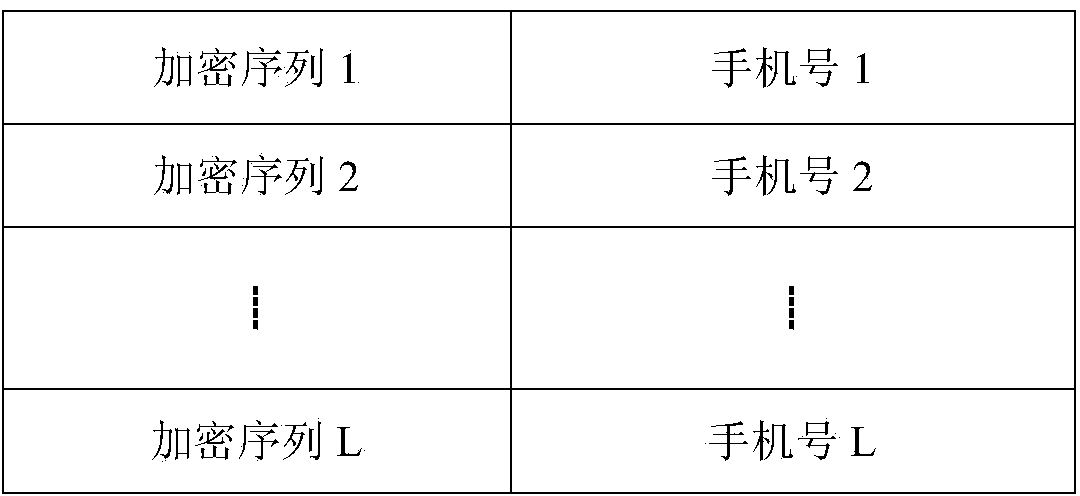
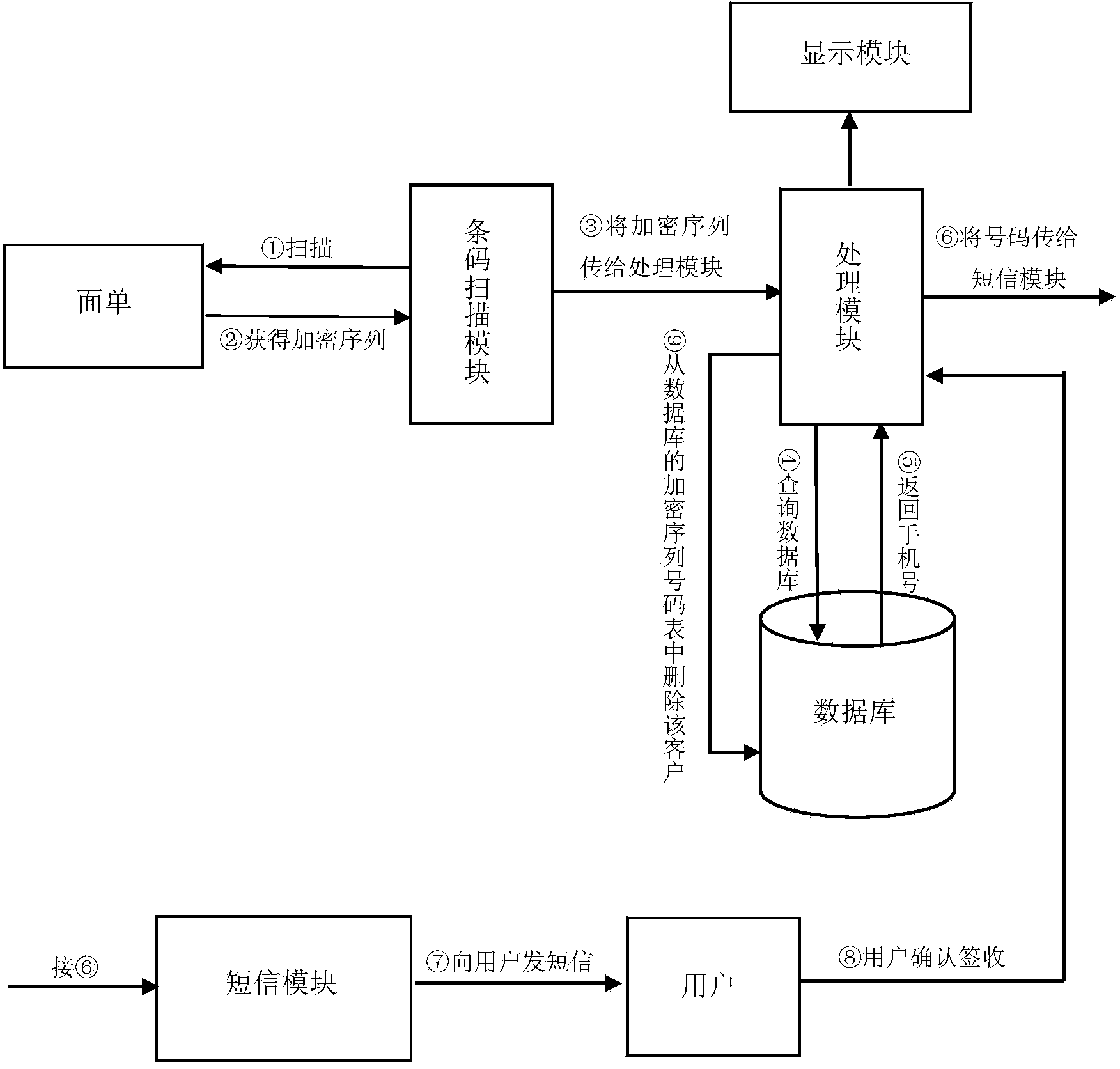
The invention discloses a text-message distribution system capable of identifying an encrypted bar code and a realization method thereof. The system includes an encrypted sequence, an encrypted algorithm database, an encrypted sequence number table, a bar-code scanning module, a processing module, a text message module, and a terminal display module. In the system and the realization method thereof, one encryption algorithm is randomly selected from the encrypted algorithm database and a number is used as input to generate a unique encryption sequence and at last, the encryption sequence and a cellphone number are used as one item of record and stored into the encrypted sequence number table and the encryption sequence is printed on an express waybill in the form of a bar code or a two-dimension code. During express distribution, the bar-code scanning module scans the bar code on the waybill so that an encryption sequence number is obtained. According to the sequence number, a bar code-number table is searched so that the cellphone number is obtained and the text message module distributes a text message which is edited in advance to a customer. The system is capable of improving express distribution efficiency, and protecting user privacy in a specific degree at the same time.
Owner:NANJING UNIV OF POSTS & TELECOMM
Safety mobile hard disc
InactiveCN101067802AImprove securityNot easy to decipherInput/output to record carriersUnauthorized memory use protectionIdentification deviceRemovable media
This invention relates to a safe moving HD including a first interface and a disk used in reading data on the disk by the first interface, a controller used in generating and backing up identification code and a second interface, in which, the generated identification code is output via a second interface and backed up at the time when it is output by the controller and when the comparison of the backed up identification code and the data input from the second interface is passed, the computer is allowed to read data on the disk, in which, only users with encrypted keys of mobile storages can use the mobile HD.
Owner:YITUO SCI & TECH CO LTD SHENZHEN
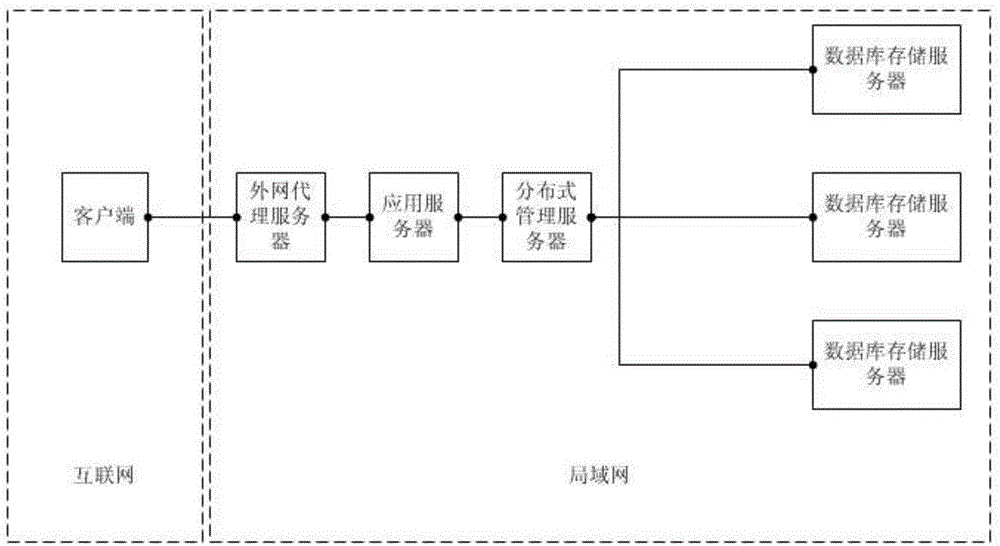
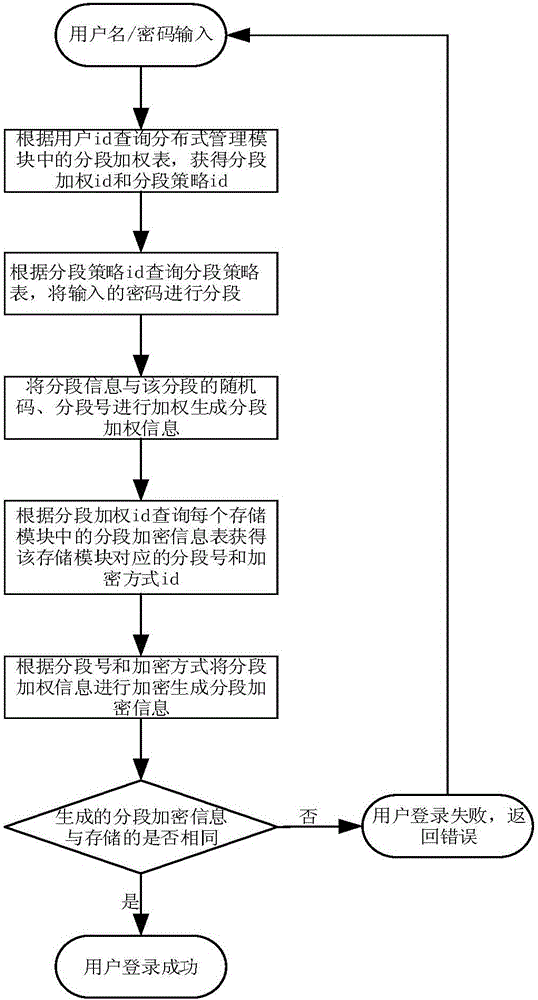
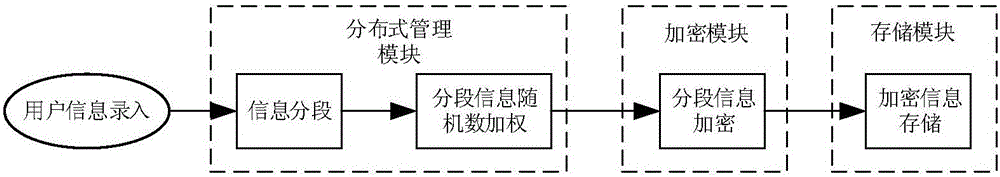
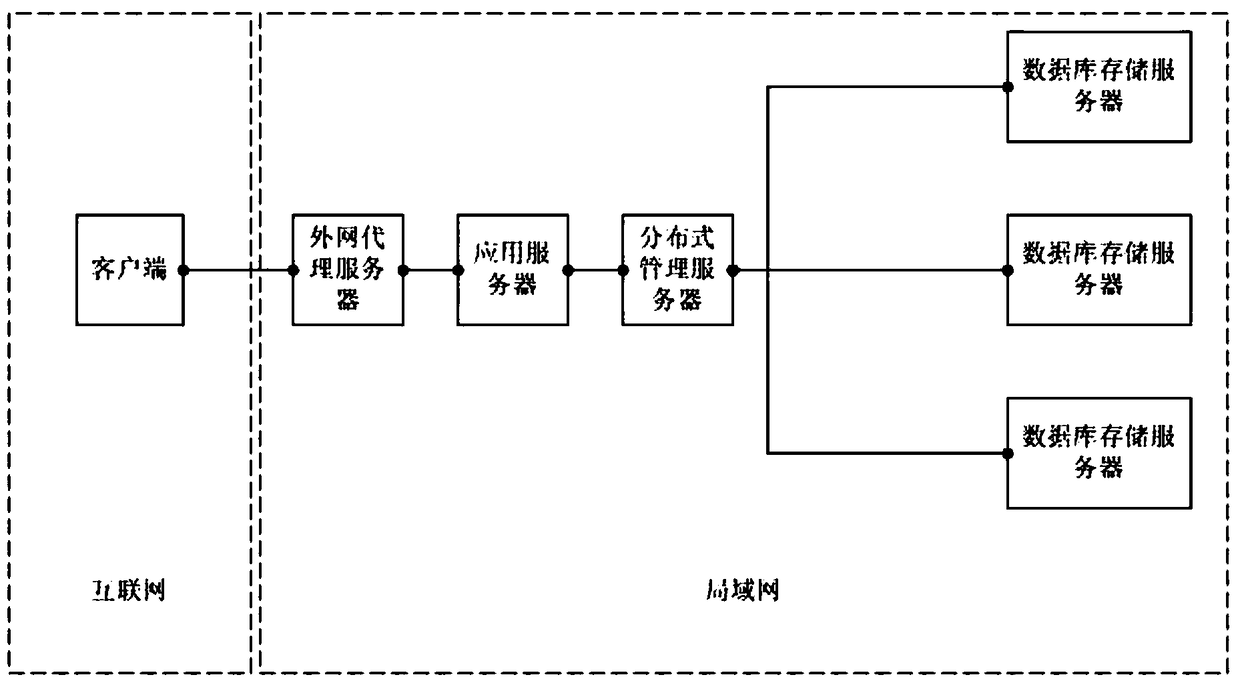
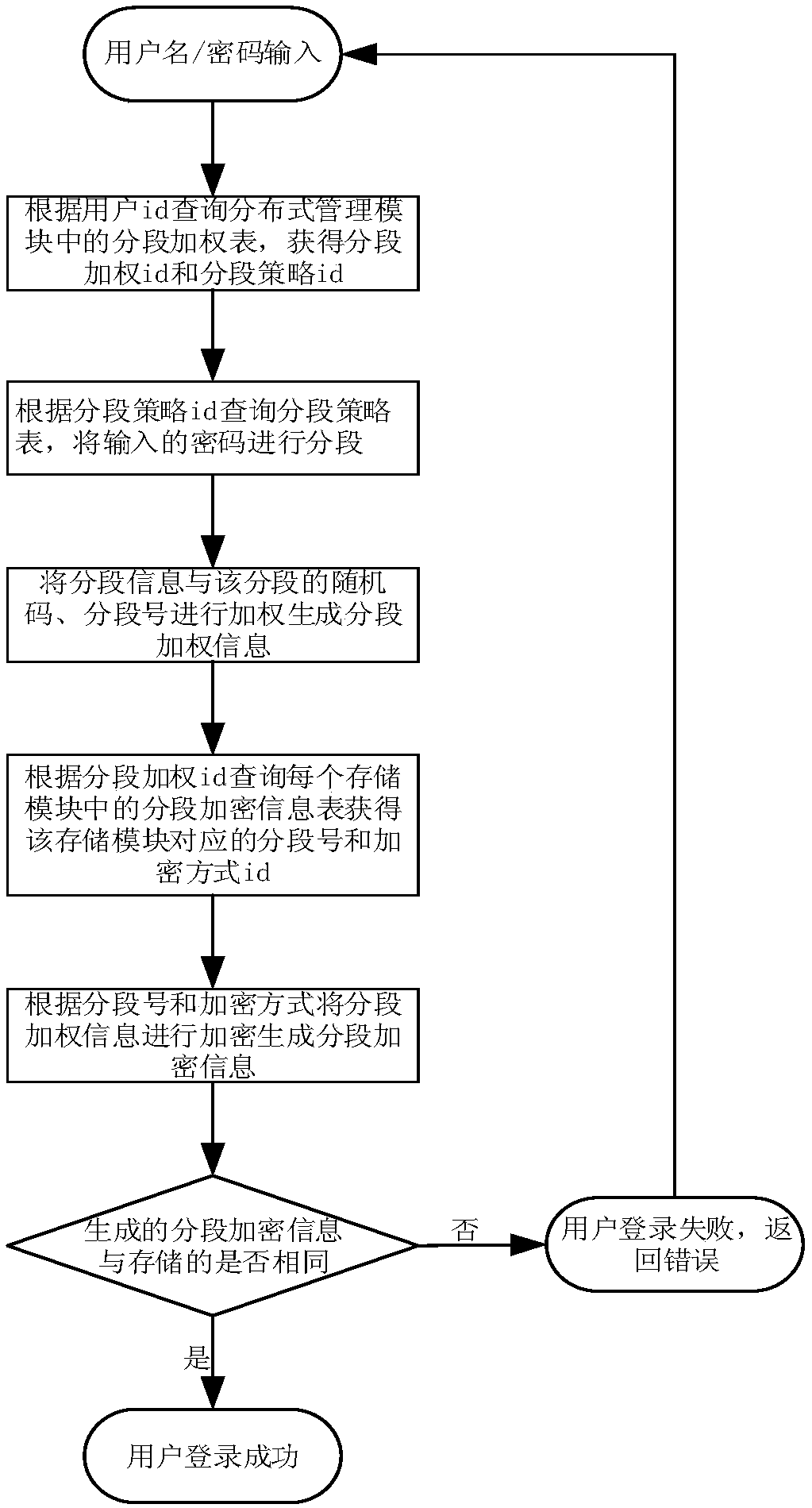
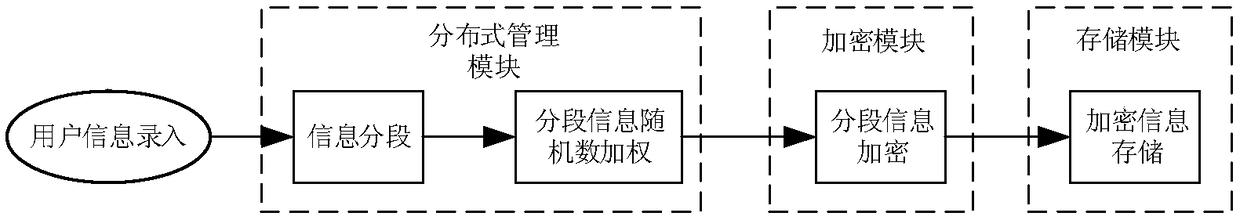
Distributed encrypted storage and authentication method based on local area network
ActiveCN105791274AEffective distributed encrypted storagePrevent leakageTransmissionComputer hardwareEncryption
The invention discloses a distributed encrypted storage and authentication method based on a local area network. The encrypted storage method disclosed by the invention comprises the steps that a distributed management module segments information according to a certain rule, generates a random code based on each segment, carries out weighted confusion based on the segment information, a segment number and the generated random code, and randomly releases the obtained information to a database storage server; and an encryption module encrypts segmented weighting information in a random encryption mode, and then stores the segmented weighting information in a database by a storage module. The authentication method disclosed by the invention is used for carrying out authentication based on the encrypted storage method, and the principle of the authentication method is to carry out segmented encryption on the information again, and then compare the information with actually stored information to judge whether the authentication is successful. The distributed encrypted storage and authentication method disclosed by the invention has the beneficial effects that sensitive information of a user can be effectively stored in a distributed encrypted storage mode to avoid the leakage of all information resulting from the capture of a single storage server.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
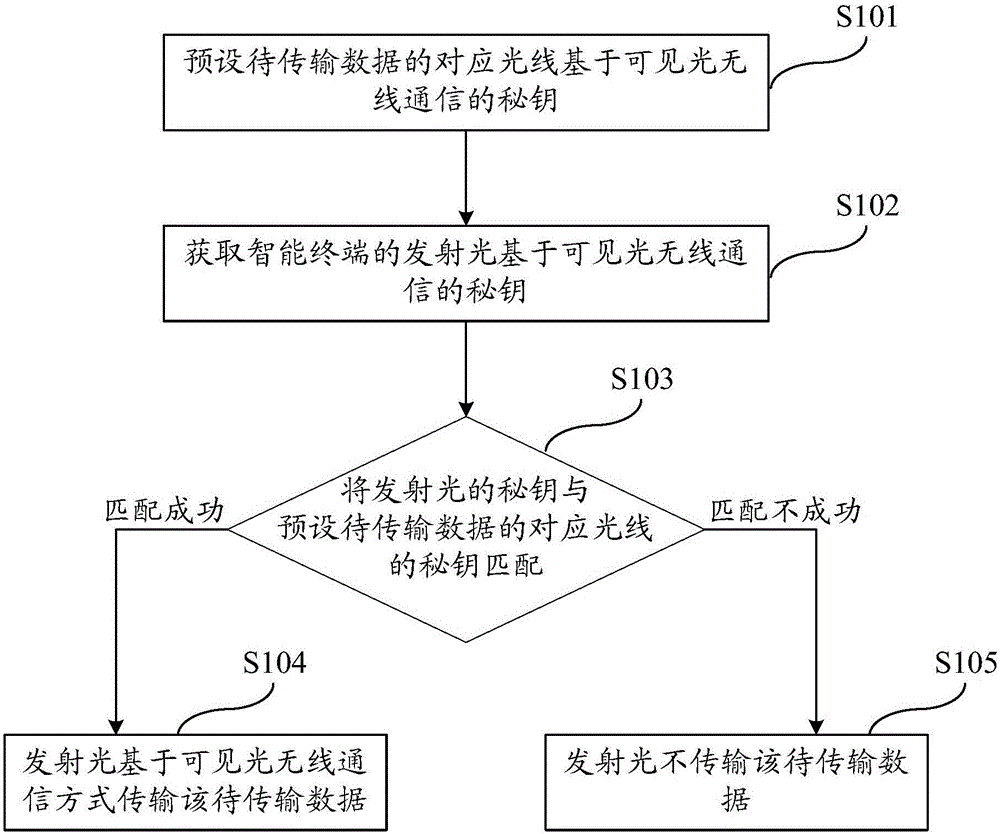
Data encryption transmission method and intelligent terminal
ActiveCN106209895ANot easy to decipherReduce the likelihood of malicious transmissionsKey distribution for secure communicationDigital data protectionComputer hardwareData transmission
The embodiment of the invention provides a data encryption transmission method. The method is applied to an intelligent terminal, and comprises the following steps of: pre-setting a secret key of corresponding light of data to be transmitted based on visible light wireless communication; obtaining a secret key of emission light of the intelligent terminal based on visible light wireless communication; matching the secret key of the emission light with the pre-set secret key of corresponding light of the data to be transmitted; if matching is successful, transmitting the data to be transmitted by the emission light based on a visible light wireless communication manner; and otherwise, not transmitting the data to be transmitted by the emission light. The embodiment of the invention further provides the intelligent terminal. According to the method and the intelligent terminal in the embodiment of the invention, whether the emission light can transmit the data to be transmitted or not is determined by judging whether the secret key of the emission light and the secret key of the corresponding light of the data to be transmitted are successfully matched or not; the fact that the data is difficultly decoded can be ensured; the malicious data transmission possibility is reduced; the transmission data interception possibility is also reduced; and thus, data transmission is relatively simple and safe.
Owner:VIVO MOBILE COMM CO LTD
Method of printing numerical code anti-fake label
InactiveCN101134400ANot easy to decipherVisual representation by matrix printersTypewritersInductorComputer engineering
The present invention relates to anti-fake digital label printing method, and features that the gluing machine is refitted, so that when the printed label passes through the PC controlled code spraying machine, the photoelectric inductor receiving the label signal sends corresponding signal to the PC controlling the code spraying machine and the PC controls the code spraying machine to spray anti-fake digit to each label. The present invention has the advantages including capacity of spraying code in gluing machine and hard deciphering of the sprayed digital code.
Owner:上海怡丽包装材料有限公司
Information verification method and information verification system based on touch screen
InactiveCN102508611AMeet individual needsEasy to rememberDigital data authenticationInput/output processes for data processingGraphicsPersonalization
The invention discloses an information verification method based on a touch screen. The information verification method comprises the following steps of: acquiring standard graphic information currently input by a user through the touch screen and converting the standard graphic information into standard information; acquiring verification information formed by pre-converting the verification graph information which is pre-stored by the user; comparing a characteristic value of the standard information with a characteristic value of the verification information; and when the characteristic value of the standard information is successfully matched with the characteristic value of the verification information, realizing successful verification and otherwise, proving the failure of the verification. According to the information verification method disclosed by the invention, the encryption can be carried out through the graphic information; the encryption mode of a graph is easy to memorize and is not easy to decode by illegal persons; and in addition, the encryption mode of the graph can also meet the requirement of individualization of the user.
Owner:GRG BAKING EQUIP CO LTD
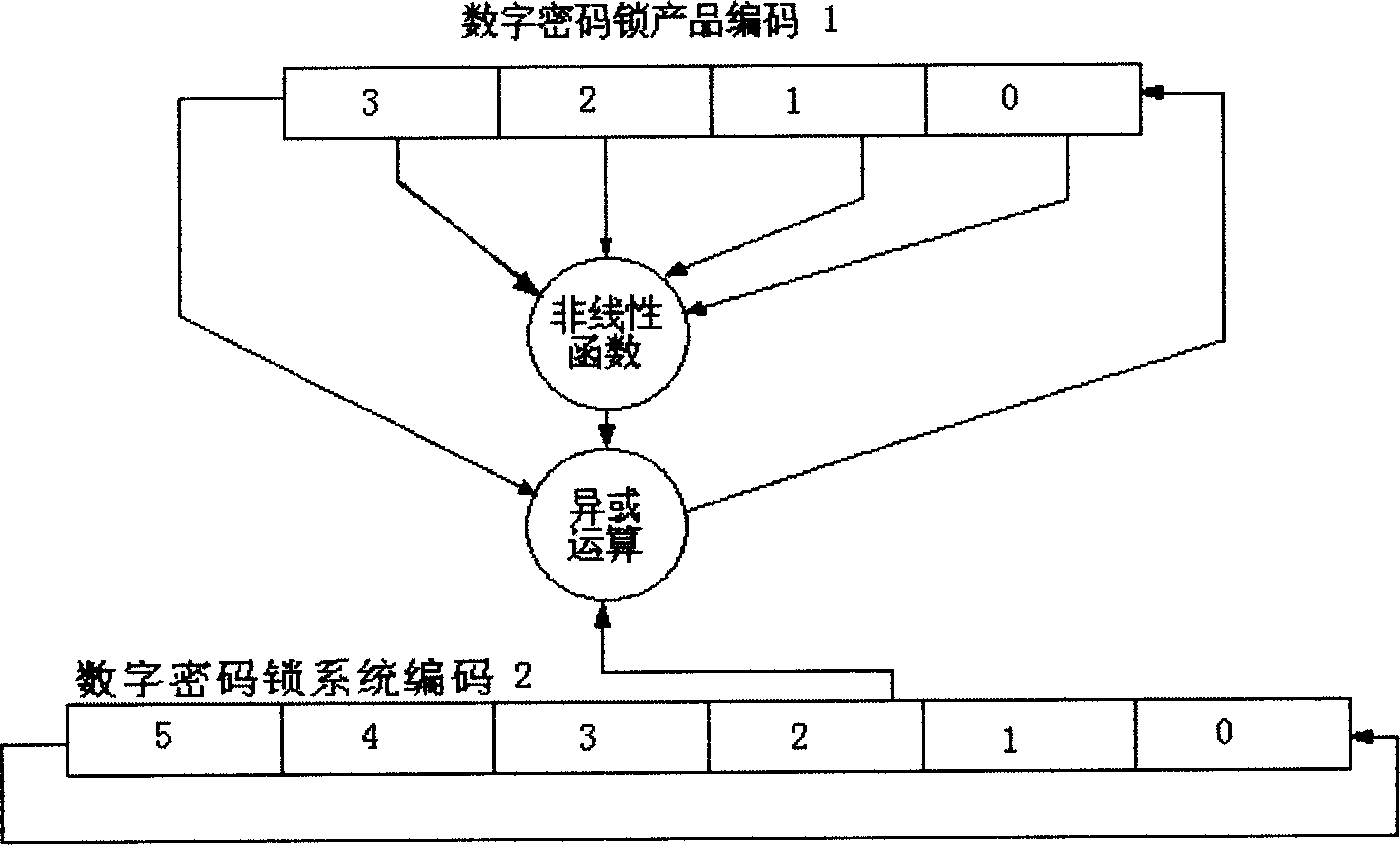
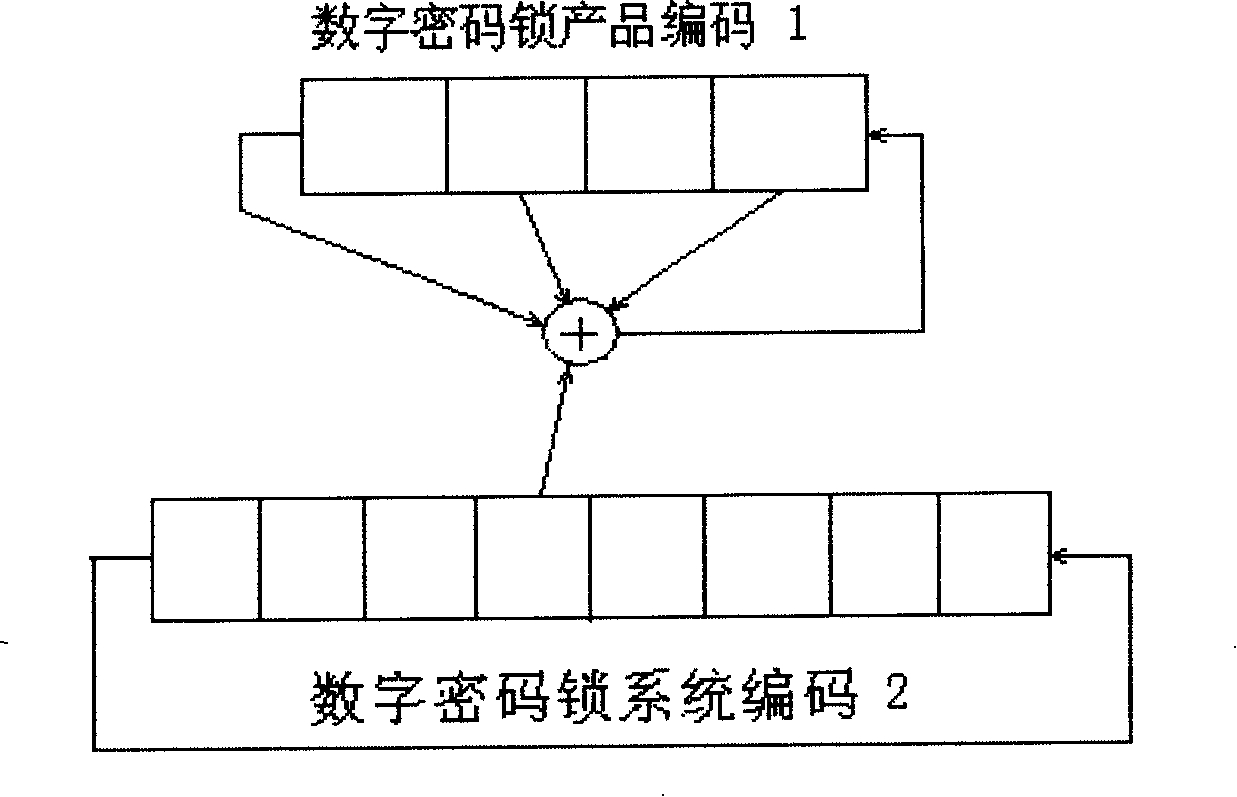
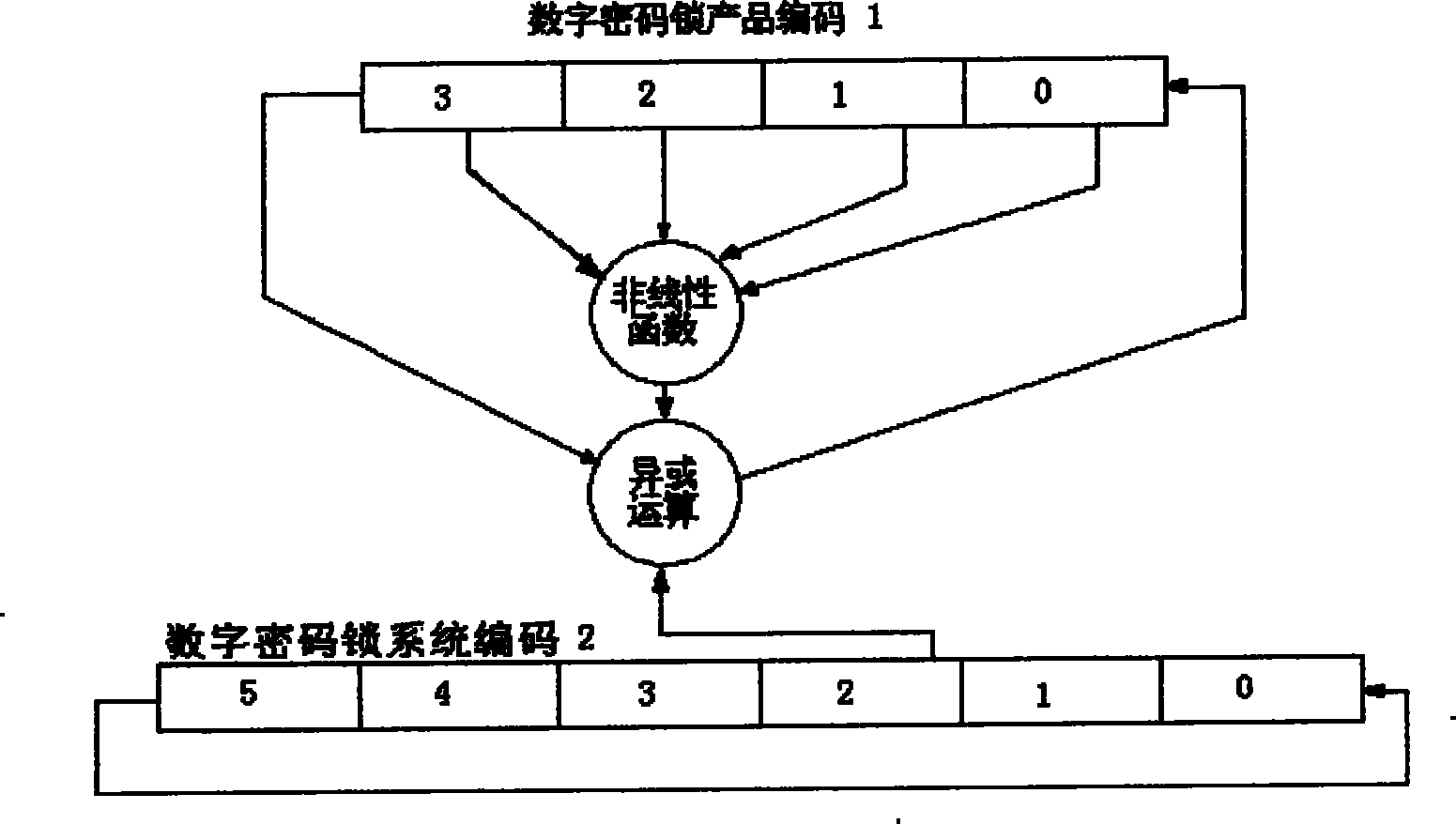
Digital cipher lock with secure secondary authorization unlocking function
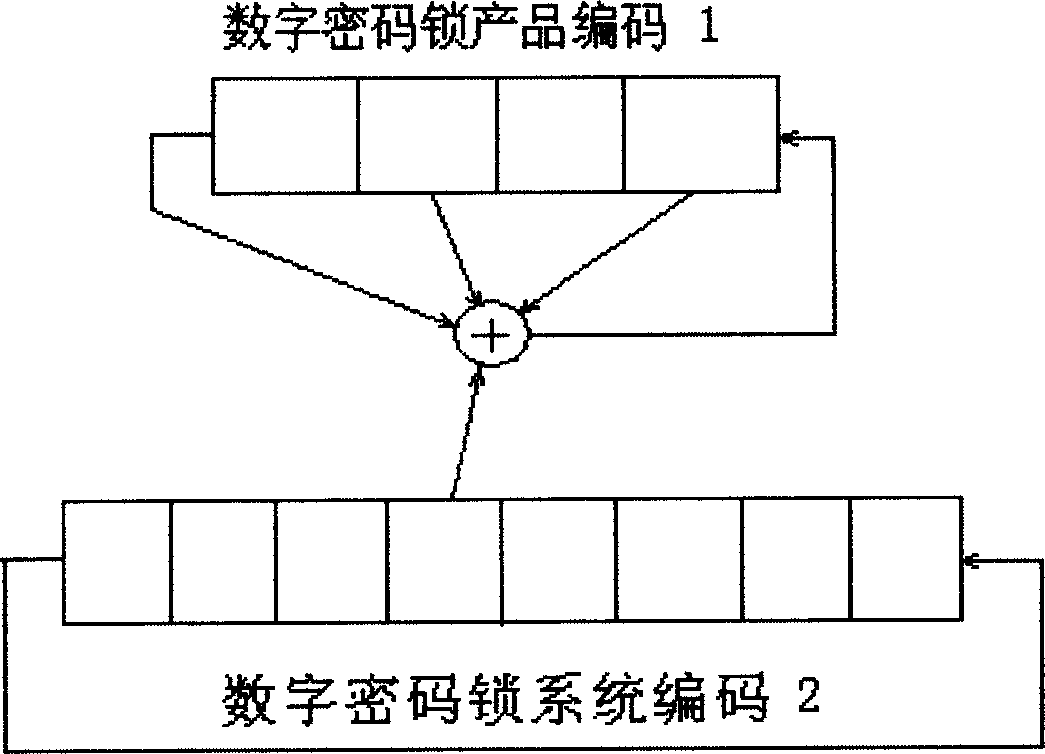
InactiveCN1877060AImprove securityNot easy to decipherElectric permutation locksPersonal computerComputer science
The invention relates to a digit code lock technique and relative system. Wherein, it uses the digit encrypt technique to solve the problem of second authorization unlocking when the user forgets the unlock code. It is characterized in that: the code generator software of personal computer and the code lock embedded system with relative algorism form said invention; when unlocking, the code generate software uses digit encrypt technique on one group of digit code that stored in the digit lock embedded system to generate code; the code lock embedded system also uses the same digit encrypt technique to calculate the same code to generate another code; then inputting the code of code generate software into digit lock embedded system, and the embedded system compares the input code with itself code, if they are same, authorizing it and unlocking the digit lock; or else, rejecting. The invention has better safety, high anti-impact ability and easy management.
Owner:黄涛
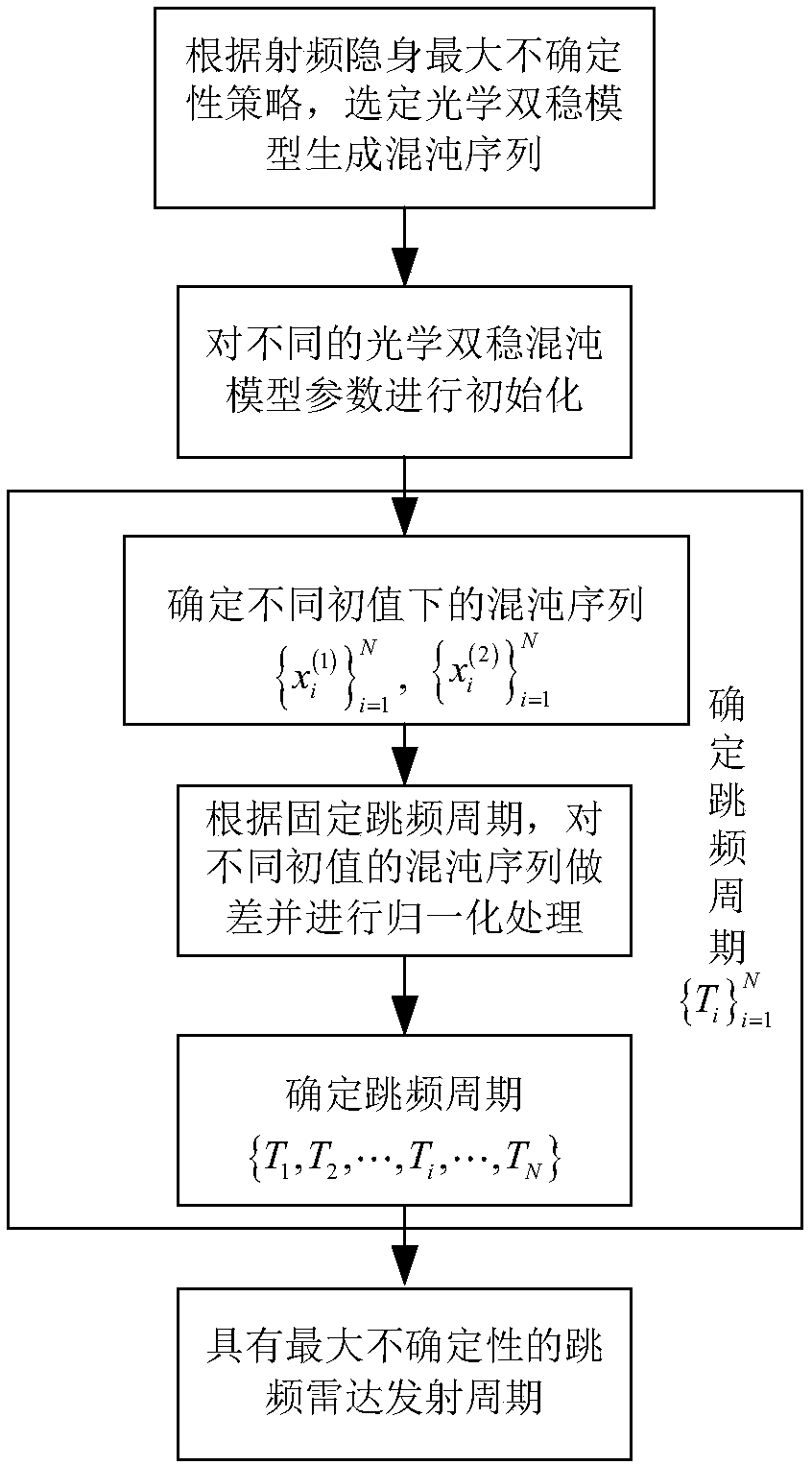
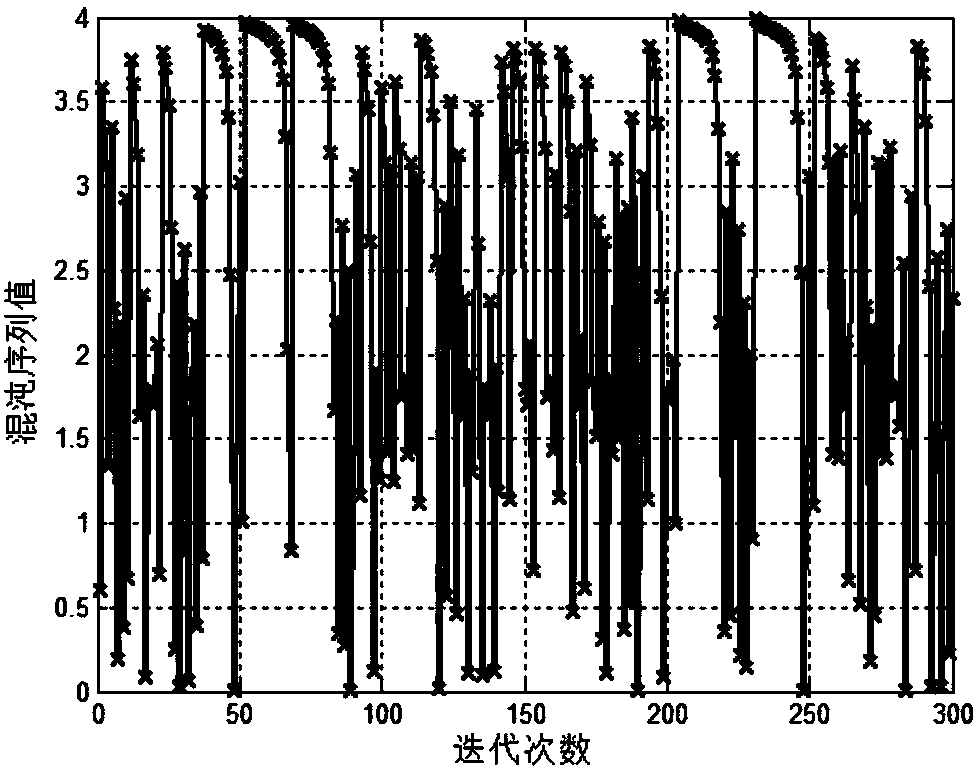
Frequency hopping radar transmission period design method based on optical bistable chaotic model
InactiveCN108089163AGuaranteed Maximum UncertaintyMaximum Uncertainty SatisfactionWave based measurement systemsRadar systemsAdaptive optimization
The invention discloses a frequency hopping radar transmission period design method based on an optical bistable chaotic model. The method is characterized in that taking the maximization of the uncertainty of the frequency hopping period of a radar system as an optimization objective, the optical bistable model in the chaotic theory is utilized to generate a chaotic sequence with the pseudo-random, quasi-noise and non-periodic characteristic changes, and the mapping and normalization processing on the sequence in a radar frequency hopping period space is carried out, so that the self-adaptionoptimization design is carried out on the radar frequency hopping transmission period. The beneficial effects of the invention are that an optical bistable chaotic model is used for carrying out theoptimization design on the radar frequency hopping transmission period, and the frequency hopping period with the pseudo-random, quasi-noise and non-periodic characteristic changes, the maximum uncertainty of the signal parameters of the frequency hopping radar is maximized, and therefore the radio frequency stealth performance of the radar system is improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Terminal communication voice encryption method and system
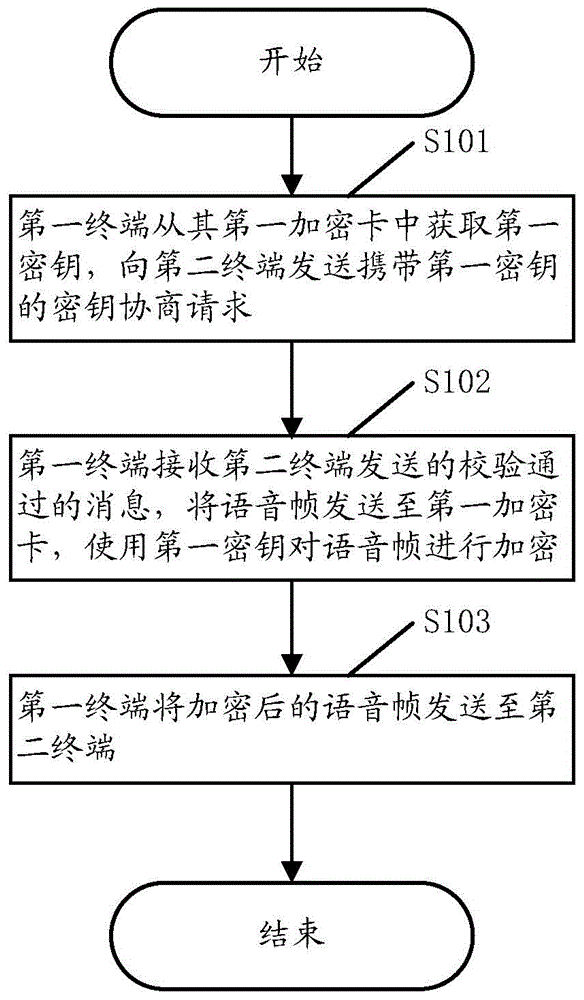
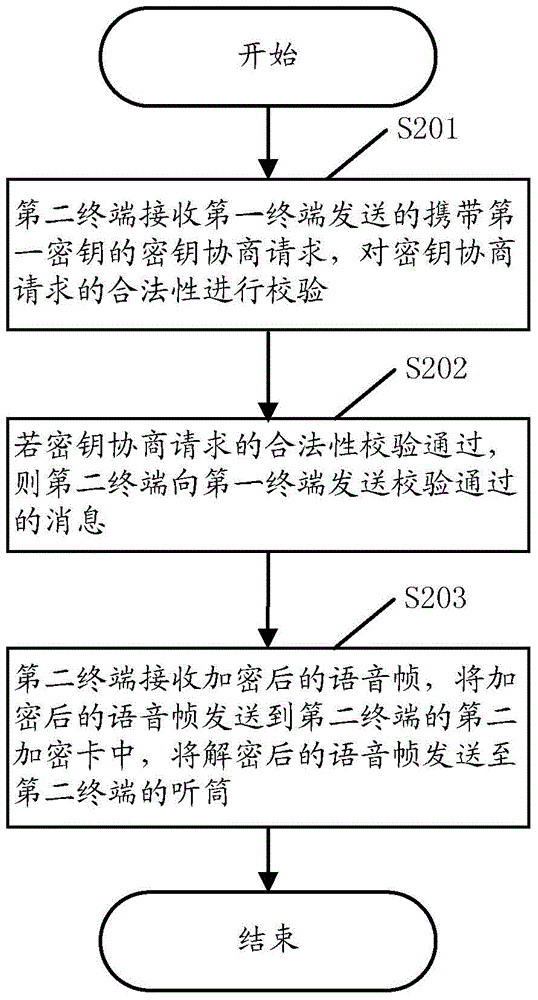
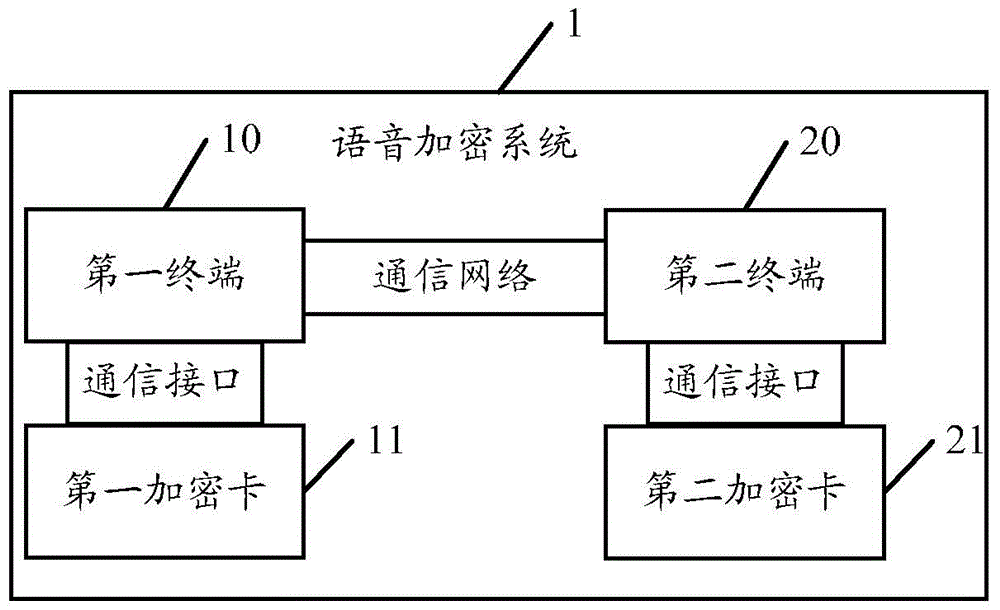
InactiveCN104640108ANot easy to decipherImprove securitySecurity arrangementComputer terminalSpeech sound
The embodiment of the invention discloses a terminal communication voice encryption method and system. The method comprises the following steps: obtaining a first secret key from a first encryption card of a first terminal by the first terminal and sending a secret key negotiation request carrying the first secret key to a second terminal; receiving a message which is sent by the second terminal and shows that validation is passed; sending a voice frame to the first encryption card and encrypting the voice frame by using the first secret key; sending the encrypted voice frame to the second terminal. According to the terminal communication voice encryption method disclosed by the embodiment of the invention, communication voices are encrypted by a dynamic secret key and are not easy to decode, so that the safety is higher.
Owner:SHENZHEN BVC SCI & TECH
Fourth-order network multi ring surface chaos circuit and its use method
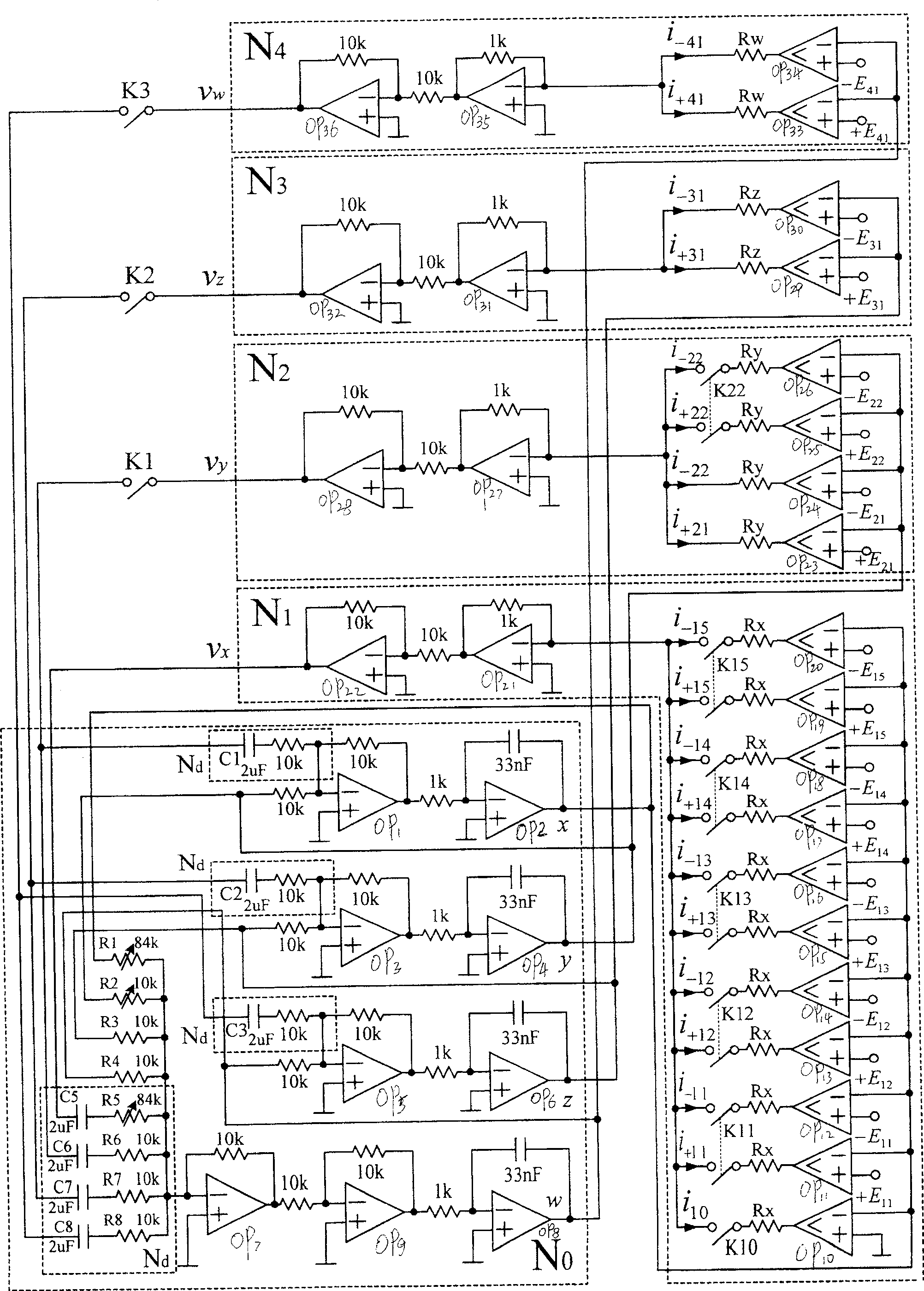
ActiveCN100486154CNot easy to decipherImprove reliabilitySecuring communicationHemt circuitsEngineering
The invention is related to chaos circuit needed by secret communication. The invention includes basic quadravalent cancellate chaos circuit in multiple tori, step wave sequence generation circuits in x, y, z directions, and switch bank. The method includes steps: disconnecting K1, K2, K3 generates single directional chaos attractors in multiple tori; through switching K10-K15 controls quantity of control tori; connecting K1, and disconnecting K2, K3 generate 2D distributed cancellate chaos attractors in multiple tori; through switching K10-K15, K22 controls quantity of chaos attractors in multiple tori; connecting K1, K2, K3 generate 4D distributed cancellate chaos attractors in multiple tori.
Owner:安徽行者智能科技股份有限公司
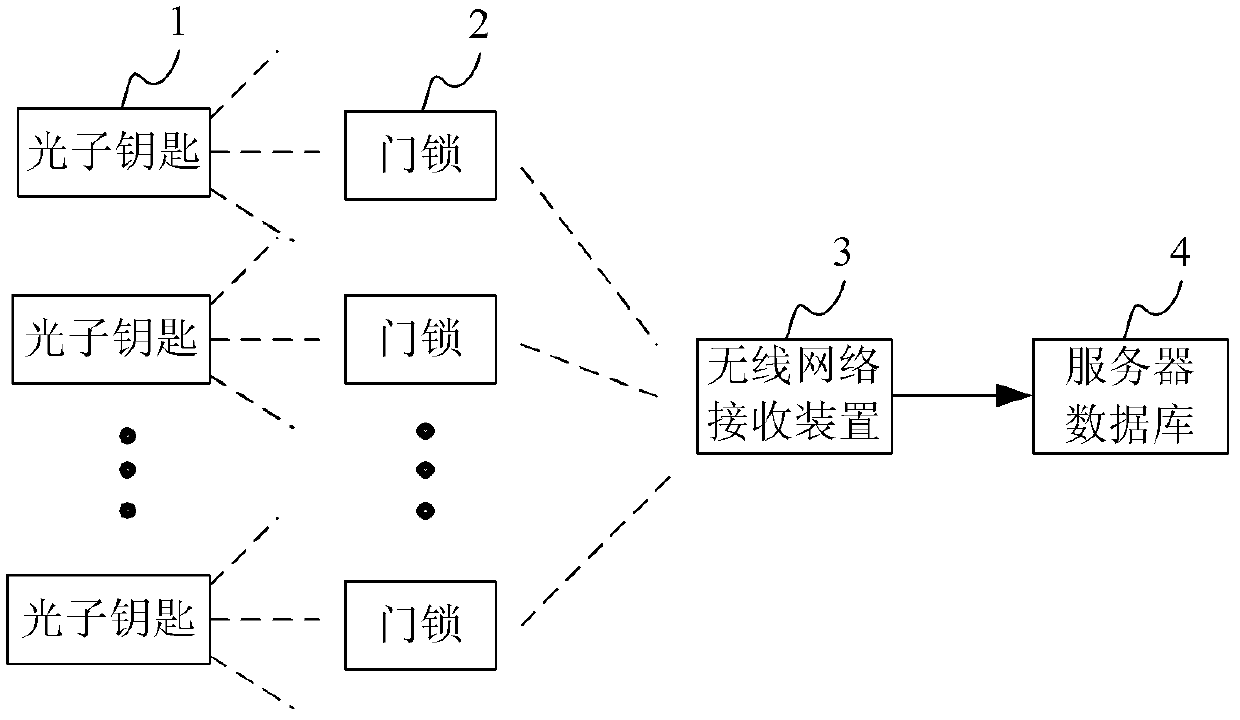
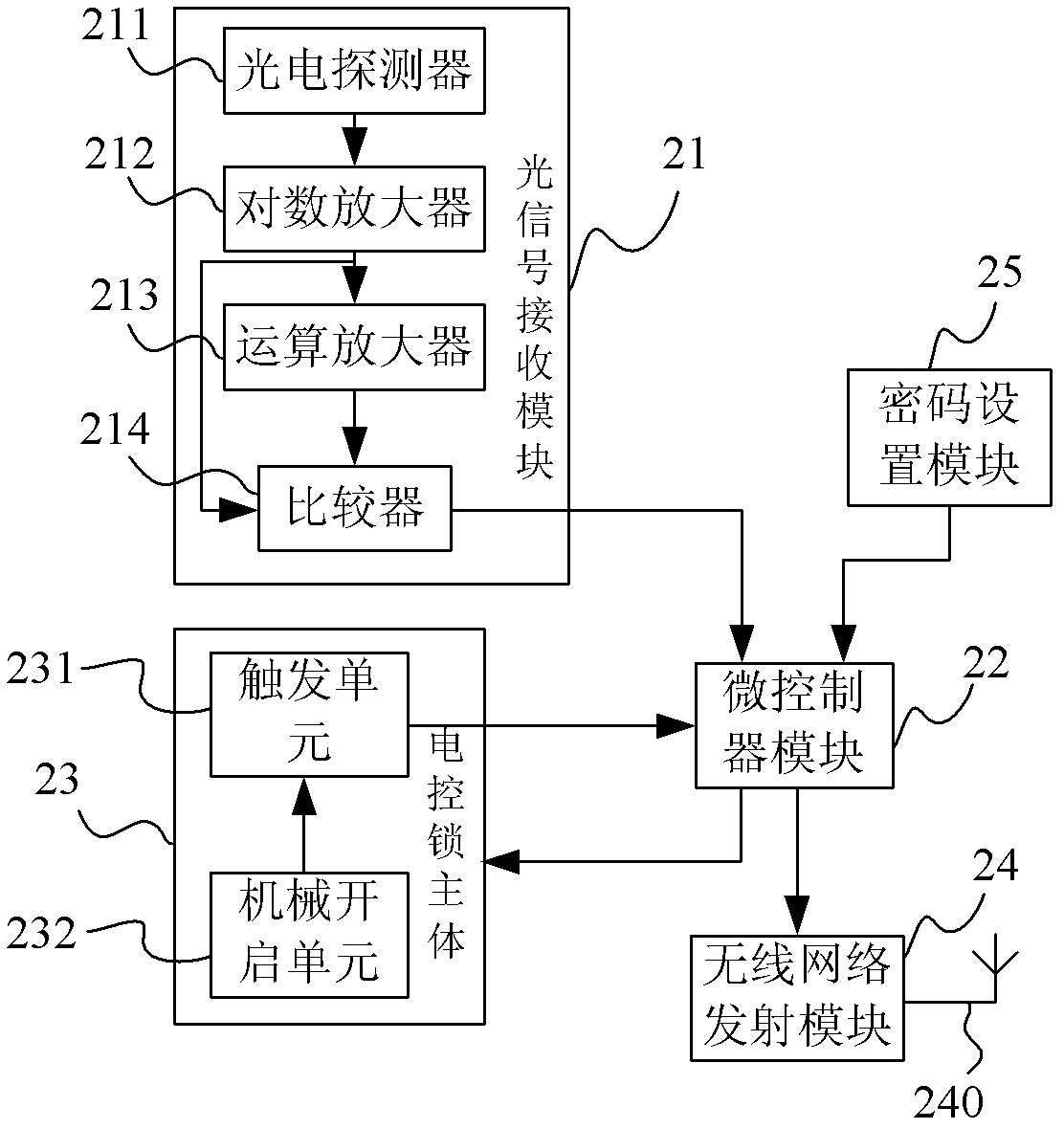
Photon lock door control system based on wireless network
ActiveCN103295289ANot easy to decipherImprove securityIndividual entry/exit registersControl systemEngineering
The invention relates to a photon lock door control system based on a wireless network. The photon lock door control system comprises a photon key, a door lock, a wireless network receiving device and a server database, wherein the photon key is used for transmitting an optical signal containing information; the door lock comprises a wireless network transmission module and is used for responding to the optical signal and transmitting the information of the door lock through the wireless network transmission module; the wireless network receiving device is used for receiving the information transmitted from the wireless network transmission module and transmitting the information to the server database through a network. According to the photon lock door control system disclosed by the invention, the photon key transmits an unlocking instruction to the door lock in a form of the optical signal, the optical signal is not easily decoded and thus the safety is high; the door lock transmits the door lock information to the network in a wireless manner through the wireless network transmission module and wiring is not needed, so that physical connection of equipment is reduced and the expansion is facilitated; the information capacity of the server database is large so as to be convenient for non-developers to operate and control the database.
Owner:KUANG CHI INTELLIGENT PHOTONIC TECH
Data processing method and terminal
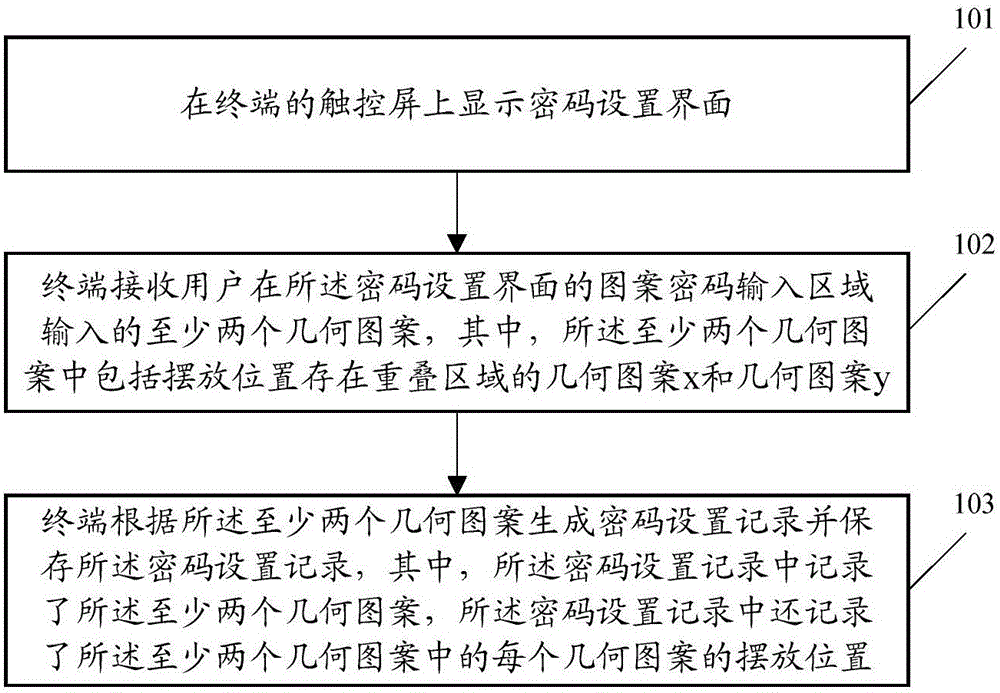
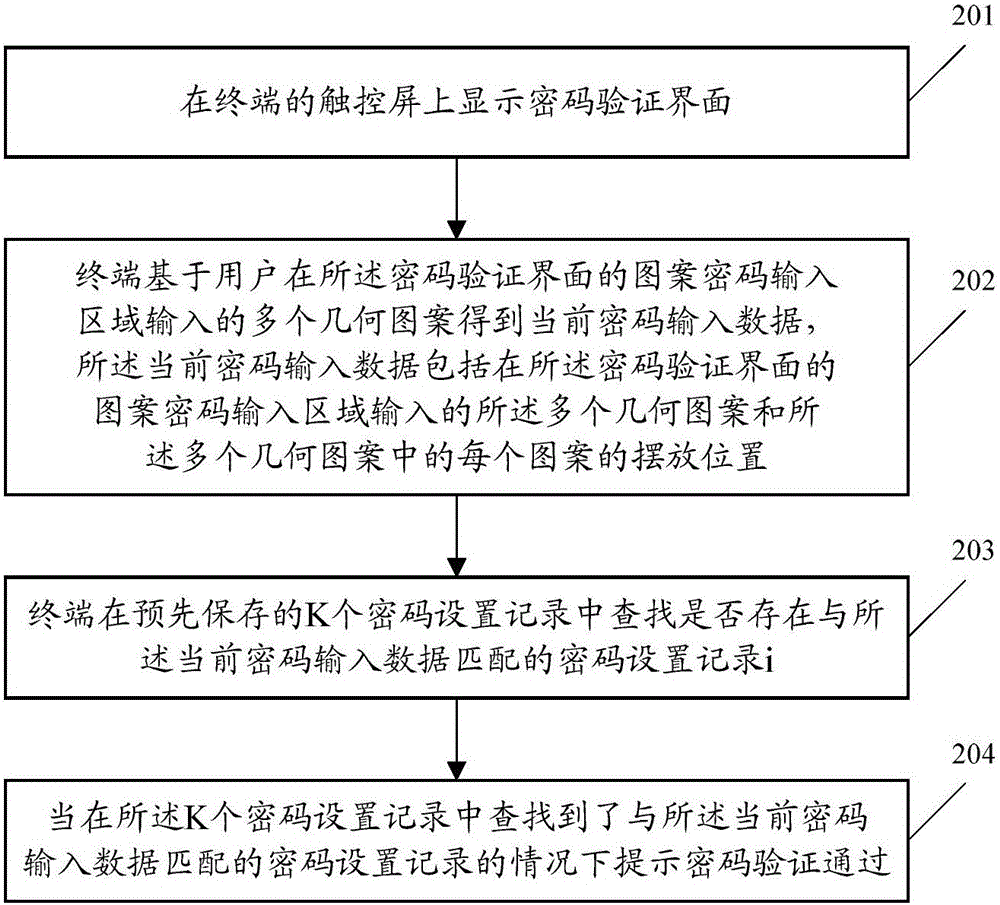
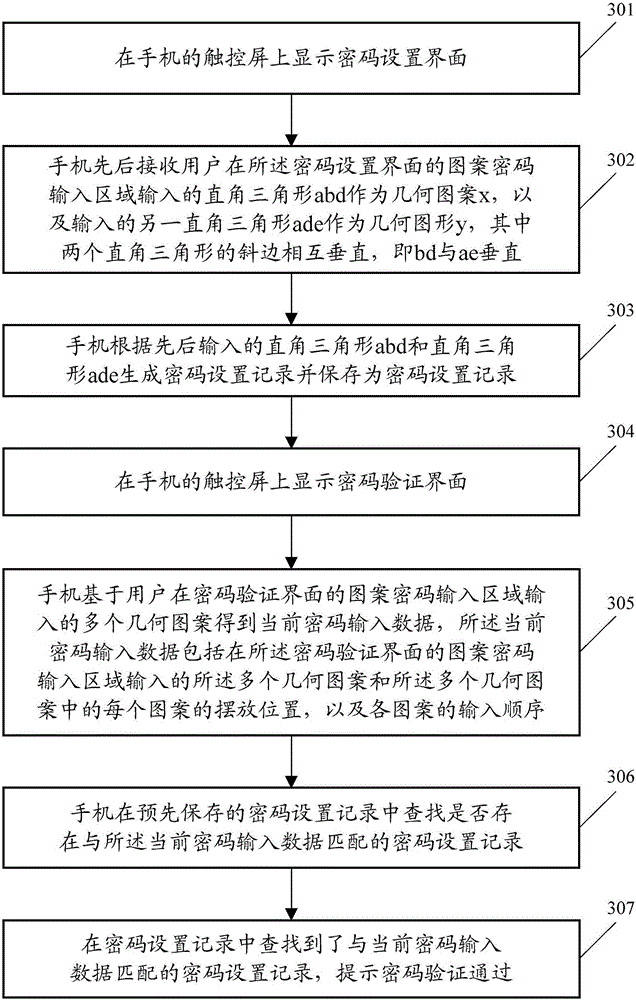
ActiveCN105760749ANot easy to decipherImprove securityDigital data authenticationPasswordComputer vision
The embodiment of the invention discloses a data processing method and a terminal, wherein the data processing method comprises the following steps: displaying a password setting interface on a touch screen; receiving at least two geometric patterns inputted by a user at a pattern password input area of the password setting interface, wherein the at least two geometric patterns include geometric patterns x and geometric patterns y with overlapped areas at placing positions; generating password setting records according to the at least two geometric patterns and storing the password setting records, wherein the password setting records record the at least two geometric patterns and also record the placing position of each geometric pattern in the at least two geometric patterns. When the technical scheme provided by the embodiment of the invention is adopted to process data as passwords, the set passwords cannot be decoded easily, so that the security of password setting is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Identity recognition system based on a computer network
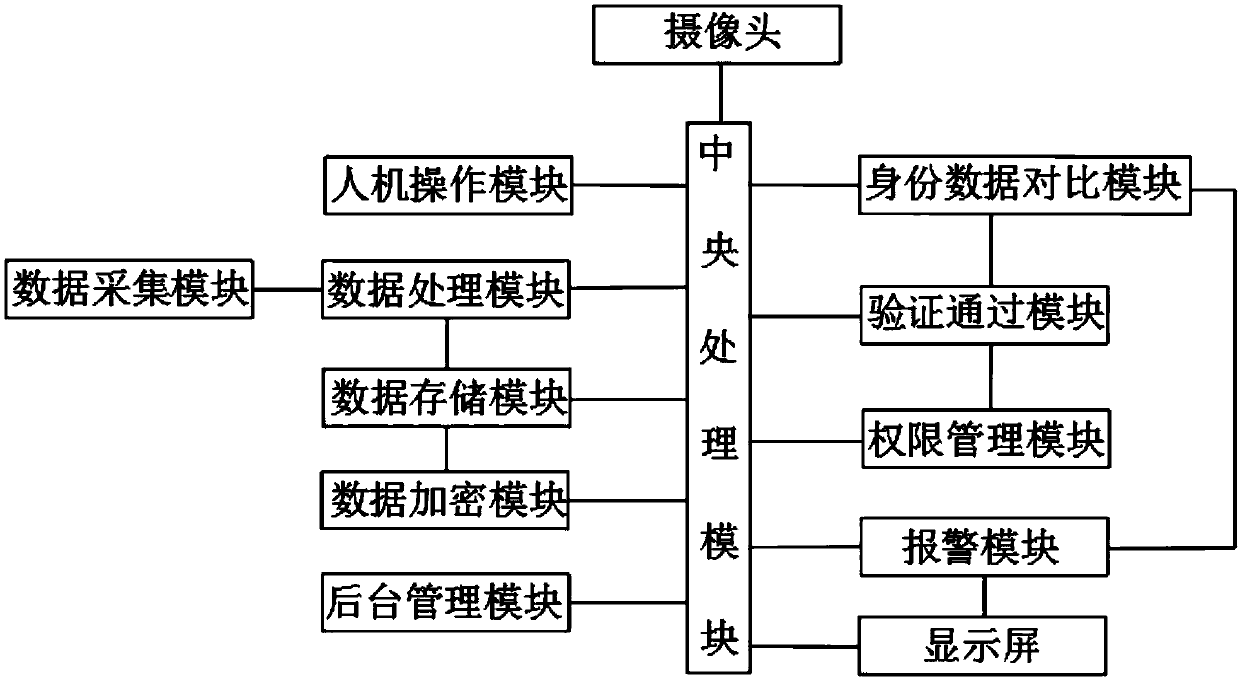
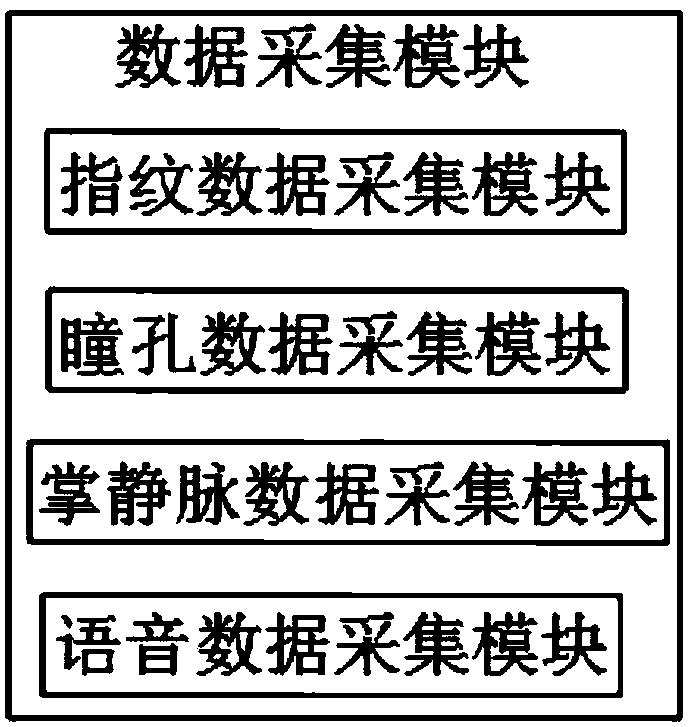
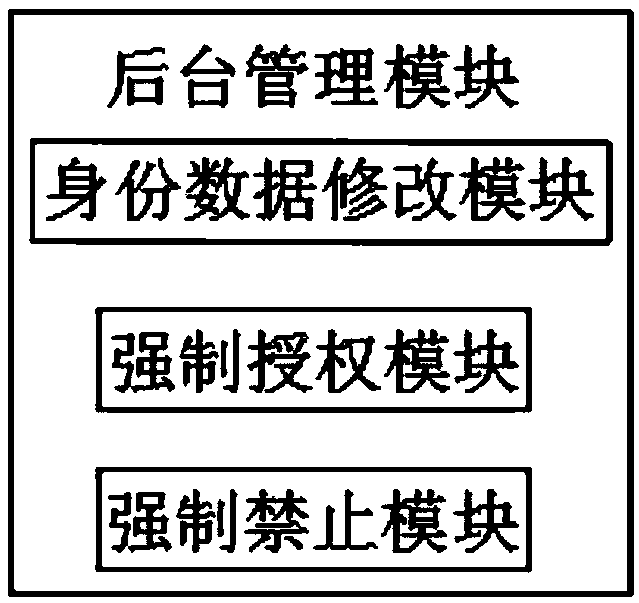
PendingCN109522694AFlexible adjustment of identity permissionsImprove securityDigital data protectionDigital data authenticationIdentity recognitionData acquisition
The invention discloses an identity recognition system based on a computer network, which relates to the technical field of identity recognition and comprises a man-machine operation module, a data acquisition module, a data processing module, a data storage module, a data encryption module, a background management module, an identity data comparison module, a verification passing module, an authority management module and an alarm module. According to the invention, various biological characteristic identity verification modes are adopted; Identity authentication of an operator, an operator does not need to record complex and tedious passwords; The system is simple in structure, high in safety coefficient, not prone to being stolen or decoded, capable of flexibly adjusting the identity permission of a client according to actual needs, capable of giving an alarm in time and recording the facial features of a displacer if masquerading displacement or other violation operations are found, and very suitable for an identity recognition system based on a computer network.
Owner:SHENGDA ECONOMICS TRADE & MANAGEMENT COLLEGE OF ZZ
Multifunctional offline password verification method for electronic lock
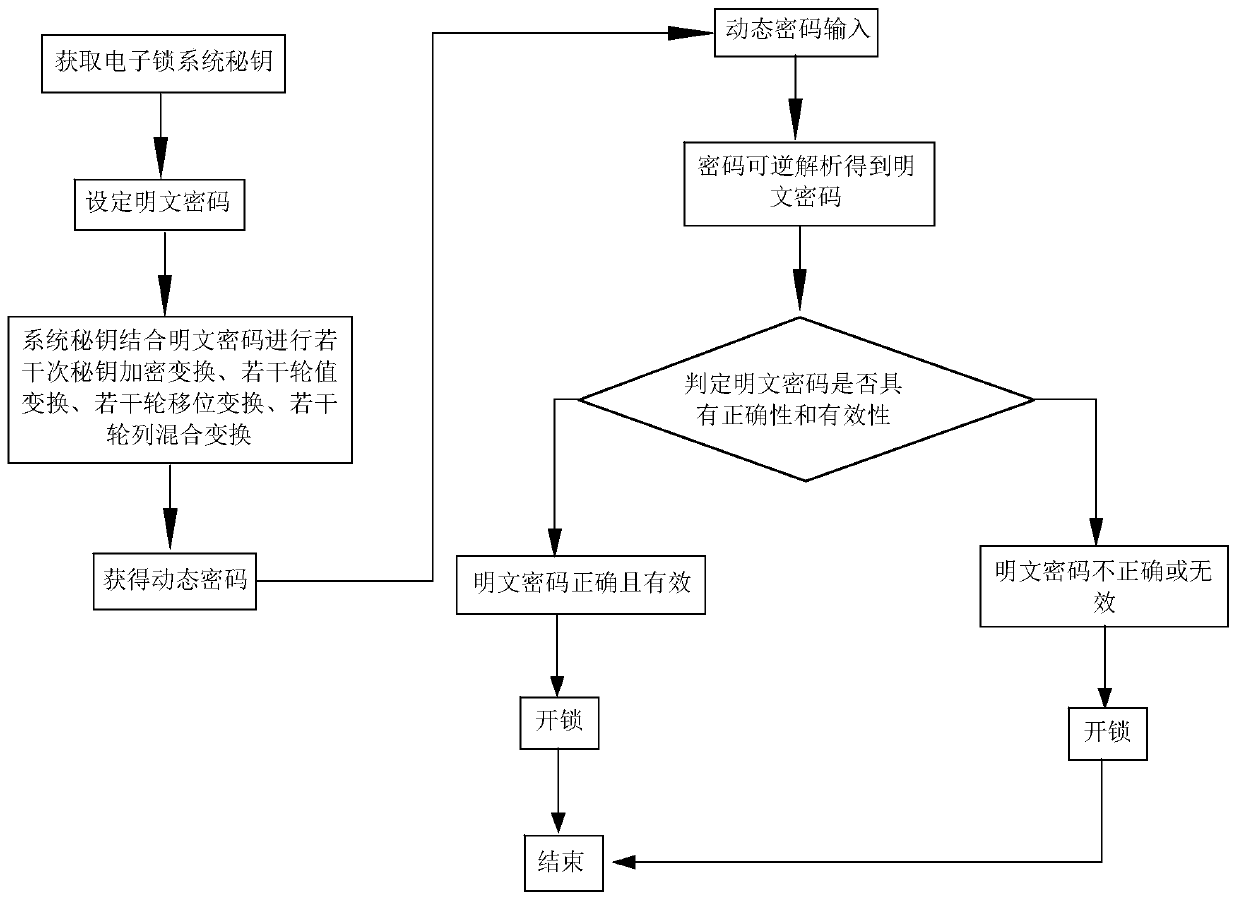
ActiveCN110022205AImprove analysis efficiencyImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPlaintextPassword
The invention discloses a multifunctional offline password verification method of an electronic lock. The method comprises steps of generating a plaintext password according to submitted information;obtaining a system secret key in the electronic lock, wherein the plaintext password is subjected to several rounds of secret key encryption transformation according to the encryption strategy and thefour groups of eight-bit secret key values; carrying out a plurality of rounds of value transformation, a plurality of rounds of shift transformation and a plurality of rounds of column hybrid transformation to obtain a dynamic password; analyzing to obtain the plaintext password; and if the plaintext password obtained through analysis has correctness and effectiveness, unlocking by the electronic lock. Compared with the prior art, the method has the beneficial effects that the plaintext password contains the information of the password type, so that the password type information and the digital password can be obtained only by one-time analysis in the analysis process, and the analysis efficiency is improved; meanwhile, encryption is carried out through 16 times of reversible encryptionalgorithms, so that decoding is not easy, and the security performance is greatly improved; and the length of the dynamic password for unlocking is 8-9 bits, so that the dynamic password is convenientto memorize.
Owner:浙江久婵物联科技有限公司
Anti-counterfeit pen and anti-counterfeit label
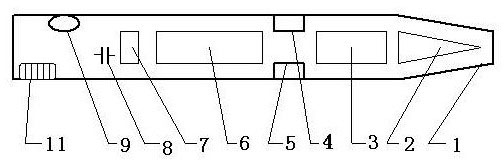
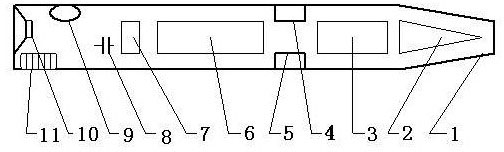
InactiveCN102147850ALow priceNot easy to decipherRecord carriers used with machinesSensing by electromagnetic radiationEngineeringLicense
The invention relates to an anti-counterfeit technology and an anti-counterfeit device, in particular to an anti-counterfeit pen and an anti-counterfeit label. When the anti-counterfeit label is arranged on printing money, an entrance ticket, a moon cake ticket, an identification card, a driving license, a famous tobacco, a famous wine, a drug, a health care product, furniture, clothing, shoes and hats, the anti-counterfeit pen can tell the authenticity of products in a visual and readable way by pointing the anti-counterfeit label. The anti-counterfeit pen comprises a shell which is internally provided with a photoelectric sensor recognizing anti-counterfeit coding information, a mother board, a power source and an anti-counterfeit information output unit; a signal output end of the photoelectric sensor recognizing the anti-counterfeit coding information is connected with a signal input end of the mother board with the functions of information identification, information comparison and judgment and anti-counterfeit signal output; and the anti-counterfeit signal output end is connected with the anti-counterfeit information output unit. The anti-counterfeit label comprises a label bottom layer, an anti-counterfeit coding layer and a pattern layer. The anti-counterfeit pen and the anti-counterfeit label mainly solve the problem that the existing anti-counterfeit technology is not easy to operate by a user due to wide varieties and are beneficial to the unification of the anti-counterfeit technology.
Owner:黄丽娜
Intelligent antitheft alarm device adopting key
InactiveCN103839317AEasy to operateMany internal codesIndividual entry/exit registersAlarm locksElectric machineThe Internet
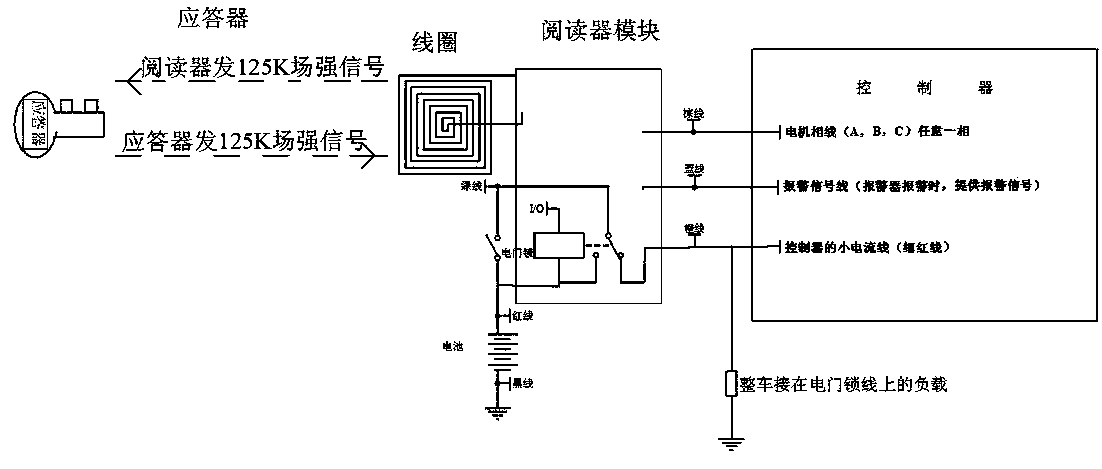
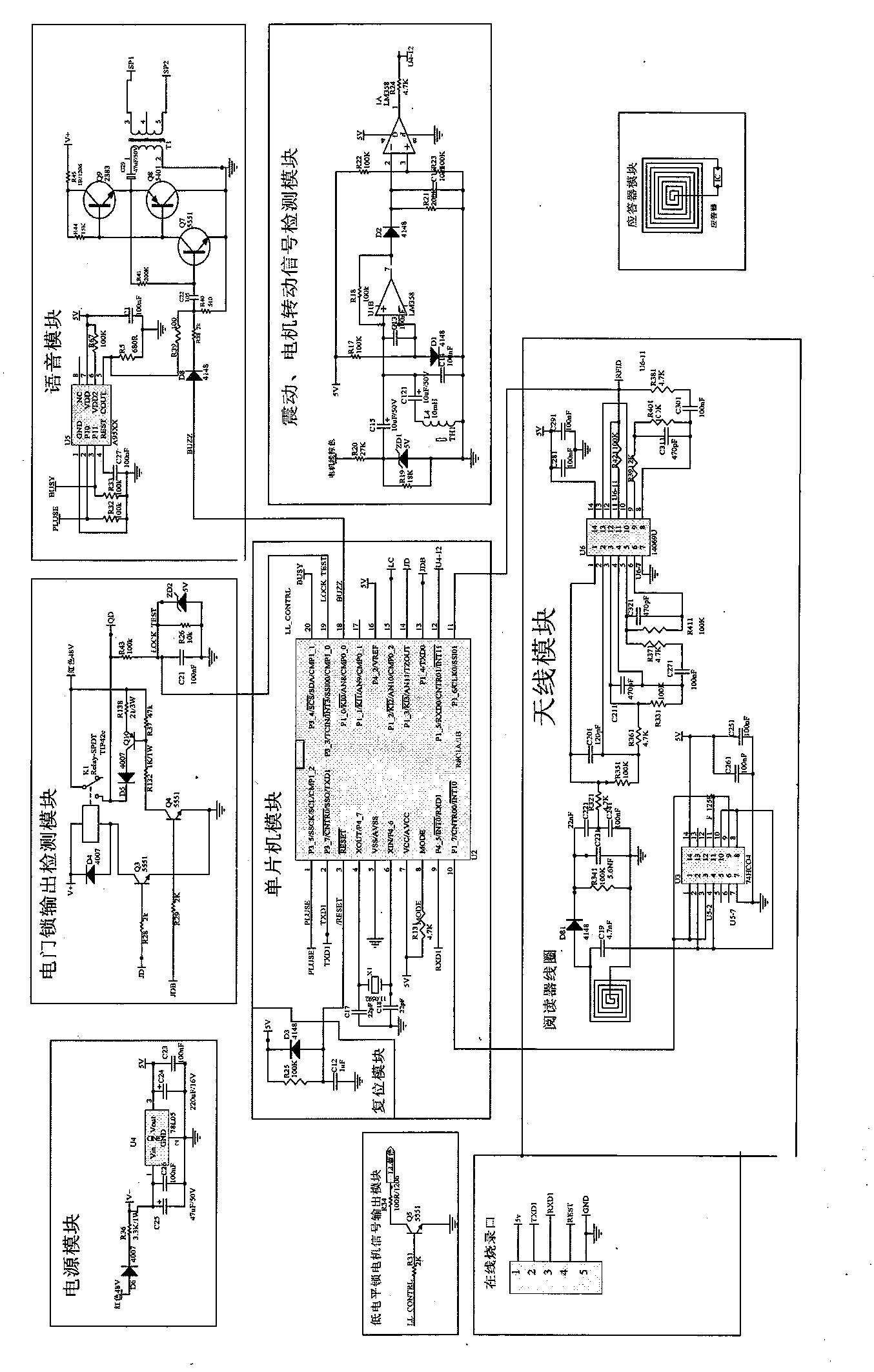
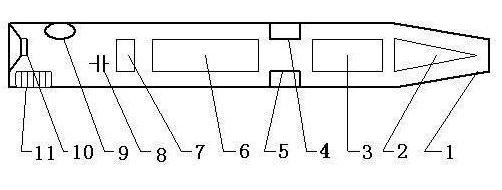
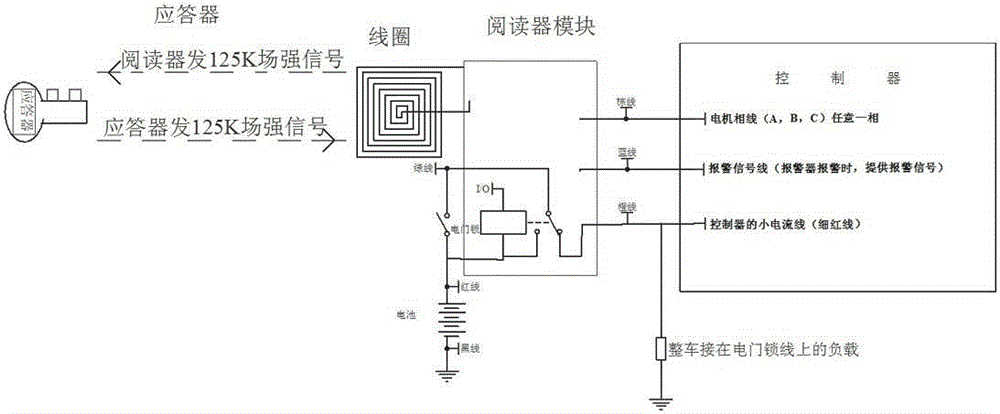
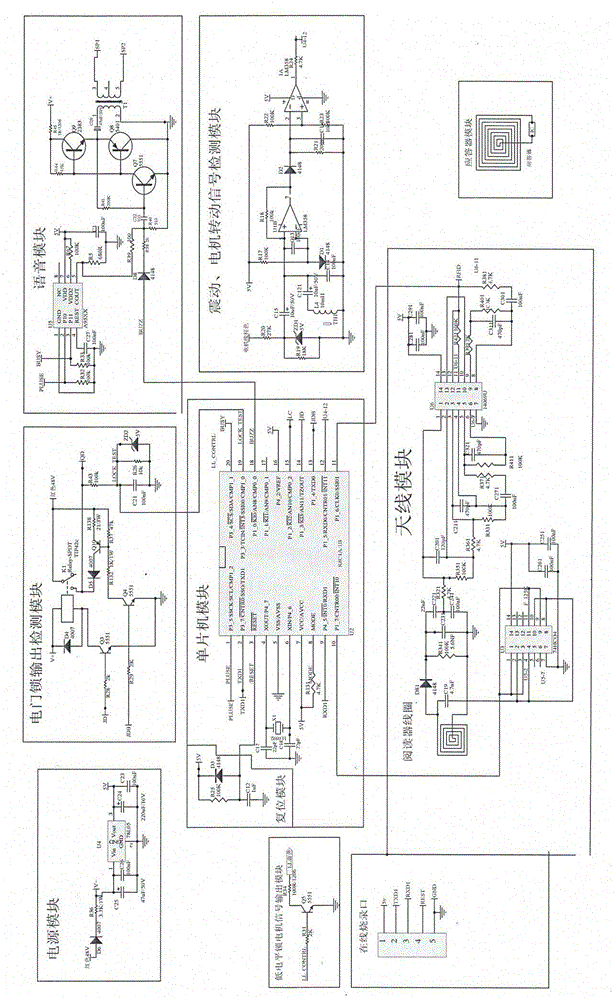
The invention discloses an intelligent antitheft alarm device adopting a key. A circuit board and a buzzer sheet are arranged in a shell cavity composed of an upper shell and a lower shell to form the alarm device; six wires are led out of the lower side of the shell and comprise a 48-V power wire, a grounding wire, an electric door locking wire, a motor rotation detection wire and a 125K antenna coil. Due to an RFID (radio frequency identification) technology for the internet of things, the identity of the key is unique and a repeated code value does not exist; even if the key is copied by others, the copied key cannot open a door; mutual opening rate is zero; meanwhile, the warning sound can frighten an opener to enable the opener to stand in awe before opening the door and not get close to the door; people feel safe and quick.
Owner:淮安市金恒泰科技有限公司
Digital cipher lock with secure secondary authorization unlocking function
InactiveCN1877060BImprove securityNot easy to decipherElectric permutation locksSecret codePersonal computer
The invention relates to a digit code lock technique and relative system. Wherein, it uses the digit encrypt technique to solve the problem of second authorization unlocking when the user forgets the unlock code. It is characterized in that: the code generator software of personal computer and the code lock embedded system with relative algorism form said invention; when unlocking, the code generate software uses digit encrypt technique on one group of digit code that stored in the digit lock embedded system to generate code; the code lock embedded system also uses the same digit encrypt technique to calculate the same code to generate another code; then inputting the code of code generate software into digit lock embedded system, and the embedded system compares the input code with itself code, if they are same, authorizing it and unlocking the digit lock; or else, rejecting. The invention has better safety, high anti-impact ability and easy management.
Owner:黄涛
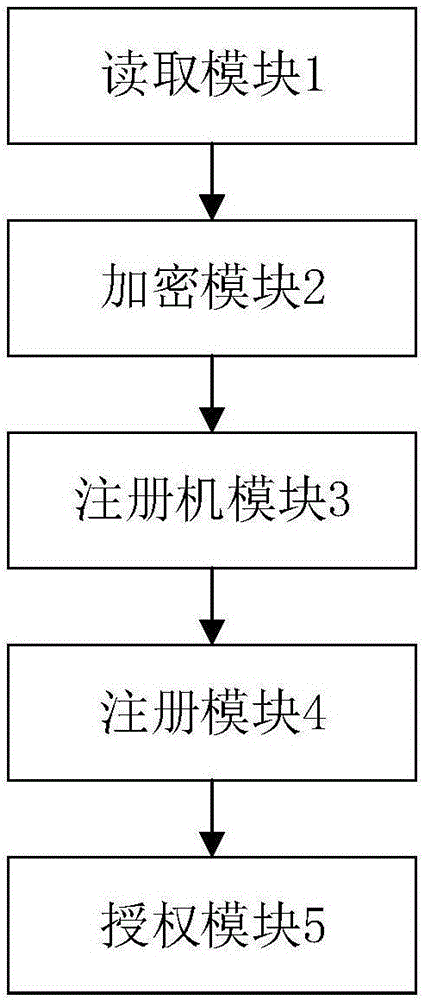
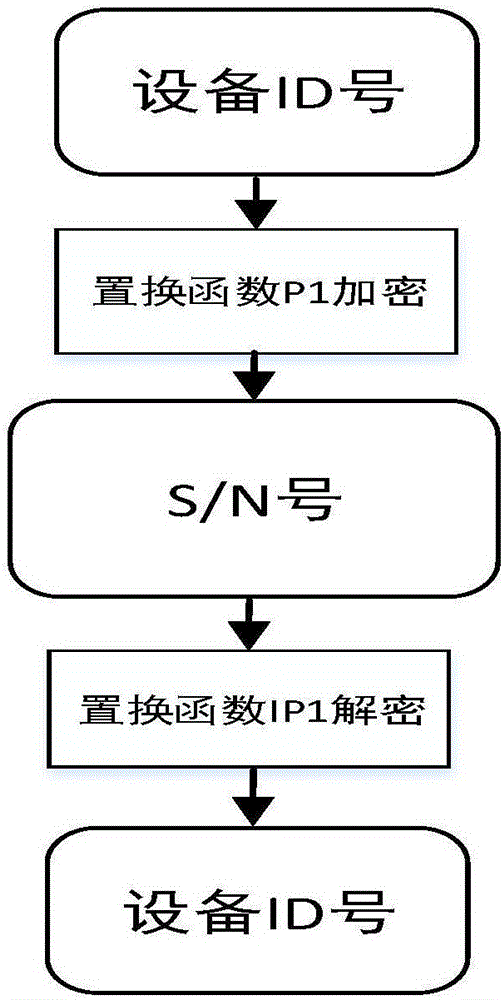
Receiver board card
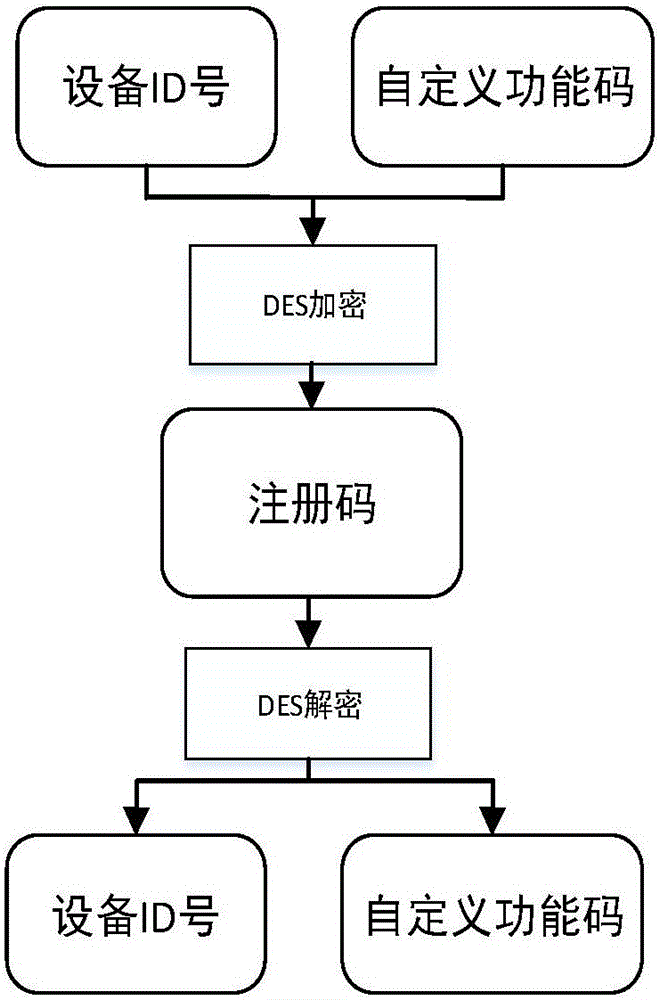
InactiveCN106850202AImprove experienceEasy to manageKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAuthorizationEncryption
The invention provides a receiver board card, comprising a reading module which is used for reading a device number of the receiver board card; an encryption module which is used for encrypting and outputting a device ID number and a self-defined function code of a receiver; a registration machine device which is used for generating a corresponding registration code according to the encrypted device ID number and self-defined function code output by a hardware platform of the board card device; a registration module which is used for receiving the registration code generated by a registration machine and inputting the registration code into the board card for decryption authorization, thereby restoring the registration code into the device ID number and the self-defined function code; and an authorization module which is used for carrying out corresponding operation on the receiver board card according to the decoded self-defined function code. According to the receiver board card, one-machine one-code is realized in an authorization process, and management and operation are convenient. According to the receiver board card, the user experience is conveniently, efficiently and effectively improved in the authorization process.
Owner:SHANGHAI HUACE NAVIGATION TECH
Bluetooth device addition method and system
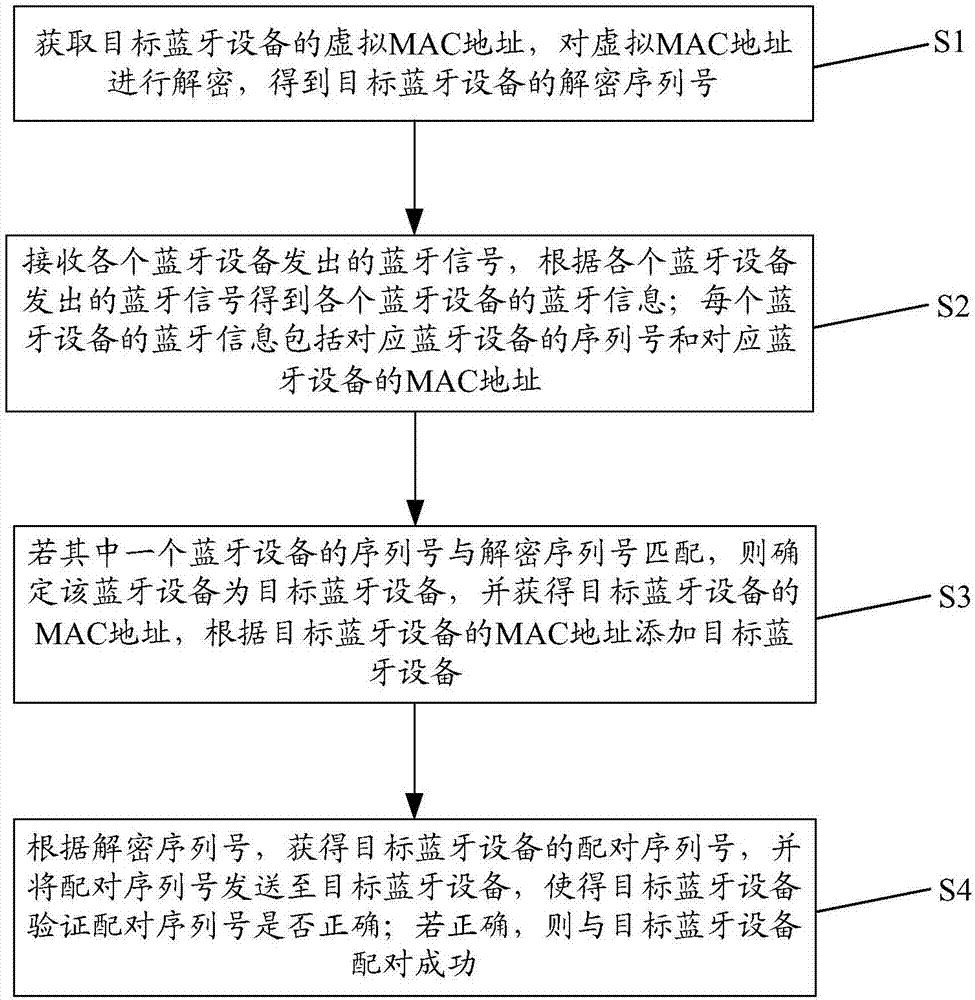
InactiveCN107071699ANot easy to getNot easy to decipherConnection managementWireless commuication servicesComputer terminalMedia access control
The invention discloses a Bluetooth device addition method and system, relates to the technical field of wireless communication and solves the technical problem that the security of transmitting information between terminals and Bluetooth devices is relatively low. The Bluetooth device addition method comprises the steps of obtaining a virtual MAC (Media Access Control) address of a target Bluetooth device and decrypting the virtual MAC address, thereby obtaining a decryption serial number of the target Bluetooth device; receiving Bluetooth signals sent by various Bluetooth devices and obtaining Bluetooth information of the various Bluetooth devices according to the Bluetooth signals sent by the various Bluetooth devices, wherein the Bluetooth information of each Bluetooth device comprises the serial number and MAC address of the corresponding Bluetooth device; and if the serial number of one Bluetooth device matches the decryption serial number, determining that the Bluetooth device is the target Bluetooth device, obtaining the MAC address of the target Bluetooth device and adding the target Bluetooth device according to the MAC address of the target Bluetooth device. The method and the system are applied to addition of the Bluetooth device.
Owner:ENN SCI & TECH DEV
Resource processing method, electronic equipment and server
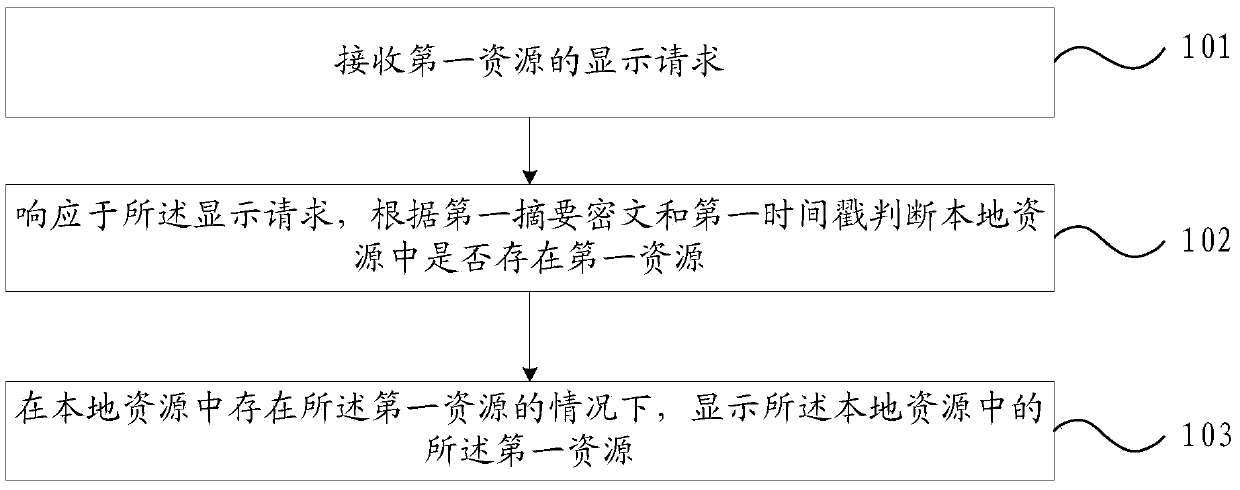
ActiveCN111488600AEasy to useAvoid duplicate downloadsDigital data protectionSpecial data processing applicationsCiphertextTimestamping
The embodiment of the invention provides a resource processing method and electronic equipment. The method comprises the following steps: receiving a display request of a first resource; in response to the display request, judging whether a first resource exists in local resources or not according to a first abstract ciphertext and a first timestamp; under the condition that the first resource exists in the local resources, displaying the first resource in the local resources, wherein the first abstract ciphertext is an abstract ciphertext generated by encrypting a channel number of a first application, and the first application is an application corresponding to the display request. According to the invention, whether the to-be-displayed first resource exists in the local resource can beaccurately identified.
Owner:南京维沃软件技术有限公司
Compression and decompression method of 3D mesh model
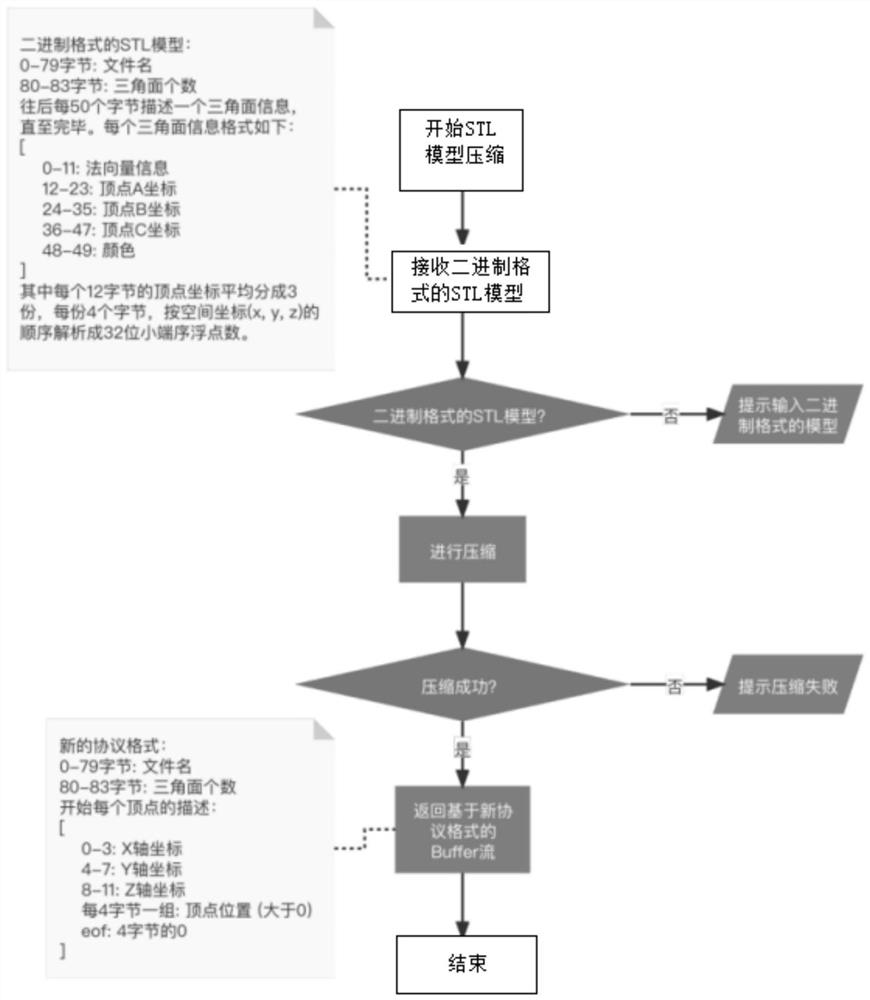
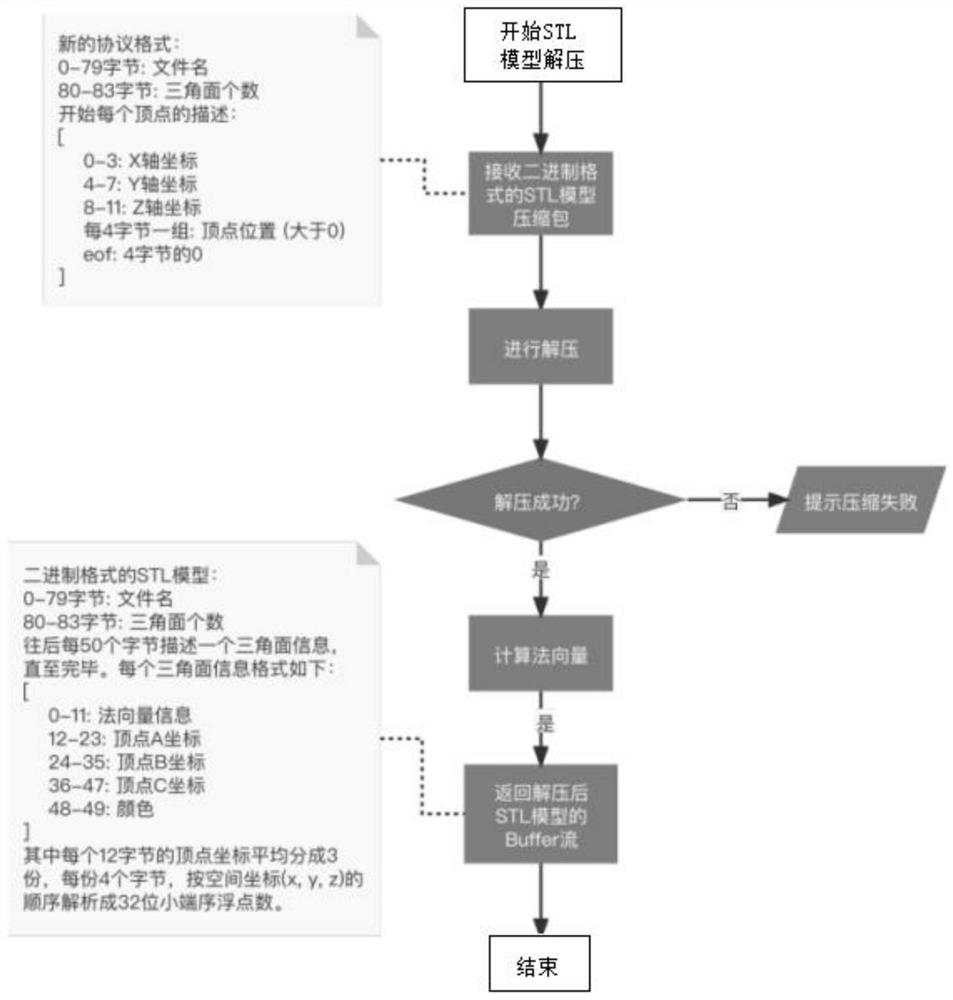
PendingCN114693817AStructure without distortionImprove data transfer efficiencyImage codingParallel computingData transmission
The invention belongs to the technical field of 3D mesh model compression, and particularly discloses a 3D mesh model compression and decompression method, and the compression method comprises the steps: obtaining an STL model in a binary format, and converting the STL model into a Buffer stream; file information of 0-83 bytes is reserved, 0-79 bytes are file names, and 80-83 bytes are triangular facets; processing the triangular facet information of every 50 bytes behind the 83th byte; after each triangular surface is processed, a new Buffer stream based on a new protocol format is returned, and the 0th to 83th bytes of the new Buffer stream are file information; the information of each vertex is separated by using 0 of 4 bytes; and if S1-S4 are not successful, prompting that the compression fails. By using a novel STL storage protocol, the compressed STL model occupies a smaller bandwidth during transmission; the device is not easy to decode when being intercepted on a transmission pipeline; and the space of the server is saved. The STL model data transmission efficiency and security are improved; an existing medical scene is matched; and the model structure is not distorted after pressurization and decompression.
Owner:PERCEPTION VISION MEDICAL TECH CO LTD +1
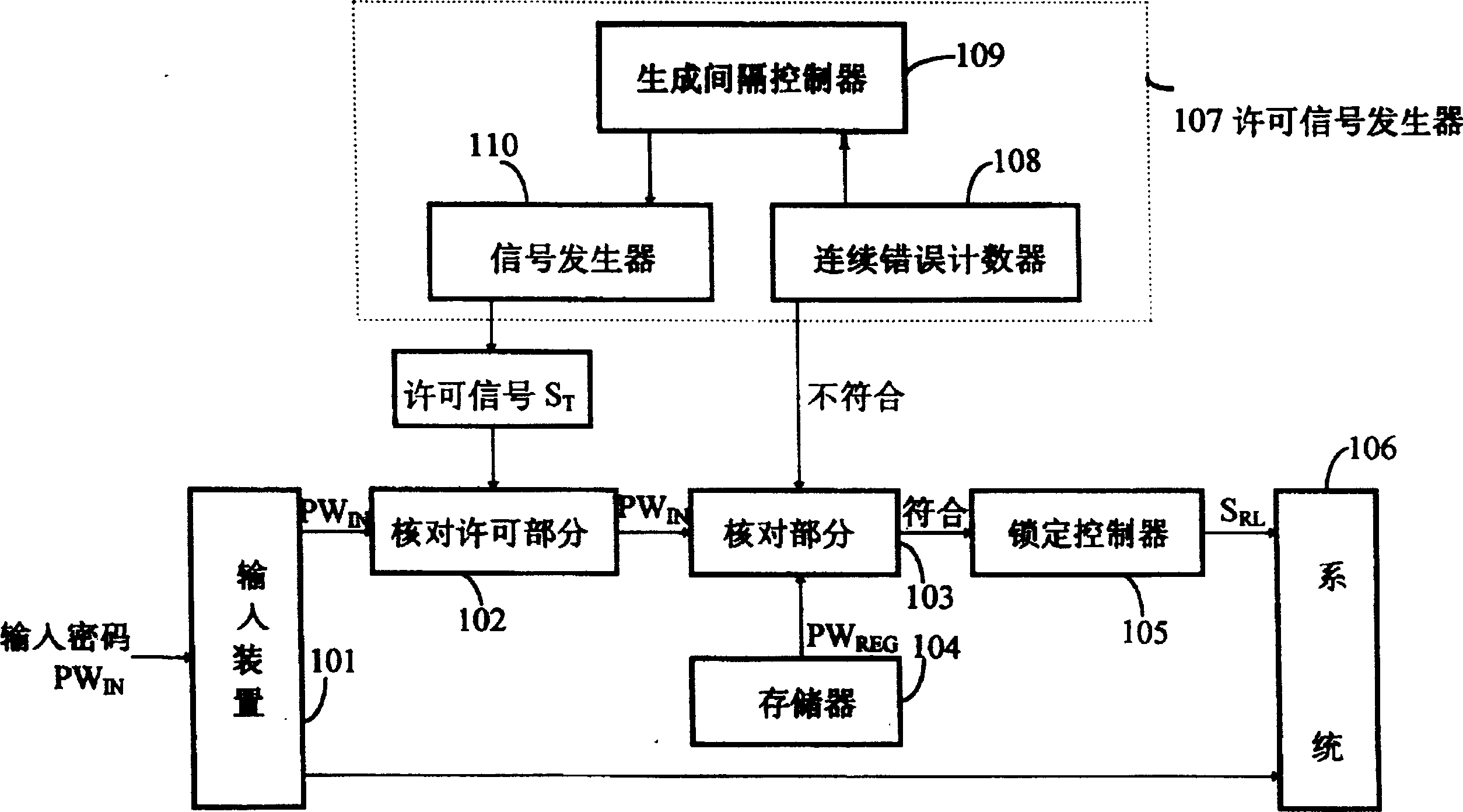
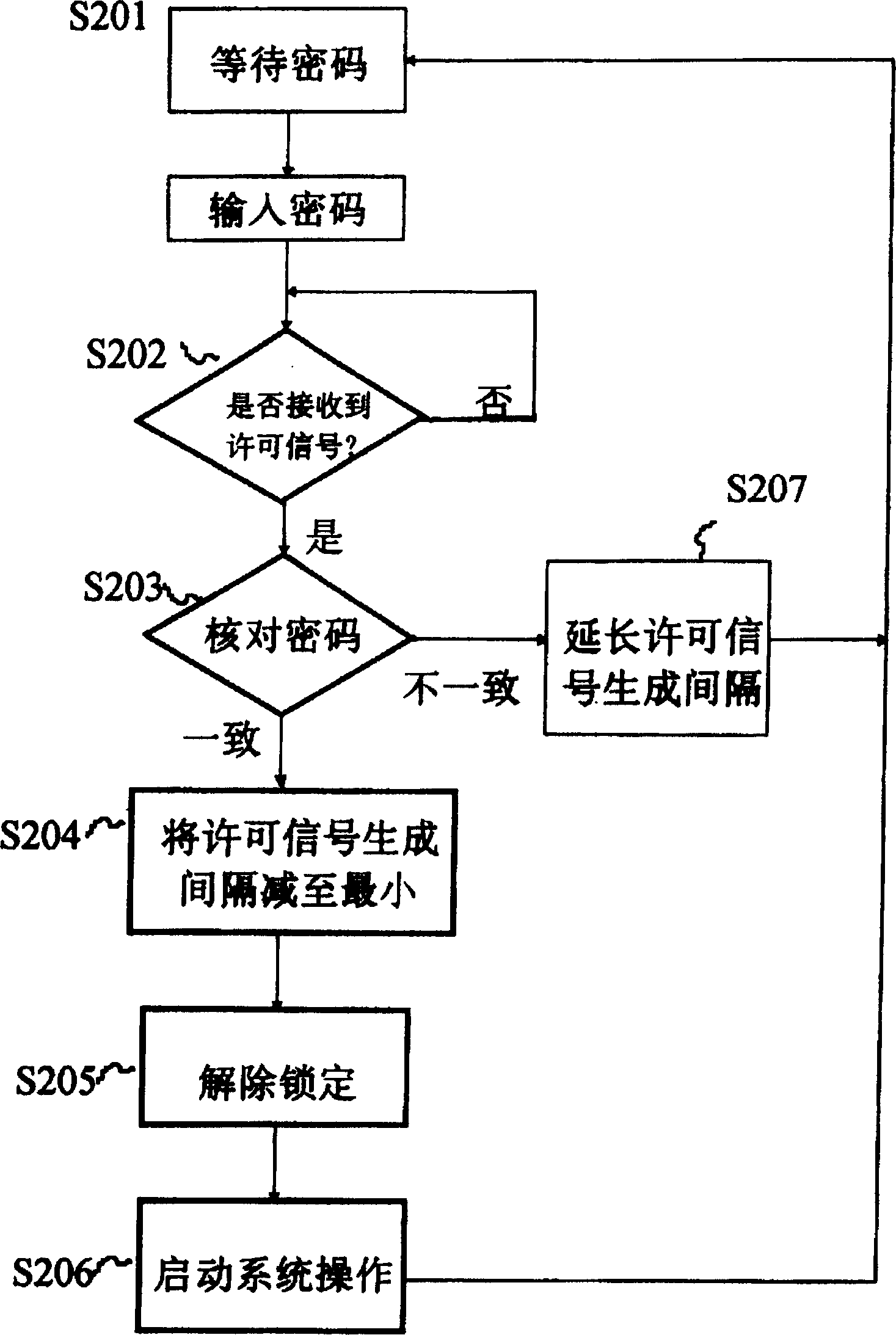
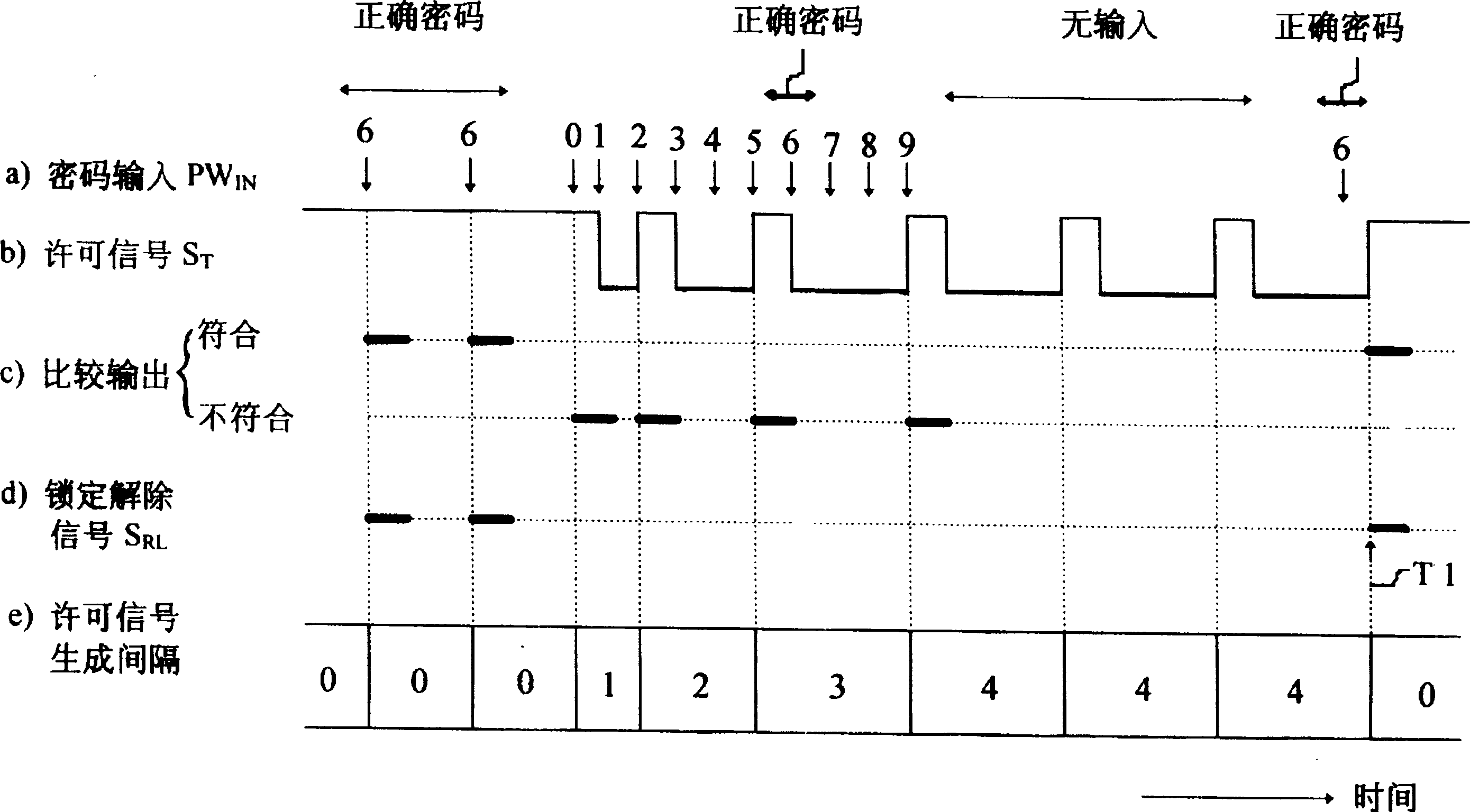
Secret information identification system
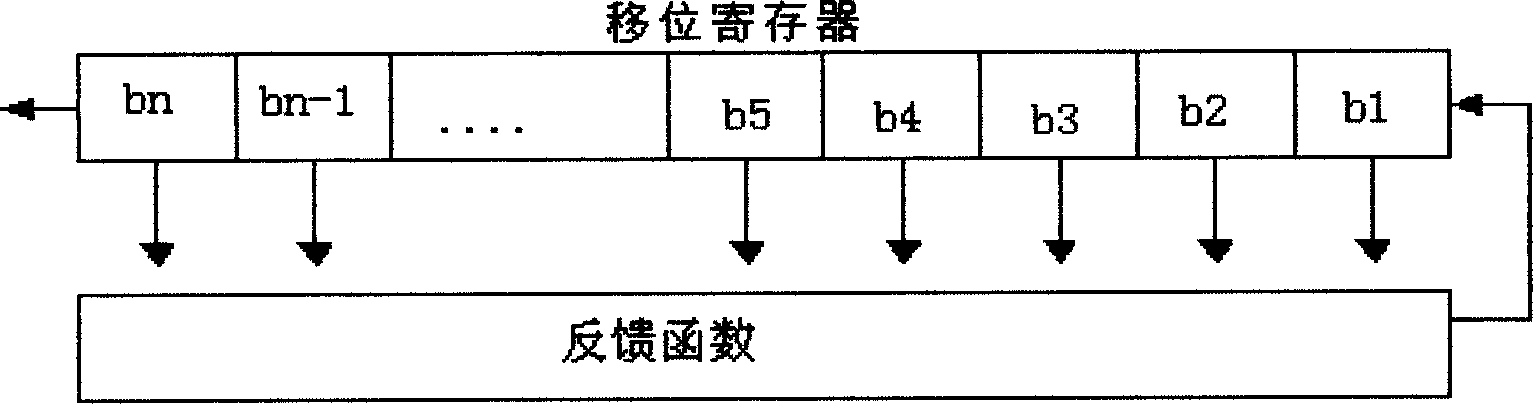
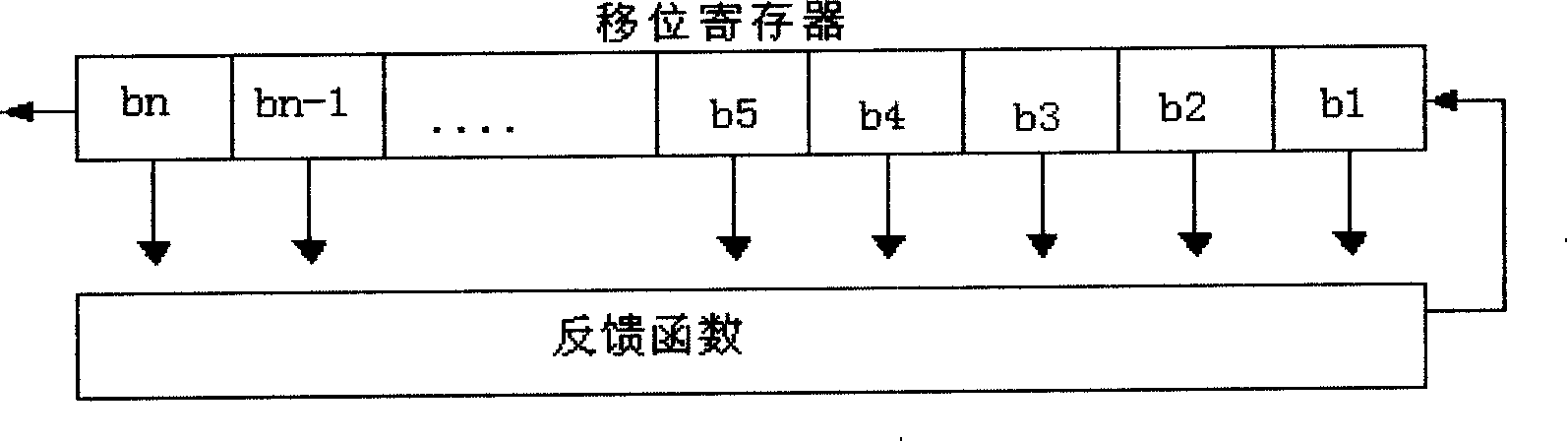
In a secret information identification system, an input password (PWIN) is compared with a registered password (PWREG) every time a permission signal (ST) is generated. Lock release permission is given when a comparison result (SCOMP) indicates coincidence. Alternatively, an input password is compared with a registered password and lock release permission is given every time a permission signal is generated when the comparison indicates coincidence. The cycle of generation of the permission signal is elongated as the number of events of non-coincidence in comparison results increases. As a result, the password is not easily broken, and further the password input function is not locked even after input of a wrong password.
Owner:NEC CORP
A Distributed Encryption Storage and Authentication Method Based on Local Area Network
ActiveCN105791274BEffective distributed encrypted storagePrevent leakageTransmissionArea networkEncryption
The invention discloses a distributed encrypted storage and authentication method based on a local area network. The encrypted storage method disclosed by the invention comprises the steps that a distributed management module segments information according to a certain rule, generates a random code based on each segment, carries out weighted confusion based on the segment information, a segment number and the generated random code, and randomly releases the obtained information to a database storage server; and an encryption module encrypts segmented weighting information in a random encryption mode, and then stores the segmented weighting information in a database by a storage module. The authentication method disclosed by the invention is used for carrying out authentication based on the encrypted storage method, and the principle of the authentication method is to carry out segmented encryption on the information again, and then compare the information with actually stored information to judge whether the authentication is successful. The distributed encrypted storage and authentication method disclosed by the invention has the beneficial effects that sensitive information of a user can be effectively stored in a distributed encrypted storage mode to avoid the leakage of all information resulting from the capture of a single storage server.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Anti-counterfeiting pen and anti-counterfeiting mark
InactiveCN102289654ALow priceNot easy to decipherRecord carriers used with machinesSensing by electromagnetic radiationInternet privacyEngineering
The invention relates to an anti-counterfeit technology and an anti-counterfeit device, in particular to an anti-counterfeit pen and an anti-counterfeit label. When the anti-counterfeit label is arranged on printing money, an entrance ticket, a moon cake ticket, an identification card, a driving license, a famous tobacco, a famous wine, a drug, a health care product, furniture, clothing, shoes and hats, the anti-counterfeit pen can tell the authenticity of products in a visual and readable way by pointing the anti-counterfeit label. The anti-counterfeit pen comprises a shell which is internally provided with a photoelectric sensor recognizing anti-counterfeit coding information, a mother board, a power source and an anti-counterfeit information output unit; a signal output end of the photoelectric sensor recognizing the anti-counterfeit coding information is connected with a signal input end of the mother board with the functions of information identification, information comparison and judgment and anti-counterfeit signal output; and the anti-counterfeit signal output end is connected with the anti-counterfeit information output unit. The anti-counterfeit label comprises a label bottom layer, an anti-counterfeit coding layer and a pattern layer. The anti-counterfeit pen and the anti-counterfeit label mainly solve the problem that the existing anti-counterfeit technology is not easy to operate by a user due to wide varieties and are beneficial to the unification of the anti-counterfeit technology.
Owner:黄丽娜
Key smart anti-theft alarm
InactiveCN103839317BEasy to operateMany internal codesIndividual entry/exit registersAlarm locksElectric machineThe Internet
The invention discloses a key intelligent anti-theft alarm. A circuit board and a buzzer are installed in a shell cavity formed by an upper shell and a lower shell to form an alarm. Six wires are drawn from the lower side of the shell, including a 48V power line, a ground Wire, electric door lock wire, motor rotation detection wire, 125K antenna coil, the RFID technology added to the Internet of Things in this invention makes the identity of the key unique and has no repeated code value. Even if it is copied by others, it also cannot open the lock. The opening rate is zero, and at the same time, an alarm sound is issued to deter the opener, making them afraid to approach, bringing us safe and fast enjoyment.
Owner:淮安市金恒泰科技有限公司
Non-contact unlocking method for mobile terminal
ActiveCN103853457BImprove experienceNot easy to decipherInput/output processes for data processingPasswordContact method
The present invention provides a non-contact unlocking method for a mobile terminal. The method includes: making the mobile terminal enter the state to be unlocked, and determining the starting point of the unlocking input; continuously receiving the user's unlocking input to the mobile terminal, and passing the direction of the sensor Change record the track point corresponding to the unlocking input process; determine the end point of the unlocking input to form an unlocking track in the air; identify the unlocking track and convert it into an unlocking password; compare it with the unlocking password preset by the mobile terminal, if If the match is successful, the mobile terminal enters the unlocked state. By providing the non-contact unlocking method, the present invention enables the user to use a hand-held mobile terminal to draw an unlocking pattern in the air to unlock. The advantage is that no scratches are generated during the unlocking process, the password is not easy to be deciphered, and the unlocking is convenient and reliable without restrictive conditions, which improves the user experience.
Owner:PHICOMM (SHANGHAI) CO LTD
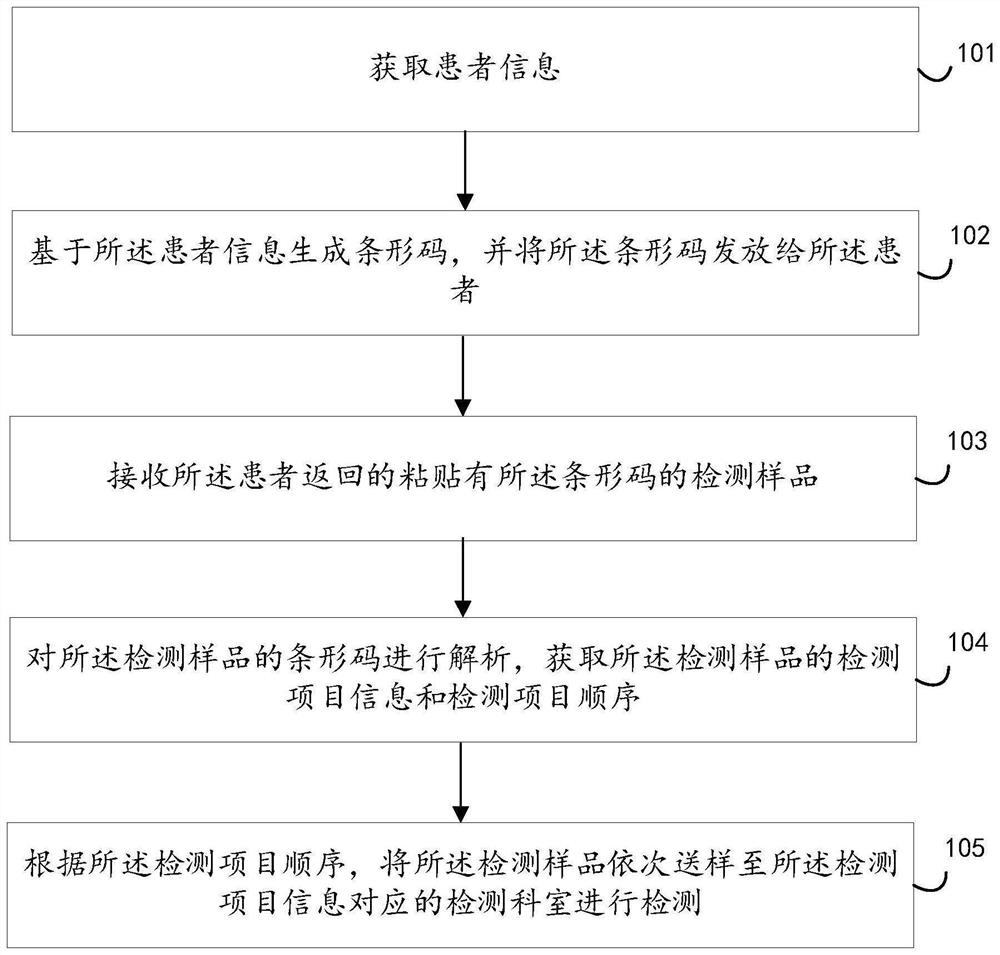
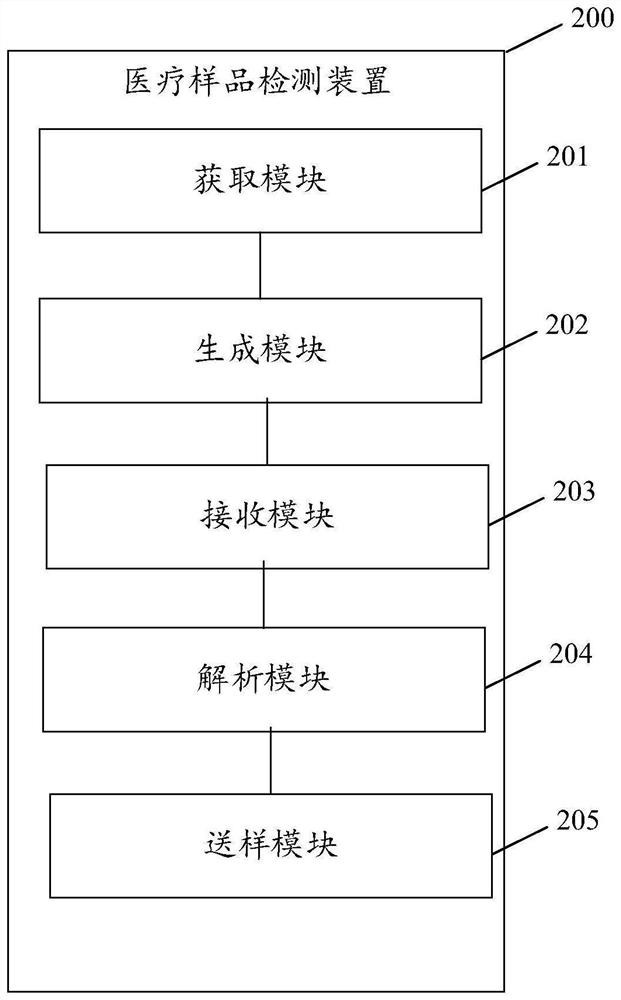
Medical sample detection method and device, electronic equipment and storage medium
PendingCN114783556AAvoid Privacy LeakageNot easy to decipherCharacter and pattern recognitionRecord carriers used with machinesComputer hardwarePatient need
The invention discloses a medical sample detection method and device, electronic equipment and a storage medium. The method comprises the following steps: acquiring patient information, wherein the patient information comprises a patient face image, detection item information and a detection item sequence; generating a bar code based on the patient information, and issuing the bar code to the patient; receiving a detection sample which is returned by the patient and is pasted with the bar code; analyzing the bar code of the detection sample to obtain detection item information and a detection item sequence of the detection sample; and according to the sequence of the detection items, sequentially sending the detection samples to the detection departments corresponding to the detection item information for detection. By adopting the scheme provided by the invention, all the detection samples of the patient can be obtained at one time according to the detection items of the patient, and the detection samples are sequentially sent to the corresponding detection departments based on the detection item information and the detection item sequence, so that the tedious process that the patient needs to go to each detection department one by one for detection is avoided.
Owner:长沙桃子卫健信息科技有限公司
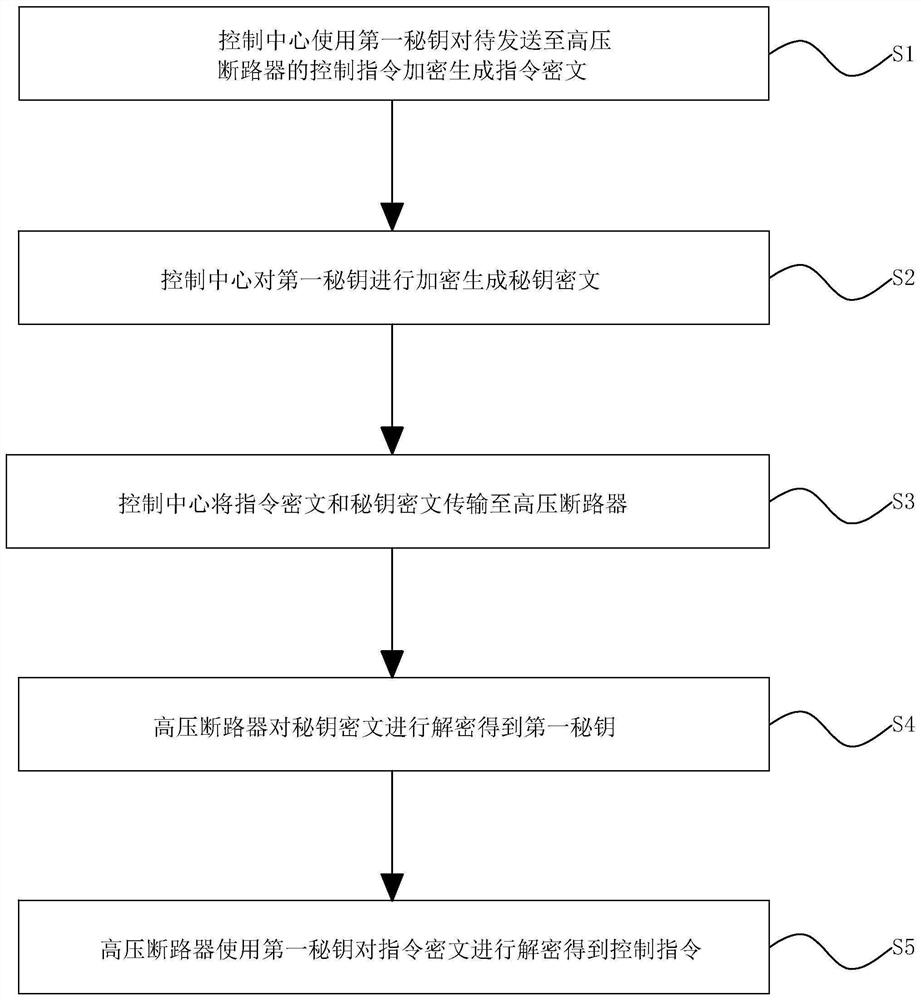
Remote control instruction transmission method for high-voltage circuit breaker
ActiveCN113487851APrevent malicious tamperingProtect normal opening and closingKey distribution for secure communicationTransmission systemsCiphertextRemote control
The invention discloses a remote control instruction transmission method for a high-voltage circuit breaker. The method comprises the following steps that S1, a control center encrypts a control instruction to be sent to a high-voltage circuit breaker by using a first secret key to generate an instruction ciphertext; S2, the control center encrypts the first secret key to generate a secret key ciphertext; S3, the control center transmits the instruction ciphertext and the secret key ciphertext to the high-voltage circuit breaker; S4, the high-voltage circuit breaker decrypts the secret key ciphertext to obtain a first secret key; and S5, the high-voltage circuit breaker decrypts the instruction ciphertext by using the first secret key to obtain the control instruction. According to the invention, the control instruction transmitted from the control center to the high-voltage circuit breaker is subjected to double encryption, so that the control instruction is prevented from being maliciously tampered in the transmission process, normal opening and closing of the high-voltage circuit breaker are protected, and normal work of a power grid is guaranteed.
Owner:ZHEJIANG UNIV OF TECH
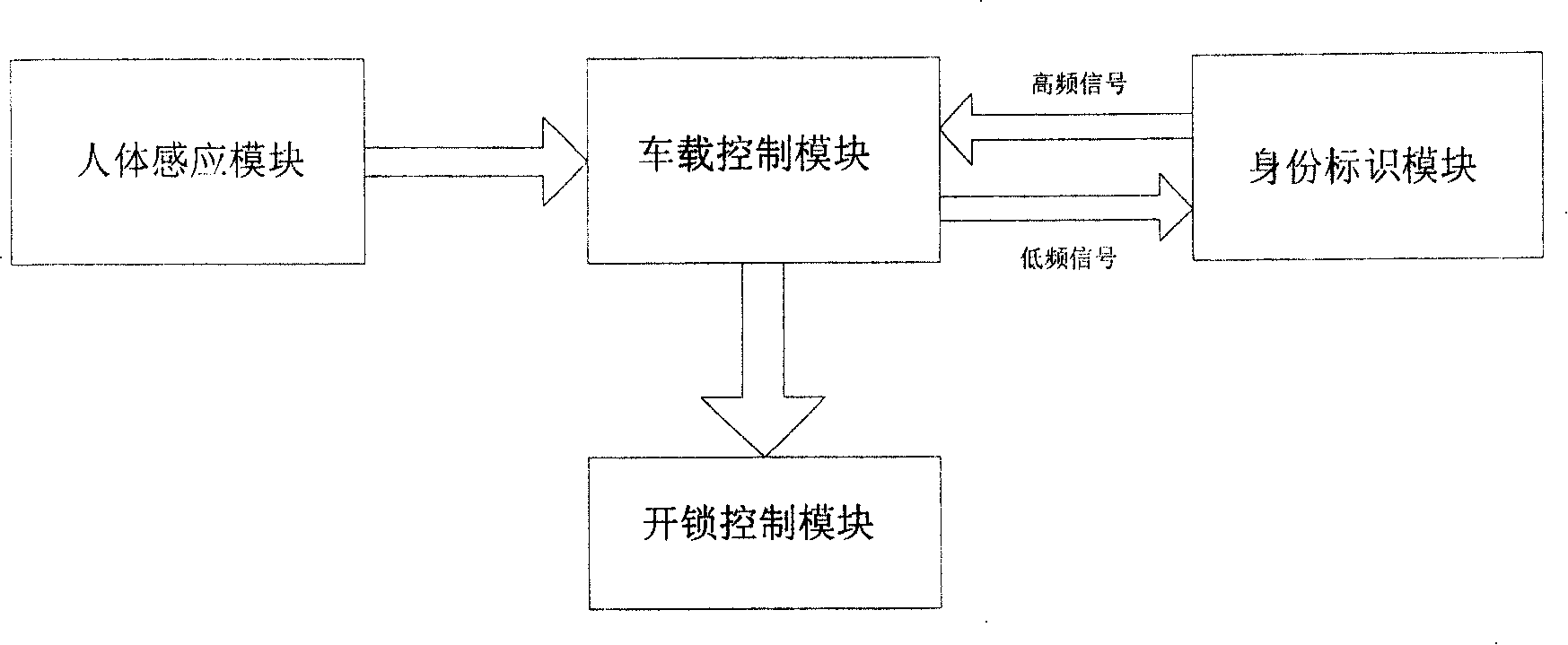
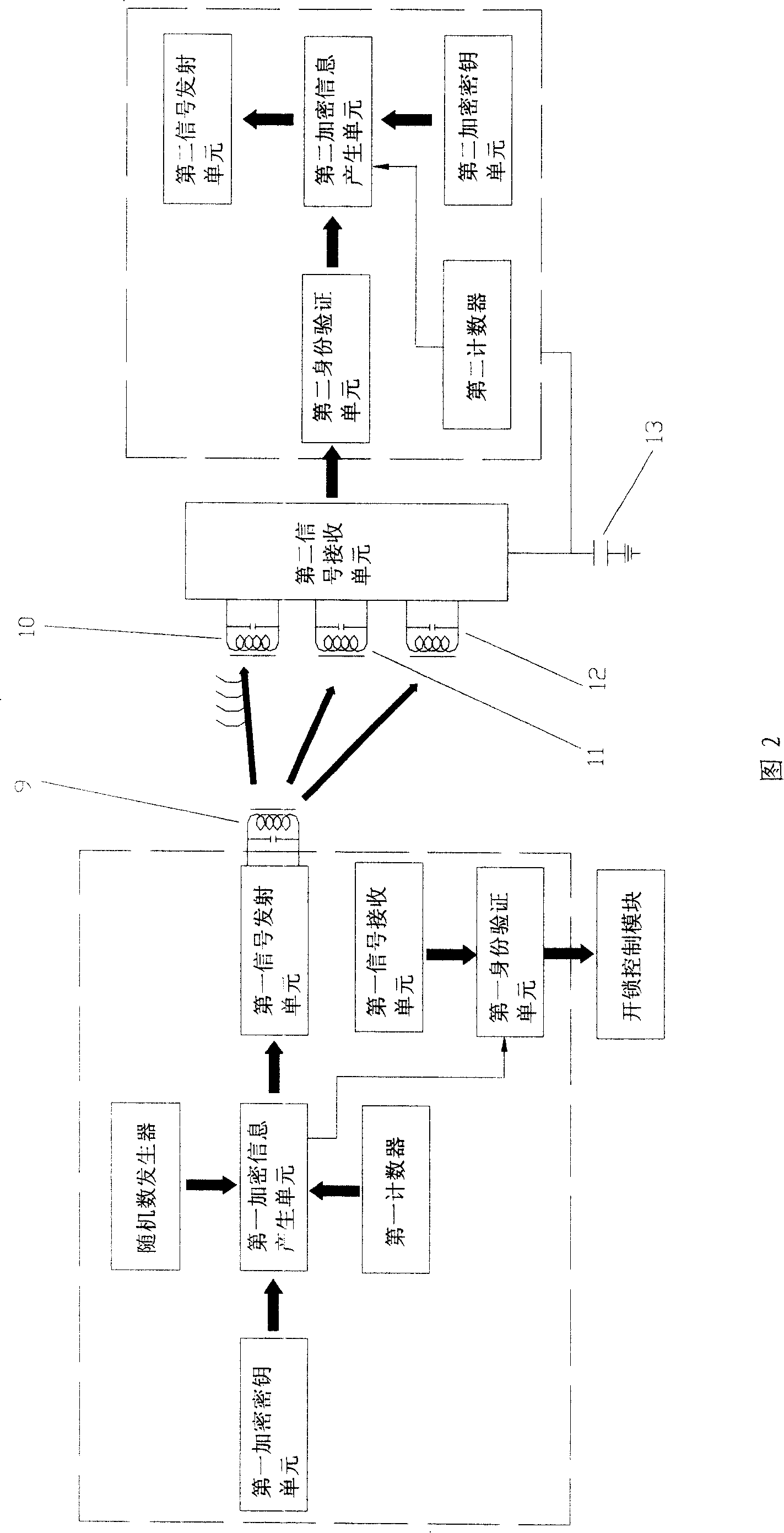
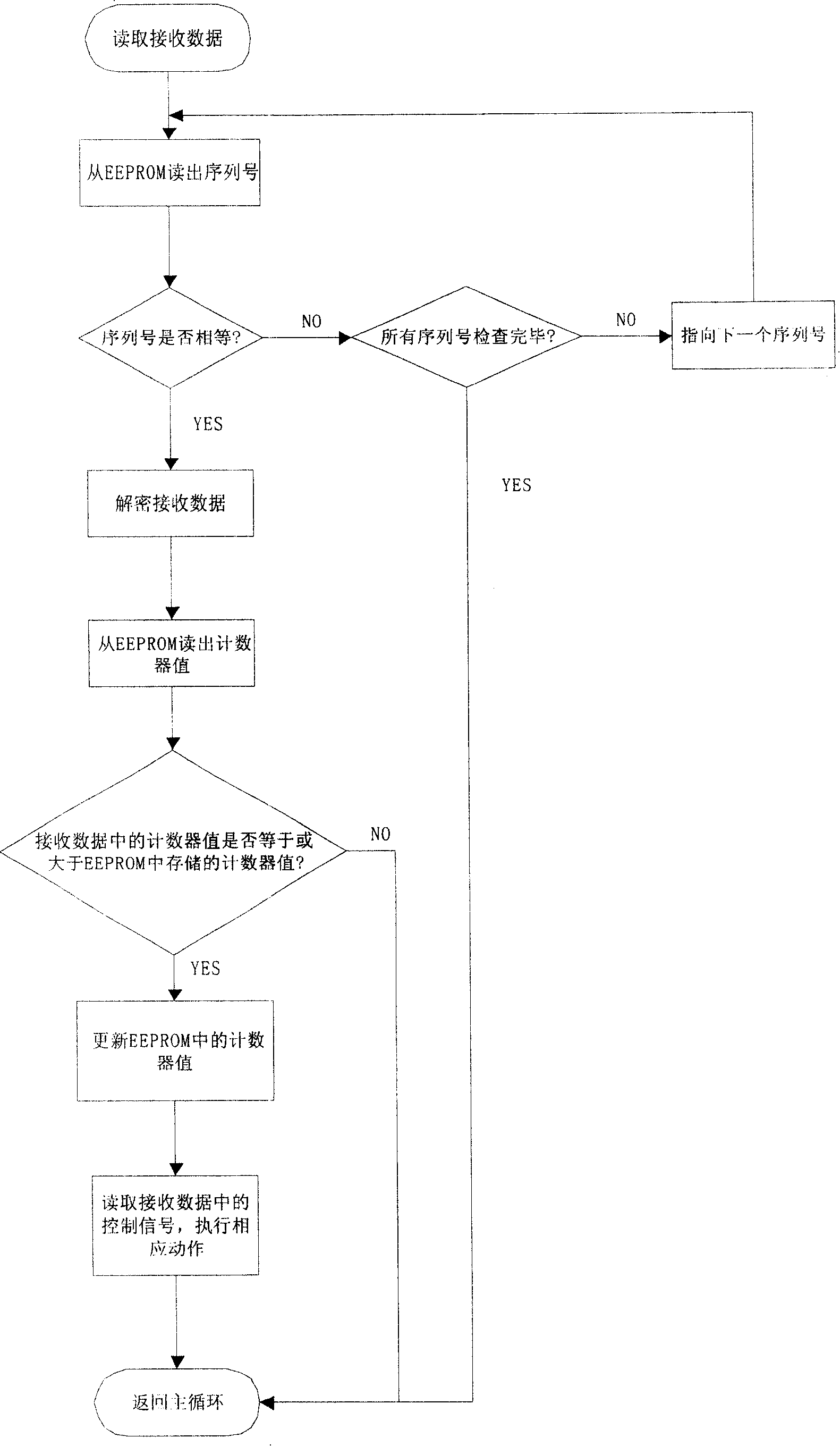
Identity recognition system for keyless entering automobile and its recognition method
ActiveCN100382099CNot easy to decipherAvoid collisionMultiple keys/algorithms usageCo-operative working arrangementsIdentity recognitionComputer module
The invented identity identification system includes car-mounted control module, identity identification module and unlocking control module. Its identity identification method includes the following steps: car-mounted control module can produce first encrypted information produced by using first encrypted key, serial number, random data and instantaneous data rolling code of counter and transmit the signal with first encrypted information; the identity identification module can be used for receiving said signal to make identity identification, producing second encrypted information produced by using first encrypted information and second encrypted key and transmitting the feedback signal with second encrypted information; the car-mounted control module can be used for receiving said feedback information, making identity identification and controlling unlocking control module to execute unlocking operation.
Owner:BYD CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com