Network and its management method
A network and management server technology, applied in the field of network and its management, can solve problems such as difficulty in interchangeable frequency band communication speed, increase of wireless LAN equipment or mutual interference of application methods, slow response, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
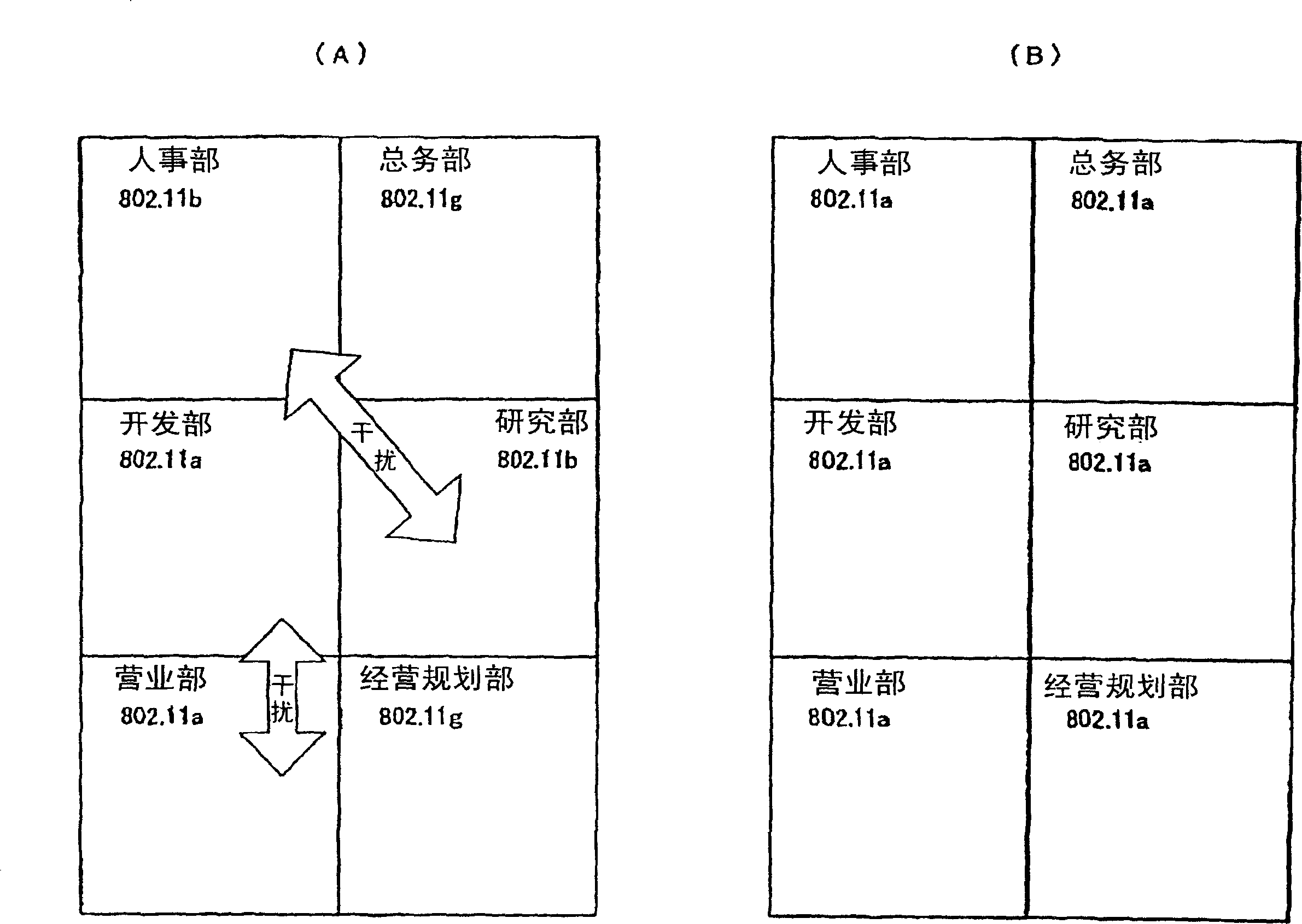
[0067] The network of Embodiment 1 employs SSID and VLAN, effectively utilizes the wireless space, communicates between the wireless terminal and the node connected to the LAN of the unit to which it belongs, and makes it set and operate as follows.
[0068] (1) An SSID is assigned to each unit that is divided.
[0069] (2) A virtual LAN (hereinafter abbreviated as 'VLAN') is assigned to each divided unit.
[0070] (3) Assign a management VLAN (for example, 'VLAN2') to the management server.
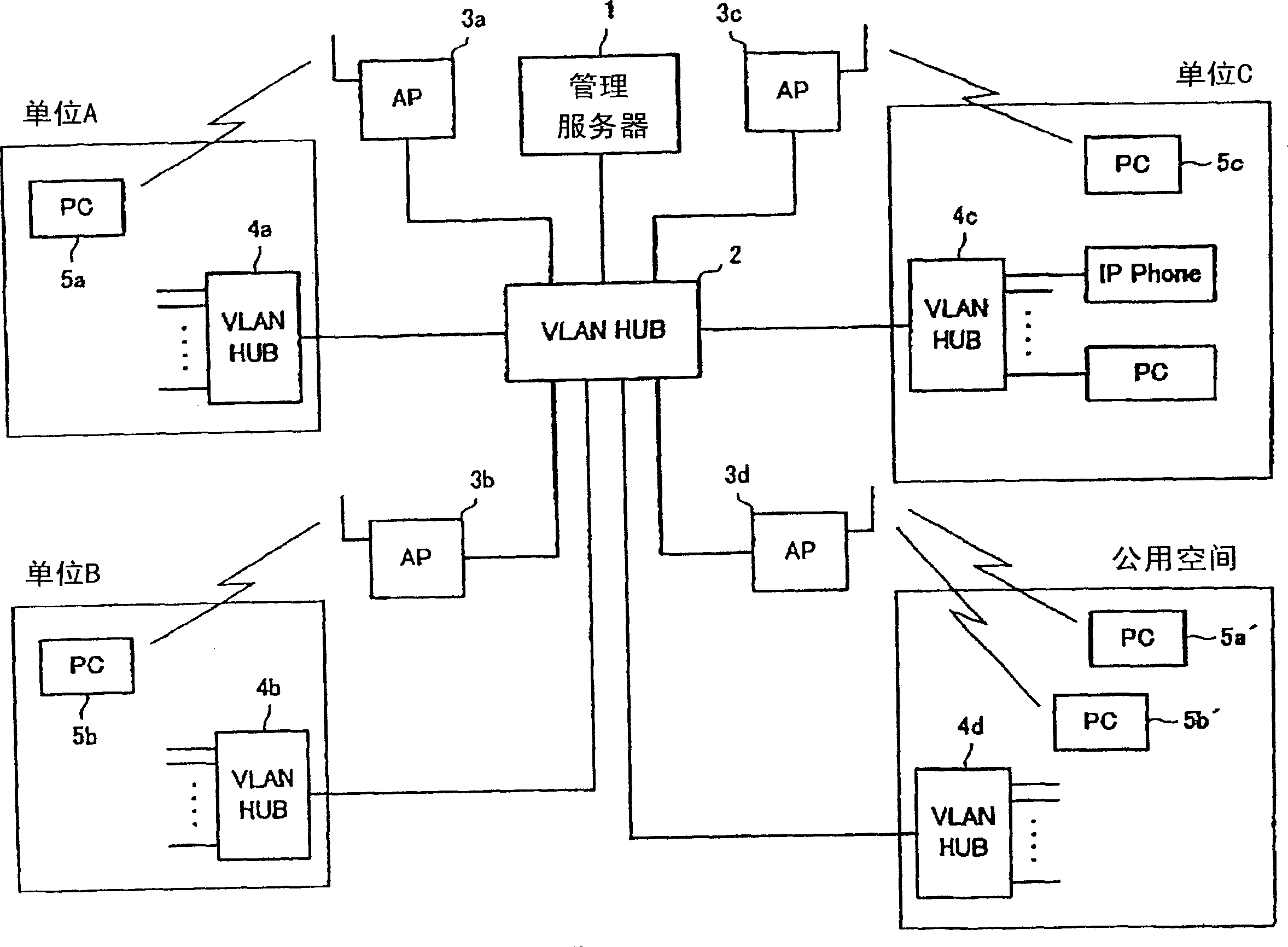
[0071] (4) Build a backbone LAN for wireless LAN.
[0072] A wireless access point (hereinafter abbreviated as 'AP') is installed together on a wired communication network for a wireless LAN that can recognize a VLAN tag. AP is not bound by unit, and can be configured and set for wireless communication with the best communication quality.
[0073] (5) The wired LAN and wireless LAN of each unit are connected with the backbone LAN.
[0074] The connection point of the backbone LAN for...
Embodiment approach 2
[0114] The network according to Embodiment 2 is a combination of user authentication based on IEEE802.1X and VLAN. Therefore, it is set and operated as follows.
[0115] (1) An SSID is assigned to each divided unit.
[0116] (2) A virtual LAN (hereinafter abbreviated as 'VLAN') is assigned to each divided unit.
[0117] (3) Assign a management VLAN (for example, 'VLAN2') to the management server.
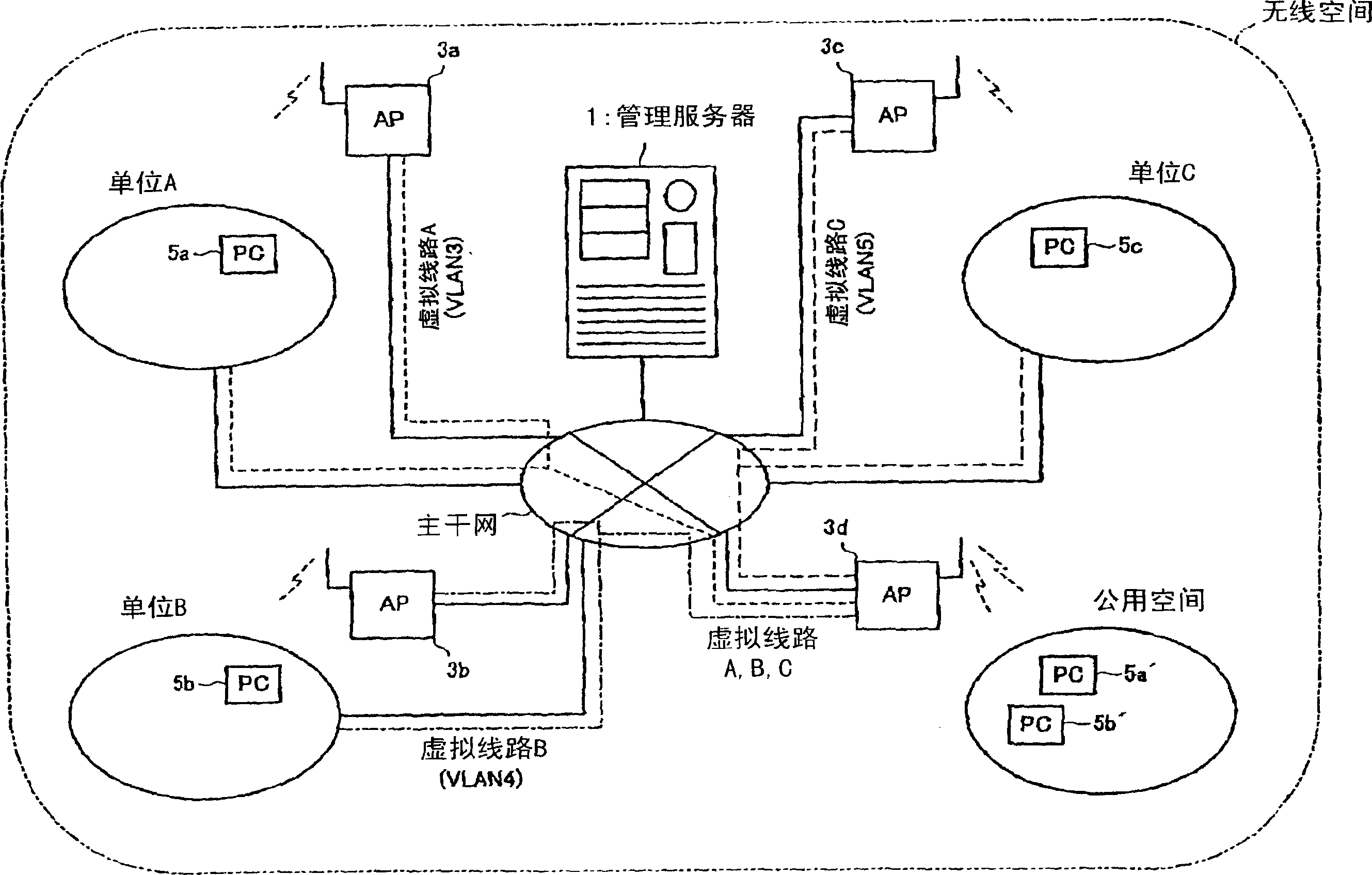
[0118] (4) Build a backbone LAN for wireless LAN.
[0119] A wireless access point (hereinafter abbreviated as 'AP') is installed together on a wired communication network for a wireless LAN that can recognize a VLAN tag. Even if it is installed in each unit and in a common space, it is installed in the same way. AP is not bound by unit, and can be configured and set for wireless communication with the best communication quality.
[0120] (5) The wired LAN and wireless LAN of each unit are connected with the backbone LAN.
[0121] The connection point of the backbone LAN for w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com