Identity recognition system based on a computer network
A computer network and identity recognition technology, applied in the field of identity recognition, can solve the problems of easy to be stolen or deciphered, low security factor of passwords, cumbersome passwords, etc., to achieve the effect of not easy to steal or decipher, and high security factor
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The technical solutions in the embodiments of the present invention will be clearly and completely described below in conjunction with the drawings in the embodiments of the invention, but it should be understood that the protection scope of the present invention is not limited by the specific embodiments.
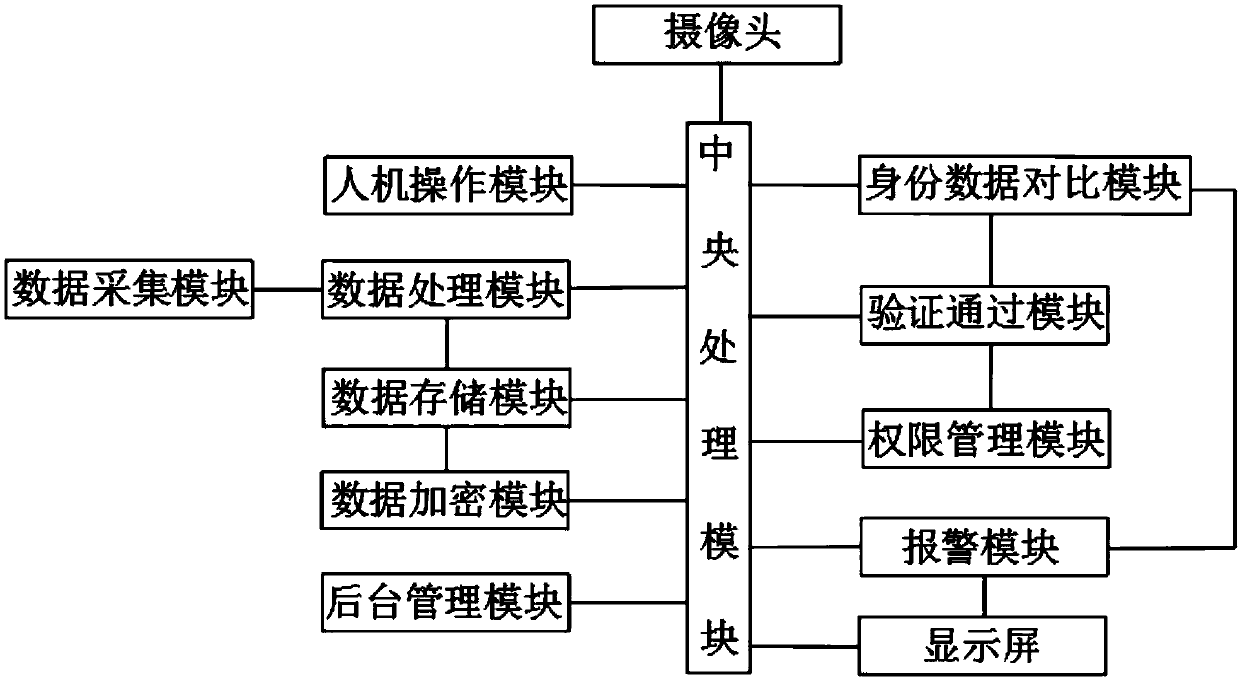
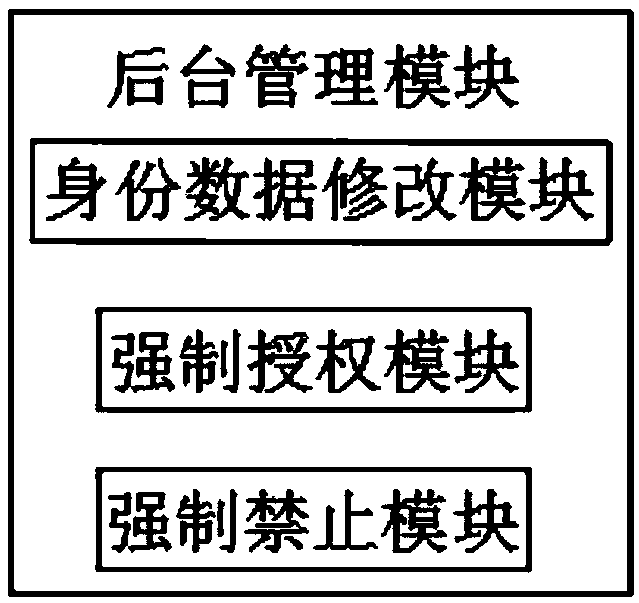
[0025] refer to Figure 1-4 , the present invention provides a computer network-based identification system, comprising:
[0026] The man-machine operation module is used to obtain the instruction data input by the operator and send it to the central processing module;
[0027] The camera is used to collect the face data of the operator and send it to the central processing module for storage and post-processing.
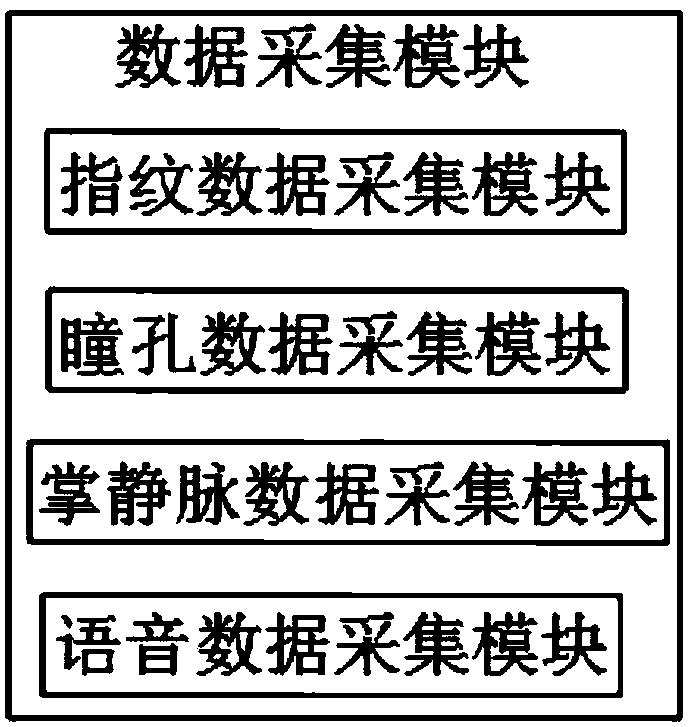
[0028] The data acquisition module is used to collect various identity verification data and send them to the data processing module, and the data processing module performs data processing after receiving various identity verification data, and sends th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com